Hello everyone is glad that I was able to get here. We are playing a little with syspass, but we have a problem
Connection error (BIND).
LDAP ERROR: Can not contact LDAP server (-1)
LDAP DN: syspass
I do not how I can not figure out what’s wrong, but I’ve been through a lot of options:
- I was trying to specify FQDN and ip server name
- The user is specified without prefixes simply Administrator (Domain Administrator in Active Directory)
- I checked telnet access to ldap server
- I tried to specify the server with all the possible prefixes ldap. *, Ldap: \
But I’m getting this error. I want to know in addition to installing php56w-ldap, I had to do some other setup?
Here is a screenshot of my setting
Hello everyone is glad that I was able to get here. We are playing a little with syspass, but we have a problem
Connection error (BIND).
LDAP ERROR: Can not contact LDAP server (-1)
LDAP DN: syspass
I do not how I can not figure out what’s wrong, but I’ve been through a lot of options:
- I was trying to specify FQDN and ip server name
- The user is specified without prefixes simply Administrator (Domain Administrator in Active Directory)
- I checked telnet access to ldap server
- I tried to specify the server with all the possible prefixes ldap. *, Ldap:
But I’m getting this error. I want to know in addition to installing php56w-ldap, I had to do some other setup?
Here is a screenshot of my setting
Hi I installed sysPass and everything work properly except the LDAP integration which fail.
Every time I try to test it, I get the following error:
Connection error (BIND)
LDAP ERROR : Can’t contact LDAP server (-1)
LDAP DN : cn=xxx,ou=xxxe,ou=xxx,dc=xxx,dc=xxx,dc=net,dc=xxx (masked the details)
Every time I’m tying to test, a Decryption error log is appears in /syspass.log.
I also captured the traffic and there are no packets to the active directory server.
Does anyone familiar with that issue?
Thanks,
Dor
Comments
I have a strange issue. Best part of users can login, but few can’t. That’s return wrong password and get this error:
Erreur de connexion (BIND)
LDAP ERROR: Can’t contact LDAP server (-1)
LDAP DN: CN=LDAPUSER,CN=Users,DC=MYBUSINESS,DC=local
They are all in the same LDAP folder, I didn’t specifie Group in sysPass setting.
Could be special char in password?
Hi, can you tell me if the LDAP connection changes on every login?. This is a feature that runs when a DNS hostname is given for the LDAP server. You can see it the sysPass event log.
In addition, it’s happen only in the first loggin. Once got User Disabled, that do not happen again.
Not sure what you asking for. But I juste log once with one browser and logged again in Private mode. I got this in log (Commit version: 6f44f8c):
First:
1262 2015-12-09 09:34:11 Se connecter SXXXXXXXXX ... (LDAP)
Connexion au serveur : srvdc.mybusiness.local
Utilisateur : sxxxxxxxxx
Profil : Admin
Groupe : Admins
Second:
1265 2015-12-09 09:42:18 Se connecter SXXXXXXXXX ... (MySQL)
Utilisateur : sxxxxxxxxx
Profil : Admin
Groupe : Admins
1264 2015-12-09 09:42:18 ldapBind ... Erreur de connexion (BIND)
LDAP ERROR: Can’t contact LDAP server (-1)
LDAP DN: CN=LDAP,CN=Users,DC=mybusiness,DC=local
I enabled Debug, I took a look in error.log. what display is wrong:
ldap_url_parse_ext(ldap://localhost/)
ldap_init: trying /etc/ldap/ldap.conf
ldap_init: using /etc/ldap/ldap.conf
ldap_init: HOME env is NULL
ldap_init: trying ldaprc
ldap_init: LDAPCONF env is NULL
ldap_init: LDAPRC env is NULL
ldap_create
ldap_url_parse_ext(ldap://dcfiles.mybusiness.local:389)
ldap_sasl_bind_s
ldap_sasl_bind
ldap_send_initial_request
ldap_new_connection 1 1 0
ldap_int_open_connection
ldap_connect_to_host: TCP dcfiles.mybusiness.local:389
ldap_connect_to_host: getaddrinfo failed: Nom ou service inconnu
ldap_err2string
ldap_err2string
No Ideal where that «dcfiles» is from. this is not what is set in the config file.
Seconde attemp, got:
ldap_url_parse_ext(ldap://localhost/)
ldap_init: trying /etc/ldap/ldap.conf
ldap_init: using /etc/ldap/ldap.conf
ldap_init: HOME env is NULL
ldap_init: trying ldaprc
ldap_init: LDAPCONF env is NULL
ldap_init: LDAPRC env is NULL
ldap_create
ldap_url_parse_ext(ldap://sbs2k3.mybusiness.local:389)
ldap_sasl_bind_s
ldap_sasl_bind
ldap_send_initial_request
ldap_new_connection 1 1 0
ldap_int_open_connection
ldap_connect_to_host: TCP sbs2k3.mybusiness.local:389
ldap_new_socket: 17
ldap_prepare_socket: 17
ldap_connect_to_host: Trying 192.168.0.2:389
ldap_pvt_connect: fd: 17 tm: 10 async: 0
ldap_ndelay_on: 17
attempting to connect:
connect errno: 115
ldap_int_poll: fd: 17 tm: 10
ldap_is_sock_ready: 17
ldap_is_socket_ready: error on socket 17: errno: 113 (No route to host)
ldap_pvt_connect: -1
ldap_close_socket: 17
ldap_err2string
ldap_err2string
This «sbs2k3» is from a old server removed. Maybe the issue is on my ldap server side? But the ldap still not use the right configuration from the config file.
That is the behavior that I told you, if you provide an LDAP hostname (myserver.mydomain.com) it will search for other AD servers on your domain to make auth requests.
If you only set an ip address (your AD ip address), it will not search for other servers….
OK, didn’t know that. I set a IP, Tested OK
Thanks!
Check your AD, it could you get some annoying issues with «ghost» servers…
2 participants
|
Пользователь 1944331 Посетитель Сообщений: 56 |
Доброго дня. Помогите решить задачу. Установлена последняя виртуальная машина, установил коробочную демо версию Битрикс24, пытаюсь подружить Битрикс с нашим АД. Получил от админа логин и пароль для чтения из АД, но при проверке соединения выскакивает ошибка : Ошибка соединения к серверу. В нашем домене используется шифрование. Админ говорит что нужны сертификаты. Подскажите какие и куда подсунуть сертификаты? На CentOs, Аpache, Битрикс?
Спасибо. |
||||||||||||||||||||||||||||
|
Пользователь 1944331 Посетитель Сообщений: 56 |
А можно подробней про ldaps? |
|
Александр, а причем тут это? это протокол который в административной панеле при подключении нужно указать |
|
|
Пользователь 1944331 Посетитель Сообщений: 56 |
А саму виртуалку нужно вводить в АД, чтоб получить доступ на чтение пользователей и авторизацию из АД? я уже не знаю куда копать, На CentOs, Аpache, Битрикс? В документации написано одно , по факту не работает. Вот хотел протестировать продукт… |
|
Пользователь 1944331 Посетитель Сообщений: 56 |
#6 0 17.04.2018 16:10:15
А где именно, что-то не вижу такого протокола? |
||
|
Александр, если его отметить, то скорее всего порт будет 636 |
|
|
Пользователь 1944331 Посетитель Сообщений: 56 |
Да, если выбрать SSL то будет ldaps, но это не помогает:-( Ошибка соединения к серверу. Может кроме этого, нужно еще что-то делать с CentsOS или Аpache? может к АД нужно виртуалку сначала покдлючить? Может и в этом проблема:
Помогите советом. |
||
|
Пользователь 1944331 Посетитель Сообщений: 56 |
и еще вопрос. |
|
#10 0 17.04.2018 17:50:42 Александр 1) Тип подключения — SSL |
|
|
Пользователь 1944331 Посетитель Сообщений: 56 |
#11 0 18.04.2018 09:50:00 BitrixCRM virtual appliance version 7.2.0 в «Manage sites in the pool»: Available actions: 1. Change cron tasks on site Брал с сайти виртуальную машину, коробочную версию Битрикс24 (bitrix24_encode_php5) |
|
Пользователь 136059 Гуру Сообщений: 5419 |
#12 0 18.04.2018 10:33:20
Это урезанная виртуальная машина для редакции CRM. Настоящую можно найти тут Голосуй за идеи по развитию API Bitrix: |
||
|
Пользователь 1944331 Посетитель Сообщений: 56 |
#13 0 18.04.2018 11:13:59 спасибо конечно за ссылку, но этот вариант требует подключения к Инету, а с этим проблемы на данной машине. а как же все остальные подключаются к АД, разве все так танцуют с бубном? НУ и в документации на этот счет ровно 0 описания. |
|
Пользователь 136059 Гуру Сообщений: 5419 |
#14 0 18.04.2018 13:26:45
По-поводу подключения к AD — у каждого разные тараканы и везде свои проблемы. Обычно это делает интегратор, который приходит и фиксит все быстро (относительно) и на месте. Без соответствующих доступов и компетенций это может растянуться на долго. На моей памяти самое быстрое подключение — 5 минут, самое длительное — в районе 30 дней (пришлось для клиента под его спец.AD перепиливать модуль). По-поводу SSO via NTLM (или по простому — прозрачная авторизация): насколько я знаю (а я могу ошибаться в этом вопросе) в редакции CRM не подразумевается такая возможность. Голосуй за идеи по развитию API Bitrix: |
||
|
Пользователь 1944331 Посетитель Сообщений: 56 |
#15 0 18.04.2018 17:23:54 Это все понятно, но как продукт в демо режиме пощупать то? |
|
Пользователь 136059 Гуру Сообщений: 5419 |
#16 0 18.04.2018 17:38:26
Продукт: Битрикс24.CRM на продукте BitrixCrmEnv Вы уже щупаете, но почему-то сетуете, что в нем нет фичи от Битрикс24 на BitrixEnv Голосуй за идеи по развитию API Bitrix: |
||
|
Пользователь 1944331 Посетитель Сообщений: 56 |
#17 0 19.04.2018 11:04:25 понятно, а может тогда просветите, что мне скачать, установить, для тестирования продукта «Управление заданиями и проектами»? Может я совсем не то скачал? |
|
Пользователь 1944331 Посетитель Сообщений: 56 |
#18 1 26.04.2018 15:56:31 Ха, решение оказалось на поверхности: в файле нужно было откаментить строку : TLS_CACERTDIR /etc/openldap/certs |
|
Пользователь 283877 Постоянный посетитель Сообщений: 130 |
#19 0 10.05.2018 19:42:13 После раскомментирования
перезагрузите httpd |
||
|
Пользователь 2683147 Заглянувший Сообщений: 1 |
#20 0 19.12.2019 11:26:46 Чтобы отключить проверку сертификатов ldap на машине с битрикс в файле |
|
Пользователь 1488151 Эксперт Сообщений: 290 |
#21 0 20.12.2019 05:03:37
В админке есть селектор для этого |
||
Follow through this tutorial to learn how to integrate sysPass with OpenLDAP for authentication and account management.
- Install and Setup OpenLDAP server
In our previous tutorials, we covered how to install and setup OpenLDAP server. Follow the link below to check them.
Install and Setup OpenLDAP server
- Install and Setup sysPass
Follow the link below to install and setup sysPass.
Install and setup sysPass on Linux
- Integrate sysPass with OpenLDAP for Authentication
To begin, ensure sysPass is installed with PHP-LDAP modules.
php -m | grep ldap- Create OpenLDAP User Group for sysPass
Create an group of OpenLDAP that can be used to control access to sysPass. All members of the group to be created will allowed to access/login to sysPass.
Follow our guide below to learn how to setup OpenLDAP groups.
How to Create OpenLDAP Member Groups
In our OpenLDAP server, we have created a group called syspass.
Some members have been added to this group as evident in the command output below;
ldapsearch -H ldapi:/// -Y EXTERNAL -LLL -Q -b "dc=ldapmaster,dc=kifarunix-demo,dc=com" cn=syspassSample output;
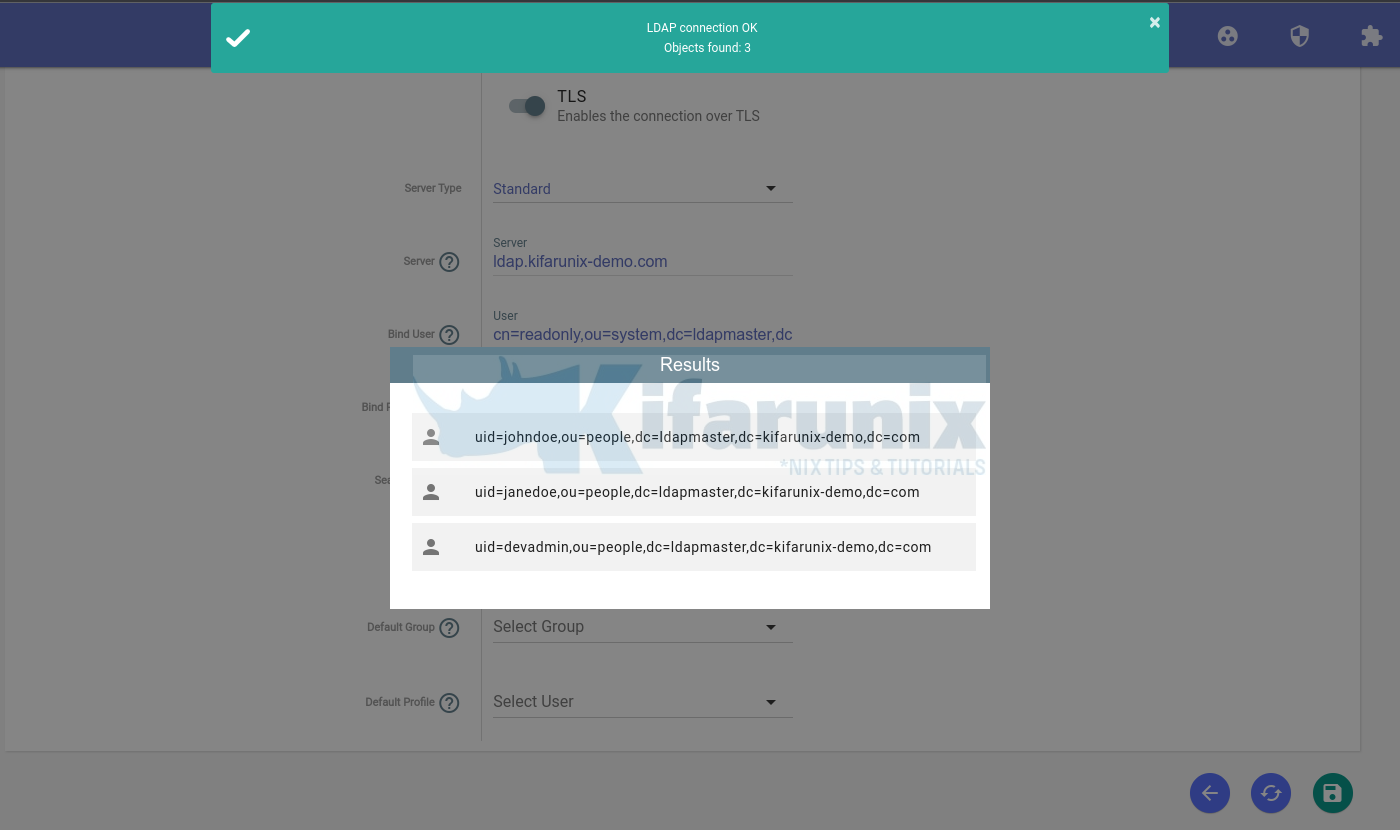
dn: cn=syspass,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com objectClass: groupOfNames cn: syspass member: uid=johndoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com member: uid=janedoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com member: uid=devadmin,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
Integrate sysPass with OpenLDAP for Authentication
Once you have setup your OpenLDAP user/groups for sysPass authentication, login to sysPass web user interface as administrator.
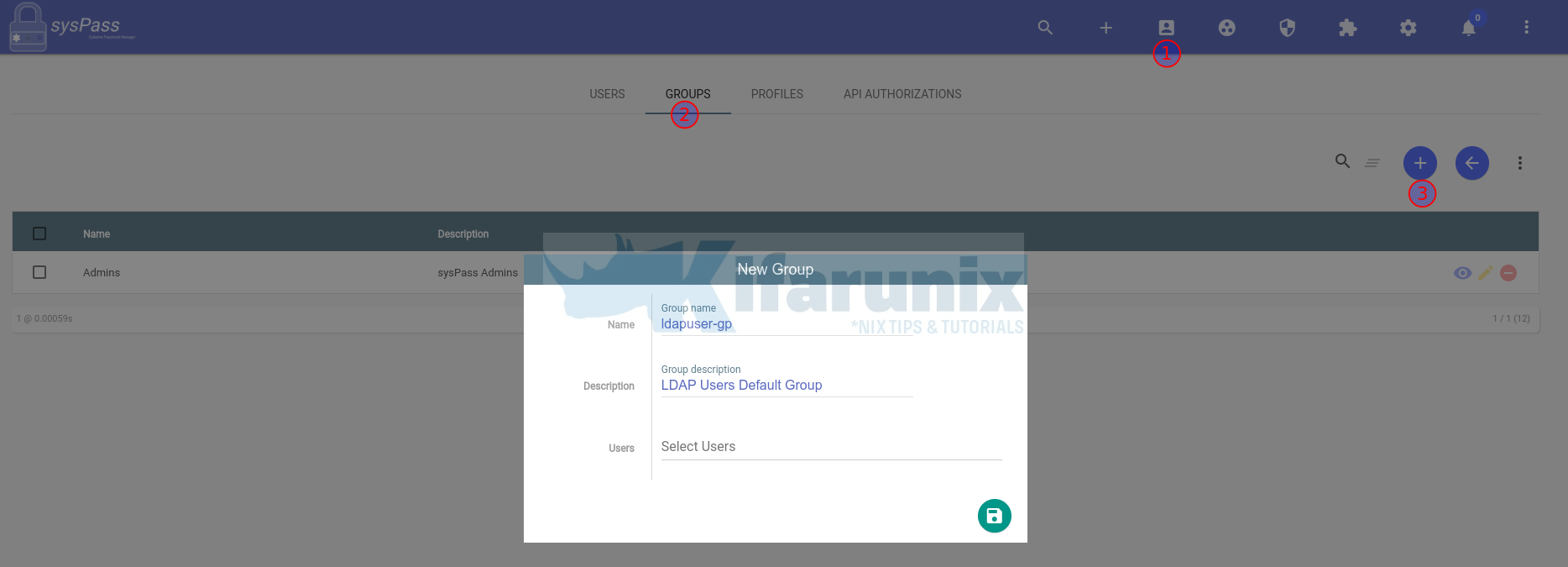
- Create OpenLDAP users group.
This will be required to specify the default group under which OpenLDAP users belong to on sysPass.
To create group, click Users and accesses icon > GROUPS > New Group.
Save the group.
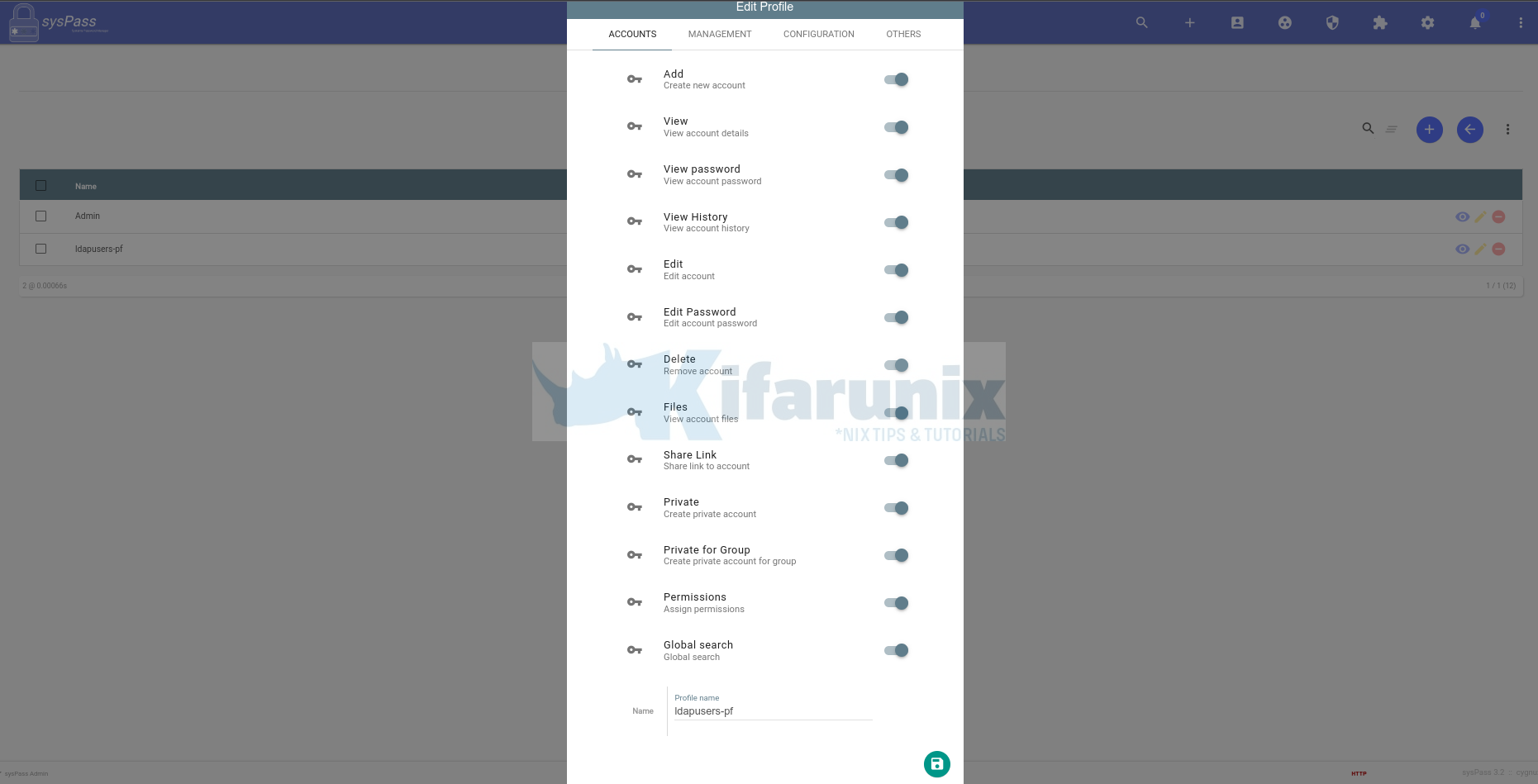
- Next, create OpenLDAP Users default Profile
This is where you define the default permissions to be assigned to a specific user profile. To create a profile, click Users and accesses icon > PROFILE > New Profile.
Sample account permissioms.
For the rest of the accesses, we didn’t give any for this particular profile. Feel Free to set the accesses accordingly.
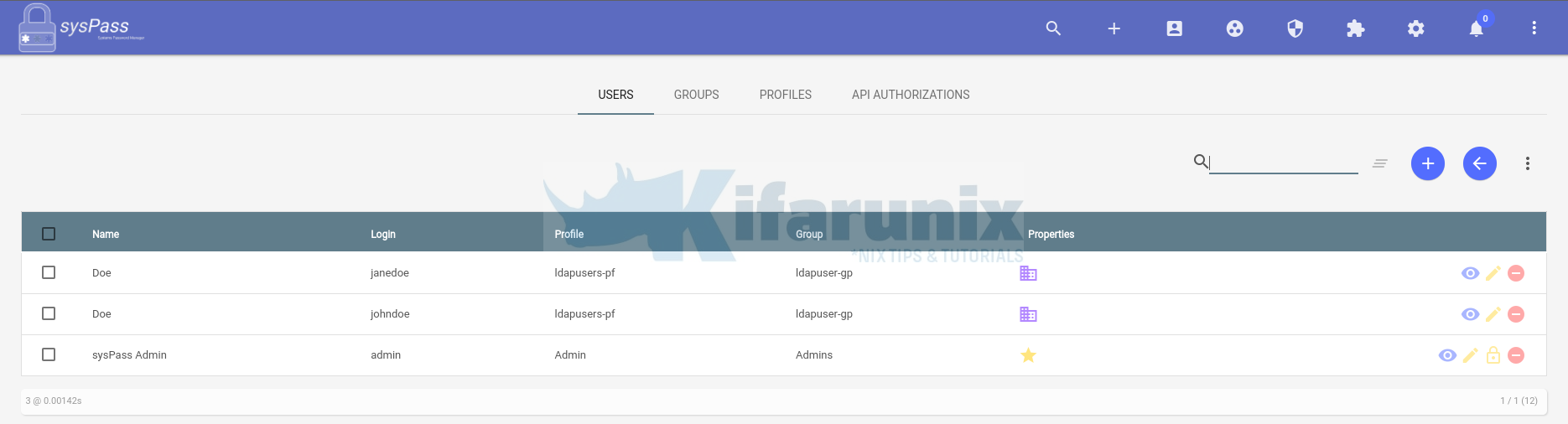
So we now have a group, ldapuser-gp, and profile, ldapusers-pf.
Note that you should be able to define the specific profile/groups once the LDAP users are in the sysPass system.
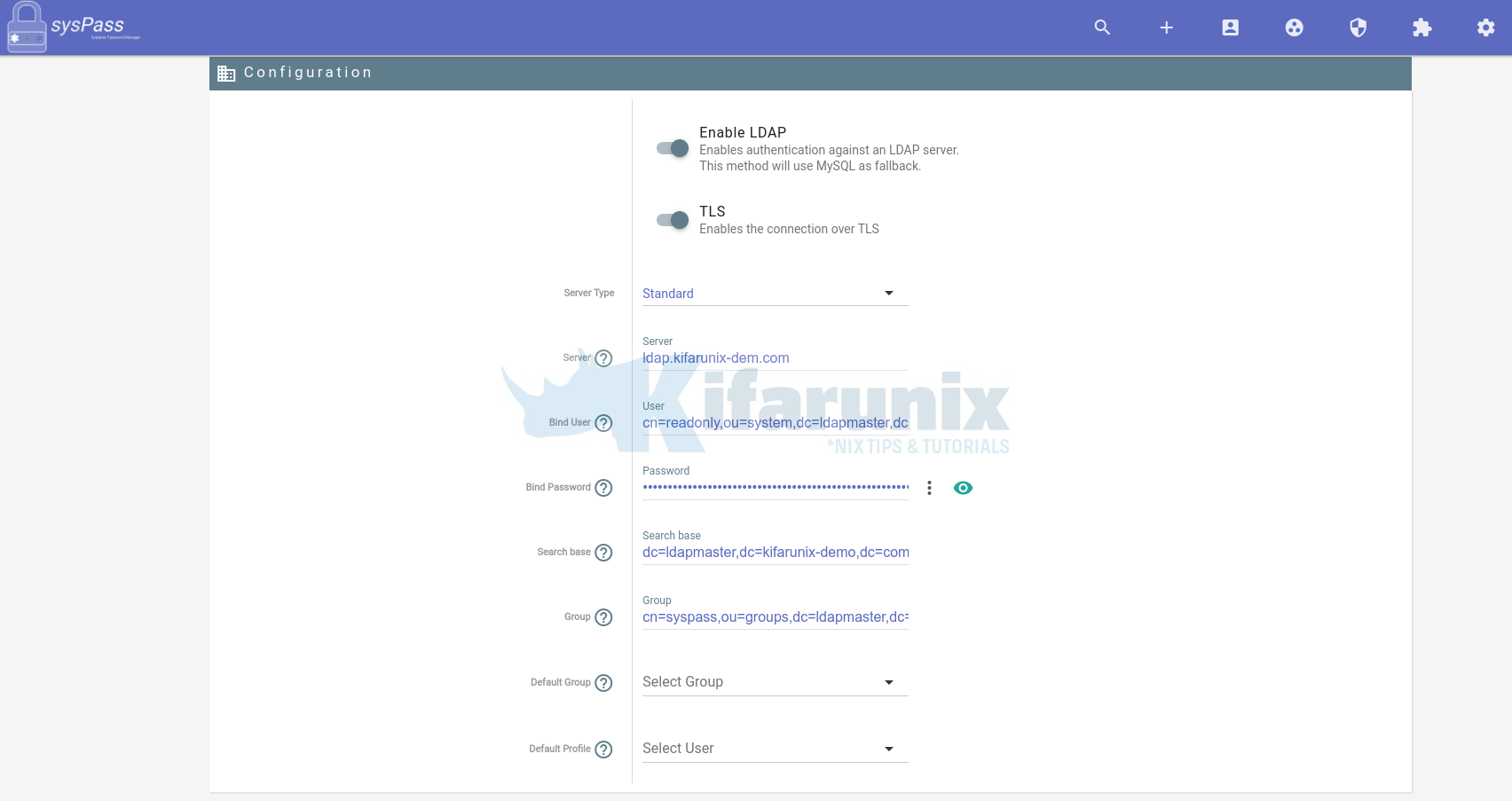
- Next, click the gear icon to access the configuration menu and click LDAP.
- Define sysPass OpenLDAP Configuration options
- Toggle the button to enable LDAP based authentication.
- Also turn on TLS connection if your OpenLDAP server is configured with TLS.
- To be able to use TLS connection, you need to;
- Install LDAP CA cert on the sysPass server
- Define the LDAP CA Path on sysPass server as shown below.
- To be able to use TLS connection, you need to;
- Server type:
standard. - Server:
- This is the LDAP server url or IP address. In our setup, ldap.kifarunix-demo.com.
- Bind User:
- This is the DN of the user to authenticate. In our setup, it is
cn=readonly,ou=system,dc=ldapmaster,dc=kifarunix-demo,dc=com.
- This is the DN of the user to authenticate. In our setup, it is
- Bind Password:
- The credentials for the user to authenticate
- This is the password for the user specified by the bind DN above.
- Search Base:
- defines the location in the OpenLDAP directory where the search for a particular directory object begins.
- In our setup, the search base for users and groups is
dc=ldapmaster,dc=kifarunix-demo,dc=com.
- Group:
- This defines the group to which the user must belong to to be able to login to sysPass.
- As seen above, the group in our setup is
cn=syspass,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com.
- Default Group and Default Profile, leave empty.
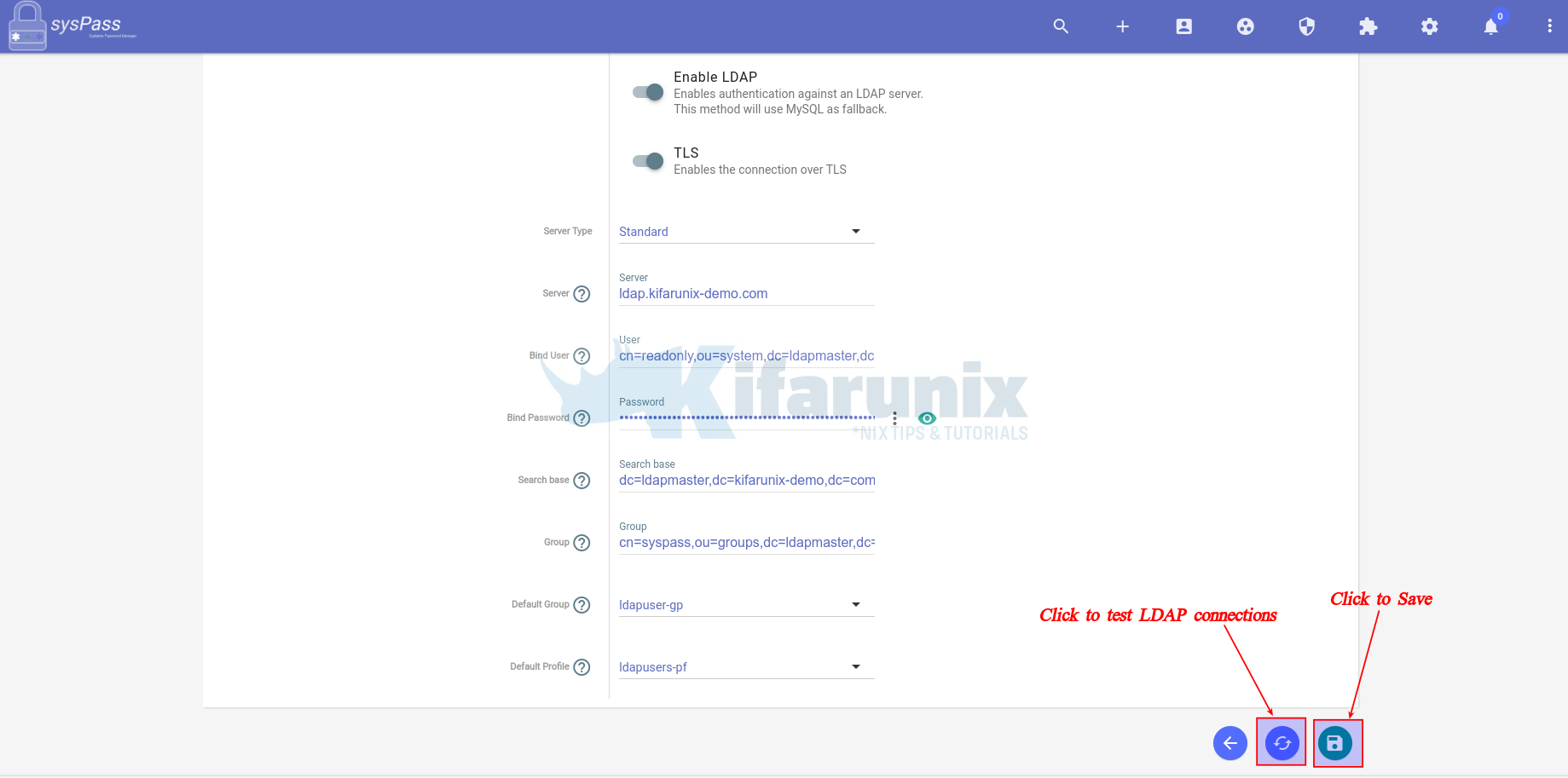
- Next, click the “exchange” icon to check connection to LDAP server. Ensure you have installed OpenLDAP CA certs if you enabled TLS before you can test the connection.
- If the connection is successful, you should see a list of all users in the OpenLDAP sysPass group.
Install OpenLDAP server CA cert and define the path on sysPass server.
Install OpenLDAP utilities on the sysPass server;
apt install ldap-utils -yDownload LDAP CA cert;
openssl s_client -connect ldap:389 -starttls ldap -showcerts </dev/null 2>/dev/null | openssl x509-----BEGIN CERTIFICATE----- MIIDozCCAougAwIBAgIUDd/aVBaJgUpWFNUbXOHYZTIb5KYwDQYJKoZIhvcNAQEL BQAwYTELMAkGA1UEBhMCWFgxFTATBgNVBAcMDERlZmF1bHQgQ2l0eTEcMBoGA1UE CgwTRGVmYXVsdCBDb21wYW55IEx0ZDEdMBsGA1UEAwwUKi5raWZhcnVuaXgtZGVt by5jb20wHhcNMjIwMTIyMjAwOTUwWhcNMjMwMTIyMjAwOTUwWjBhMQswCQYDVQQG EwJYWDEVMBMGA1UEBwwMRGVmYXVsdCBDaXR5MRwwGgYDVQQKDBNEZWZhdWx0IENv bXBhbnkgTHRkMR0wGwYDVQQDDBQqLmtpZmFydW5peC1kZW1vLmNvbTCCASIwDQYJ KoZIhvcNAQEBBQADggEPADCCAQoCggEBANVwVxFtjvHrgTHADFmE/NfsBjnnsorD d6Hww+RDKTTdwpSQtAi5e9roP4umjLelQmIs2iPijBwFzTwh1ok7e40K0WFUCXwW O2R2FomvwXe5D5VmlXLc4jY8/z6QuSv/j27q3DT44ywV8WmtWQ732cLo6YT1e441 LeXcCn258zvH8QE4UJOErJqDijFzuSxTj0gAsHe7ef+B2rhhD9Jzh6g4RYzDWmI3 oAZT/oArfWJFf+yP9eCunn/Q+b2RVWB9/Do9MYGdqOJJcDJ1w3pAyuEUWnDqTrhR wjpIFub8lRlqrlNv7raw++aIIIUzCkl74/ReLgMRYlHAHC2pfMgLYjkCAwEAAaNT MFEwHQYDVR0OBBYEFMN/TE6ZSw95erqDLAXa/LOfRFtqMB8GA1UdIwQYMBaAFMN/ TE6ZSw95erqDLAXa/LOfRFtqMA8GA1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQEL BQADggEBAL+PuCNgR0MnOzl6IrxVZA9dDH0/DnMm2WjxkS3w5sfIPpUlVgSHmVeT +a9raqFrve7RXHRBwouWlO/3n0218WSns6nyl9hTWbYIlIjCTFVCEFe68Q0ulcPy AUEQBoKc6fUZCtenJDo2SVKt7dnX1EAi4Ohnig+f9zMrYFxYajdFAxJJV6wxJnnF duLYpRexUxdzOvPUP4vkP2haZmRRWBDfmj2bSQF/r3DE4Yg8nVxHndsmxcVls4wF 7ddAL/Gx5Lv3QZPpxi8ZcHV8SRCP8N5VZP+hINr/M4gw3YO/S5F0TXnq5LQP0ePD bkc1+yvlgKUPaXH20/C1COiGI+r8UGA= -----END CERTIFICATE-----
Install the OpenLDAP CA cert on specific path;
cat > /etc/ssl/certs/openldap-ca.pem << 'EOL' -----BEGIN CERTIFICATE----- MIIDozCCAougAwIBAgIUDd/aVBaJgUpWFNUbXOHYZTIb5KYwDQYJKoZIhvcNAQEL BQAwYTELMAkGA1UEBhMCWFgxFTATBgNVBAcMDERlZmF1bHQgQ2l0eTEcMBoGA1UE CgwTRGVmYXVsdCBDb21wYW55IEx0ZDEdMBsGA1UEAwwUKi5raWZhcnVuaXgtZGVt by5jb20wHhcNMjIwMTIyMjAwOTUwWhcNMjMwMTIyMjAwOTUwWjBhMQswCQYDVQQG EwJYWDEVMBMGA1UEBwwMRGVmYXVsdCBDaXR5MRwwGgYDVQQKDBNEZWZhdWx0IENv bXBhbnkgTHRkMR0wGwYDVQQDDBQqLmtpZmFydW5peC1kZW1vLmNvbTCCASIwDQYJ KoZIhvcNAQEBBQADggEPADCCAQoCggEBANVwVxFtjvHrgTHADFmE/NfsBjnnsorD d6Hww+RDKTTdwpSQtAi5e9roP4umjLelQmIs2iPijBwFzTwh1ok7e40K0WFUCXwW O2R2FomvwXe5D5VmlXLc4jY8/z6QuSv/j27q3DT44ywV8WmtWQ732cLo6YT1e441 LeXcCn258zvH8QE4UJOErJqDijFzuSxTj0gAsHe7ef+B2rhhD9Jzh6g4RYzDWmI3 oAZT/oArfWJFf+yP9eCunn/Q+b2RVWB9/Do9MYGdqOJJcDJ1w3pAyuEUWnDqTrhR wjpIFub8lRlqrlNv7raw++aIIIUzCkl74/ReLgMRYlHAHC2pfMgLYjkCAwEAAaNT MFEwHQYDVR0OBBYEFMN/TE6ZSw95erqDLAXa/LOfRFtqMB8GA1UdIwQYMBaAFMN/ TE6ZSw95erqDLAXa/LOfRFtqMA8GA1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQEL BQADggEBAL+PuCNgR0MnOzl6IrxVZA9dDH0/DnMm2WjxkS3w5sfIPpUlVgSHmVeT +a9raqFrve7RXHRBwouWlO/3n0218WSns6nyl9hTWbYIlIjCTFVCEFe68Q0ulcPy AUEQBoKc6fUZCtenJDo2SVKt7dnX1EAi4Ohnig+f9zMrYFxYajdFAxJJV6wxJnnF duLYpRexUxdzOvPUP4vkP2haZmRRWBDfmj2bSQF/r3DE4Yg8nVxHndsmxcVls4wF 7ddAL/Gx5Lv3QZPpxi8ZcHV8SRCP8N5VZP+hINr/M4gw3YO/S5F0TXnq5LQP0ePD bkc1+yvlgKUPaXH20/C1COiGI+r8UGA= -----END CERTIFICATE----- EOL
You can use one command though;
openssl s_client -connect ldap:389 -starttls ldap
-showcerts </dev/null 2>/dev/null |
openssl x509 > /etc/ssl/certs/openldap-ca.pemsysPass OpenLDAP User Login
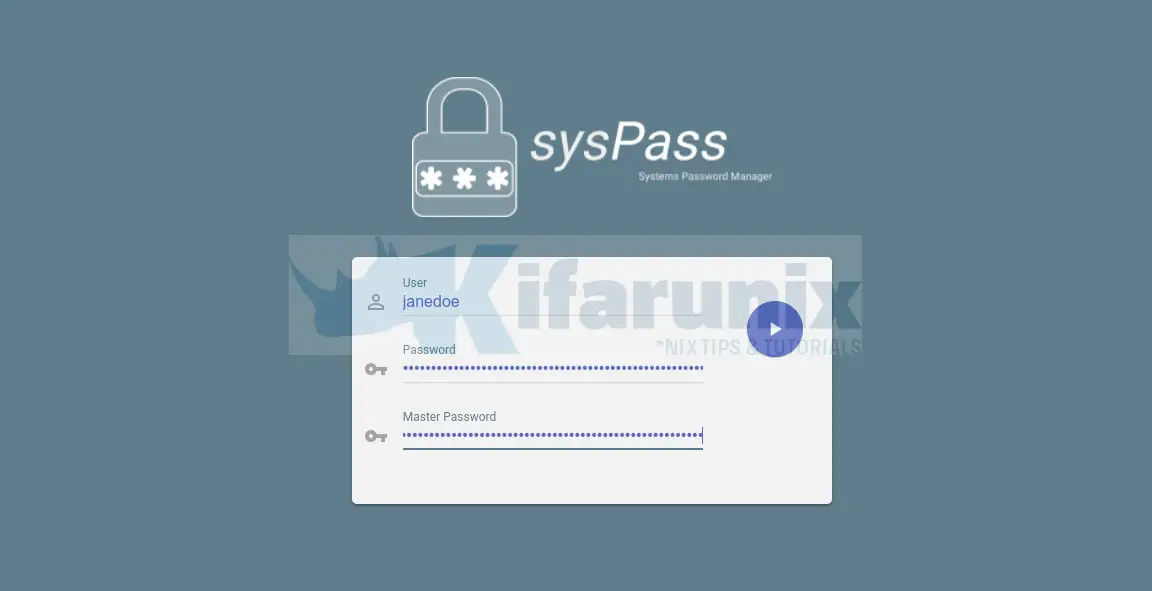
Once you have configured sysPass for OpenLDAP authentication, you need to generate a temporary master password as it is required for every first login. Temporary master password is used so as not to reveal the original admin password.
To generate temporary master password, login to sysPass as admin and navigate to Configuration > Encryption > Temporary Password. Note the lifetime of the password.
For every new user logging in, share with them the temporary master password generated.
For example, logging in as our LDAP user janedoe;
When you first enter your credentials and press Enter, authentication will fail with Master password is not saved or wrong.
The enter the username/password and temporary master password provided.
From Administrator site, you should be able to see LDAP accounts added to the sysPass system.
And that is how easily you can integrate sysPass with OpenLDAP for authentication.
Other Tutorials
Configure SSSD for LDAP Authentication on Ubuntu 22.04
Integrate Gitlab with OpenLDAP for Authentication
-
#1
After updating to custombuild 2.0.0 (rev: 2496) and DirectAdmin V1.61.0, Bind doesn’t work anymore
I failed in my research…
Any idea ?
~# service bind9 status
Code:
bind9.service - BIND Domain Name Server
Loaded: loaded (/lib/systemd/system/bind9.service; disabled; vendor preset: enabled)
Active: inactive (dead)
Docs: man:named(8)~# /etc/init.d/bind9 restart
Code:
/etc/init.d/bind9 restart
[....] Restarting bind9 (via systemctl): bind9.serviceJob for bind9.service failed because the control process exited with error code.
See "systemctl status bind9.service" and "journalctl -xe" for details.
failed!~# systemctl status bind9.service
Code:
bind9.service - BIND Domain Name Server
Loaded: loaded (/lib/systemd/system/bind9.service; disabled; vendor preset: enabled)
Active: failed (Result: exit-code) since Sun 2020-05-24 05:21:01 CEST; 21min ago
Docs: man:named(8)
Process: 27770 ExecStart=/usr/sbin/named $OPTIONS (code=exited, status=1/FAILURE)
Tasks: 0 (limit: 2319)
Memory: 396.0K
CGroup: /system.slice/bind9.service
May 24 05:21:01 vps123456.ovh.net named[27771]: listening on IPv4 interface eth0, 91.121.37.27#53
May 24 05:21:01 vps123456.ovh.net named[27771]: binding TCP socket: address in use
May 24 05:21:01 vps123456.ovh.net named[27771]: listening on IPv4 interface eth0, 91.121.45.207#53
May 24 05:21:01 vps123456.ovh.net named[27771]: binding TCP socket: address in use
May 24 05:21:01 vps123456.ovh.net named[27771]: unable to listen on any configured interfaces
May 24 05:21:01 vps123456.ovh.net named[27771]: loading configuration: failure
May 24 05:21:01 vps123456.ovh.net named[27771]: exiting (due to fatal error)
May 24 05:21:01 vps123456.ovh.net systemd[1]: bind9.service: Control process exited, code=exited, status=1/FAILURE
May 24 05:21:01 vps123456.ovh.net systemd[1]: bind9.service: Failed with result 'exit-code'.
May 24 05:21:01 vps123456.ovh.net systemd[1]: Failed to start BIND Domain Name Server.~# nano /var/log/messages
Code:
May 24 03:33:00 vps123456 kernel: [ 1504.328879] Firewall: *ICMP_IN Blocked* IN=eth0 OUT= MAC=fa:16:3e:08:e5:ba:02:fa:6a:50:b3:70:08:00 SRC=92.222.186.1 DST=87.98.169.140 LEN=32 TOS=0x08 PREC=0x00 TTL=7 ID=1 DF PROTO=ICMP TYPE=8 CODE=0 ID=47744 SEQ=1
May 24 03:33:00 vps123456 kernel: [ 1504.695458] Firewall: *TCP_IN Blocked* IN=eth0 OUT= MAC=fa:16:3e:08:e5:ba:02:fa:6a:50:b3:70:08:00 SRC=213.217.0.101 DST=51.38.215.43 LEN=40 TOS=0x00 PREC=0x00 TTL=241 ID=31311 PROTO=TCP SPT=42185 DPT=5381 WINDOW=1024 RES=0x00 SYN URGP=0
May 24 03:33:01 vps123456 kernel: [ 1505.179205] Firewall: *ICMP_IN Blocked* IN=eth0 OUT= MAC=fa:16:3e:08:e5:ba:02:fa:6a:50:b3:70:08:00 SRC=92.222.185.1 DST=91.121.45.207 LEN=32 TOS=0x08 PREC=0x00 TTL=5 ID=1 DF PROTO=ICMP TYPE=8 CODE=0 ID=39936 SEQ=1Iptable and CSF
Ip’s are unknown and not blocked
But Bind seems working in the same time !!!!!!
~# dig @localhost 91.121.37.27
Code:
; <<>> DiG 9.11.5-P4-5.1+deb10u1-Debian <<>> @localhost 91.121.37.27
; (2 servers found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: REFUSED, id: 55666
;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1
;; WARNING: recursion requested but not available
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
; COOKIE: 49bbdff1ebd4a0ec6cc0b5cc5ec9ee42b0e1fa583c7d7a2a (good)
;; QUESTION SECTION:
;91.121.37.27. IN A
;; Query time: 4 msec
;; SERVER: ::1#53(::1)
;; WHEN: Sun May 24 05:47:14 CEST 2020
;; MSG SIZE rcvd: 69Last edited: May 26, 2020
-
#2
Have you try reboot server ?
or try kill all process like » bind » or any use by port 53
» unable to listen on any configured interfaces «
It seem port is used by other process like bind previous doesn’t clean restart
-
#3
Yes reboot the server have been done, and more than one time..
I agree with you, it seem port 53 is used by other process like bind OR like if a «second» Bind is installed on the same server !
But apparently Not as we can see below.
~# netstat -nlpt
Code:
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:587 0.0.0.0:* LISTEN 452/exim
tcp 0 0 127.0.0.1:3310 0.0.0.0:* LISTEN 934/clamd
tcp 0 0 0.0.0.0:110 0.0.0.0:* LISTEN 435/dovecot
tcp 0 0 127.0.0.1:783 0.0.0.0:* LISTEN 3840/perl
tcp 0 0 0.0.0.0:143 0.0.0.0:* LISTEN 435/dovecot
tcp 0 0 0.0.0.0:465 0.0.0.0:* LISTEN 452/exim
tcp 0 0 91.121.37.27:53 0.0.0.0:* LISTEN 8358/named
tcp 0 0 0.0.0.0:21 0.0.0.0:* LISTEN 578/pure-ftpd
tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN 452/exim
tcp 0 0 0.0.0.0:993 0.0.0.0:* LISTEN 435/dovecot
tcp 0 0 0.0.0.0:995 0.0.0.0:* LISTEN 435/dovecot
tcp6 0 0 :::3306 :::* LISTEN 846/mysqld
tcp6 0 0 :::2222 :::* LISTEN 580/directadmin
tcp6 0 0 :::80 :::* LISTEN 923/httpd
tcp6 0 0 :::56180 :::* LISTEN 632/sshd
tcp6 0 0 :::53 :::* LISTEN 8358/named
tcp6 0 0 :::21 :::* LISTEN 578/pure-ftpd
tcp6 0 0 :::443 :::* LISTEN 923/httpd-
#4
Seem like your bind with tcp4 has problem with that ip while tcp6 bind with localhost ip. and can work normally with tcp6
let debug in step by step
try rewrite_confs with directadmin
change your bind tcp4 to 0.0.0.0
in named.conf
remove all include domain with not localhost
other else you need to get some one to debug directly in server with like tool anydesk or teamviewer
-
#5
We are not at the step to get some one to debug directly in the server with tools like anydesk or teamviewer.
Maybe, if you give me the command line to try what you are saying will be enough.
How to :
try rewrite_confs with directadmin
How to :
change your bind tcp4 to 0.0.0.0
-
#6
try change bind tcp4
recreate named_zone
echo «action=rewrite&value=named» >> /usr/local/directadmin/data/task.queue
/usr/local/directadmin/dataskq d40
I try to ping that port on ip: 91.121.37.27:53
It open normally but when bind fail to start shouldn’t open that port.
try to stop bind service and ping that port
if you stop and can ping online port 53 that it’s use by other in network on IP 91.121.37.27.
-
#7
This link doesn’t show how to change tcp4 to tcp6
But Bind listen already on all interfaces and IP (default) with listen on all interfaces and IP (default) in /etc/bind/named.conf with :
listen-on { any; };
recreate named_zone
echo «action=rewrite&value=named» >> /usr/local/directadmin/data/task.queue
/usr/local/directadmin/dataskq d40
This is will erase all existing DNS Zone ?
I would like avoid to erase my dns existing zones, that’s an hard job to create again all dns zone for all domains name…
if you stop and can ping online port 53 that it’s use by other in network on IP 91.121.37.27
Bind is offline already because the problem is «Bind don’t start»
Any way I have done
and Bind stopped
~# ping 91.121.37.27:53
Code:
ping: 91.121.37.27:53: Name or service not known~# ping -c 3 91.121.37.27
Code:
PING 91.121.37.27 (91.121.37.27) 56(84) bytes of data.
64 bytes from 91.121.37.27: icmp_seq=1 ttl=64 time=0.129 ms
64 bytes from 91.121.37.27: icmp_seq=2 ttl=64 time=0.104 ms
64 bytes from 91.121.37.27: icmp_seq=3 ttl=64 time=0.070 ms
--- 91.121.37.27 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 32ms
rtt min/avg/max/mdev = 0.070/0.101/0.129/0.024 ms-
#8
You shouldn’t use ping to tell port
When you want to check some port opened please use eg.
That it hard to debug without checking with remote
Your bind start fail but I still got telnet to 53 on your IP and it’s open port.
If it start fait. Port shouldn’t open.
because your ipv6 can start normolly but your ipv4 is problem.
It hard to help without debug directly
Create ticket to directadmin support and let them help you directly.
You need to find your friend to check directly
-
#9
It hard to help without debug directly
Many thanks for you help
Let’s wait a little bit, maybe I going to be lucky with other people
-
#10
I’d like to note CustomBuild does not manage Bind. You must be having a configuration issue. Check:
Code:
/usr/sbin/named-checkconf -z /etc/named.conf | grep -v loaded-
#11
Thanks Mister Custom Build
/usr/sbin/named-checkconf -z /etc/named.conf | grep -v loaded
Code:
~# /usr/sbin/named-checkconf -z /etc/named.conf | grep -v loaded
open: /etc/named.conf: file not found
How this file can disappear ?
How to create a new one ?
Or you mean /usr/sbin/named-checkconf -z /etc/bind/named.conf | grep -v loaded
Thanks
-
#12
This is default named.conf
Readd all zone of All domain.
-
#13
Thanks Mister Custom Build
Code:
~# /usr/sbin/named-checkconf -z /etc/named.conf | grep -v loaded open: /etc/named.conf: file not foundHow this file can disappear ?
How to create a new one ?Or you mean /usr/sbin/named-checkconf -z /etc/bind/named.conf | grep -v loaded
Thanks
Oh, if that’s debian — yes, you need to point it to another location. Please check /usr/sbin/named-checkconf -z /etc/bind/named.conf | grep -v loaded.
-
#14
Oh, if that’s debian — yes, you need to point it to another location. Please check
/usr/sbin/named-checkconf -z /etc/bind/named.conf | grep -v loaded
It return nothing or any problems and seems that I do not have any configuration issues
Please give me a new direction to search
Apparently that’s more with :
Code:
binding TCP socket: address in useand
Code:
Process: 13969 ExecStart=/usr/sbin/named $OPTIONS (code=exited, status=1/FAILURE)That’s the error when I am trying to restart bind (/etc/init.d/bind9 restart)
-
#15
The journalctl -xe command also not showing strange things?
-
#16
The journalctl -xe command also not showing strange things?
Yes, with journalctl -xe command I have :
Code:
May 25 00:48:37 vps123456.ovh.net kernel: Firewall: *TCP_IN Blocked* IN=eth0 OUT= MAC=fa:16:3e:08:e5:ba:32:cf:ac:97:ec:de:08:00 SRC=94.102.50.137 DST=91.121.37.27 LEN=40 TOS=0x00 PREC=0x00 TTL=245 ID=8462 PROTO=TCP SPT=51347 DPT=20031 WI
May 25 00:48:37 vps123456.ovh.net kernel: Firewall: *ICMP_IN Blocked* IN=eth0 OUT= MAC=fa:16:3e:08:e5:ba:32:cf:ac:97:ec:de:08:00 SRC=167.114.37.1 DST=91.121.37.27 LEN=32 TOS=0x08 PREC=0x00 TTL=4 ID=1 DF PROTO=ICMP TYPE=8 CODE=0 ID=35770
May 25 00:48:38 vps123456.ovh.net kernel: Firewall: *TCP_IN Blocked* IN=eth0 OUT= MAC=fa:16:3e:08:e5:ba:32:cf:ac:97:ec:de:08:00 SRC=195.54.166.181 DST=51.68.71.112 LEN=40 TOS=0x00 PREC=0x00 TTL=242 ID=9732 PROTO=TCP SPT=45184 DPT=11799 W
May 25 00:48:39 vps123456.ovh.net kernel: Firewall: *TCP_IN Blocked* IN=eth0 OUT= MAC=fa:16:3e:08:e5:ba:32:cf:ac:97:ec:de:08:00 SRC=194.26.29.51 DST=91.121.45.207 LEN=40 TOS=0x00 PREC=0x00 TTL=244 ID=56435 PROTO=TCP SPT=42711 DPT=2065 WI
May 25 00:48:40 vps123456.ovh.net kernel: Firewall: *ICMP_IN Blocked* IN=eth0 OUT= MAC=fa:16:3e:08:e5:ba:32:cf:ac:97:ec:de:08:00 SRC=92.222.186.1 DST=87.98.169.140 LEN=32 TOS=0x08 PREC=0x00 TTL=7 ID=1 DF PROTO=ICMP TYPE=8 CODE=0 ID=47432
May 25 00:48:41 vps123456.ovh.net kernel: Firewall: *TCP_IN Blocked* IN=eth0 OUT= MAC=fa:16:3e:08:e5:ba:32:cf:ac:97:ec:de:08:00 SRC=185.175.93.6 DST=51.38.215.43 LEN=40 TOS=0x00 PREC=0x00 TTL=241 ID=10703 PROTO=TCP SPT=54229 DPT=3393 WIN
May 25 00:48:42 vps123456.ovh.net kernel: Firewall: *TCP_IN Blocked* IN=eth0 OUT= MAC=fa:16:3e:08:e5:ba:32:cf:ac:97:ec:de:08:00 SRC=68.183.83.51 DST=87.98.169.132 LEN=40 TOS=0x00 PREC=0x00 TTL=234 ID=11980 PROTO=TCP SPT=45548 DPT=14315 W
May 25 00:48:42 vps123456.ovh.net kernel: Firewall: *TCP_IN Blocked* IN=eth0 OUT= MAC=fa:16:3e:08:e5:ba:32:cf:ac:97:ec:de:08:00 SRC=194.26.29.227 DST=51.38.250.175 LEN=40 TOS=0x00 PREC=0x00 TTL=244 ID=12518 PROTO=TCP SPT=59109 DPT=29609
lines 932-1001/1001 (END)-
#17
I stopped CSF (csf -x) just be sure this problem doesn’t come from the firewall
Bind doesn’t start and still yell :
Code:
May 25 00:59:00 vps123456.ovh.net named[19806]: listening on IPv4 interface eth0, 91.121.37.27#53
May 25 00:59:00 vps123456.ovh.net named[19806]: binding TCP socket: address in use
May 25 00:59:00 vps123456.ovh.net named[19806]: unable to listen on any configured interfaces
May 25 00:59:00 vps123456.ovh.net named[19806]: loading configuration: failure
May 25 00:59:00 vps123456.ovh.net named[19806]: exiting (due to fatal error)
May 25 00:59:00 vps123456.ovh.net systemd[1]: bind9.service: Control process exited, code=exited, status=1/FAILURE
--
-- A start job for unit bind9.service has finished with a failure.
--
-- The job identifier is 1278 and the job result is failed.
May 25 00:59:01 vps123456.ovh.net CRON[19829]: pam_unix(cron:session): session opened for user root by (uid=0)
May 25 00:59:01 vps123456.ovh.net CRON[19830]: (root) CMD (/usr/local/directadmin/dataskq)
May 25 00:59:01 vps123456.ovh.net CRON[19829]: pam_unix(cron:session): session closed for user rootLast edited: May 24, 2020
-
#18
Just out of curiosity, cuold it be a hostname issue? Or did you always use vps123456.ovh.net as hostname? I’m must wondering if maybe bind9 is trying to start via vps12345.ovh.net and DA lets it start under host.domain.com.
If not, I’ll leave things to smtalk, he’s smarter anyway.
-
#19
Just out of curiosity, cuold it be a hostname issue
My hostname have been always same (vps12345.ovh.net ), I didn’t change anything, I just updated Directadmin and the Bind’s problem came
-
#20
Something seems to be already started on port 53. Check:
netstat -lnp | grep 53
0
1
Не запускается service bind9
Feb 02 17:33:12 andrew named[1348]: binding TCP socket: address in use
Feb 02 17:33:12 andrew named[1348]: listening on IPv4 interface enp4s0, 192.168.1.197#53
Feb 02 17:33:12 andrew named[1348]: binding TCP socket: address in use
Feb 02 17:33:12 andrew named[1348]: listening on IPv4 interface enp3s0, 192.168.0.99#53
Feb 02 17:33:12 andrew named[1348]: binding TCP socket: address in use
Feb 02 17:33:12 andrew named[1348]: unable to listen on any configured interfaces
Feb 02 17:33:12 andrew named[1348]: loading configuration: failure
Feb 02 17:33:12 andrew named[1348]: exiting (due to fatal error)
Feb 02 17:33:12 andrew systemd[1]: bind9.service: Main process exited, code=exited, status=1/FAILURE
Feb 02 17:33:12 andrew systemd[1]: bind9.service: Failed with result ‘exit-code’.
Hello everyone is glad that I was able to get here. We are playing a little with syspass, but we have a problem
Connection error (BIND).
LDAP ERROR: Can not contact LDAP server (-1)
LDAP DN: syspass
I do not how I can not figure out what’s wrong, but I’ve been through a lot of options:
- I was trying to specify FQDN and ip server name
- The user is specified without prefixes simply Administrator (Domain Administrator in Active Directory)
- I checked telnet access to ldap server
- I tried to specify the server with all the possible prefixes ldap. *, Ldap:
But I’m getting this error. I want to know in addition to installing php56w-ldap, I had to do some other setup?
Here is a screenshot of my setting
Comments
I have a strange issue. Best part of users can login, but few can’t. That’s return wrong password and get this error:
Erreur de connexion (BIND)
LDAP ERROR: Can’t contact LDAP server (-1)
LDAP DN: CN=LDAPUSER,CN=Users,DC=MYBUSINESS,DC=local
They are all in the same LDAP folder, I didn’t specifie Group in sysPass setting.
Could be special char in password?
Hi, can you tell me if the LDAP connection changes on every login?. This is a feature that runs when a DNS hostname is given for the LDAP server. You can see it the sysPass event log.
In addition, it’s happen only in the first loggin. Once got User Disabled, that do not happen again.
Not sure what you asking for. But I juste log once with one browser and logged again in Private mode. I got this in log (Commit version: 6f44f8c):
First:
1262 2015-12-09 09:34:11 Se connecter SXXXXXXXXX ... (LDAP)
Connexion au serveur : srvdc.mybusiness.local
Utilisateur : sxxxxxxxxx
Profil : Admin
Groupe : Admins
Second:
1265 2015-12-09 09:42:18 Se connecter SXXXXXXXXX ... (MySQL)
Utilisateur : sxxxxxxxxx
Profil : Admin
Groupe : Admins
1264 2015-12-09 09:42:18 ldapBind ... Erreur de connexion (BIND)
LDAP ERROR: Can’t contact LDAP server (-1)
LDAP DN: CN=LDAP,CN=Users,DC=mybusiness,DC=local
I enabled Debug, I took a look in error.log. what display is wrong:
ldap_url_parse_ext(ldap://localhost/)
ldap_init: trying /etc/ldap/ldap.conf
ldap_init: using /etc/ldap/ldap.conf
ldap_init: HOME env is NULL
ldap_init: trying ldaprc
ldap_init: LDAPCONF env is NULL
ldap_init: LDAPRC env is NULL
ldap_create
ldap_url_parse_ext(ldap://dcfiles.mybusiness.local:389)
ldap_sasl_bind_s
ldap_sasl_bind
ldap_send_initial_request
ldap_new_connection 1 1 0
ldap_int_open_connection
ldap_connect_to_host: TCP dcfiles.mybusiness.local:389
ldap_connect_to_host: getaddrinfo failed: Nom ou service inconnu
ldap_err2string
ldap_err2string
No Ideal where that «dcfiles» is from. this is not what is set in the config file.
Seconde attemp, got:
ldap_url_parse_ext(ldap://localhost/)
ldap_init: trying /etc/ldap/ldap.conf
ldap_init: using /etc/ldap/ldap.conf
ldap_init: HOME env is NULL
ldap_init: trying ldaprc
ldap_init: LDAPCONF env is NULL
ldap_init: LDAPRC env is NULL
ldap_create
ldap_url_parse_ext(ldap://sbs2k3.mybusiness.local:389)
ldap_sasl_bind_s
ldap_sasl_bind
ldap_send_initial_request
ldap_new_connection 1 1 0
ldap_int_open_connection
ldap_connect_to_host: TCP sbs2k3.mybusiness.local:389
ldap_new_socket: 17
ldap_prepare_socket: 17
ldap_connect_to_host: Trying 192.168.0.2:389
ldap_pvt_connect: fd: 17 tm: 10 async: 0
ldap_ndelay_on: 17
attempting to connect:
connect errno: 115
ldap_int_poll: fd: 17 tm: 10
ldap_is_sock_ready: 17
ldap_is_socket_ready: error on socket 17: errno: 113 (No route to host)
ldap_pvt_connect: -1
ldap_close_socket: 17
ldap_err2string
ldap_err2string
This «sbs2k3» is from a old server removed. Maybe the issue is on my ldap server side? But the ldap still not use the right configuration from the config file.
That is the behavior that I told you, if you provide an LDAP hostname (myserver.mydomain.com) it will search for other AD servers on your domain to make auth requests.
If you only set an ip address (your AD ip address), it will not search for other servers….
OK, didn’t know that. I set a IP, Tested OK
Thanks!
Check your AD, it could you get some annoying issues with «ghost» servers…
2 participants
LDAP (Lightweight Directory Access Protocol) is a protocol used for accessing and maintaining distributed directory information services over an IP network. The ldap_bind invalid credentials (49) error is a common error that occurs when trying to authenticate with an LDAP server. This error occurs due to incorrect username and password, or due to a misconfiguration in the LDAP server.
If you encounter this error, don’t worry. In this guide, we will show you how to fix ldap_bind invalid credentials (49) error step-by-step.
Step 1: Check the LDAP Server Status
The first step to fixing ldap_bind invalid credentials (49) error is to check if the LDAP server is running and reachable. To do this, you can use the ping command to ping the server IP address.
ping ldap.server.ip.address
If the LDAP server is running and reachable, you should receive a response. If not, you need to check the network connection and make sure that the LDAP server is up and running.
Step 2: Verify the Username and Password
The second step is to verify the username and password that you are using to authenticate with the LDAP server. Make sure that the credentials are correct and match the ones stored in the LDAP server.
Step 3: Check the LDAP Configuration
If the username and password are correct, the next step is to check the LDAP configuration. Ensure that the LDAP server is configured correctly, and the LDAP client is using the correct configuration file.
Step 4: Check the LDAP Client Configuration
If the LDAP configuration is correct, the next step is to check the LDAP client configuration. Ensure that the LDAP client is using the correct server address, port number, and protocol.
Step 5: Enable LDAP Debugging
If you are still having issues with ldap_bind invalid credentials (49) error, you can enable LDAP debugging to get more information about the error. To do this, add the following lines to the LDAP client configuration file:
loglevel 256
debug yes
This will enable debugging and provide more information about the error.
Frequently Asked Questions (FAQ)
Q1. What is ldap_bind invalid credentials (49) error?
ldap_bind invalid credentials (49) error is an error that occurs when trying to authenticate with an LDAP server. This error occurs due to incorrect username and password, or due to a misconfiguration in the LDAP server.
Q2. How can I fix ldap_bind invalid credentials (49) error?
To fix ldap_bind invalid credentials (49) error, you need to check the LDAP server status, verify the username and password, check the LDAP configuration, check the LDAP client configuration, and enable LDAP debugging.
Q3. How do I ping an LDAP server?
To ping an LDAP server, use the ping command followed by the server IP address:
ping ldap.server.ip.address
Q4. How do I verify the LDAP configuration?
To verify the LDAP configuration, ensure that the LDAP server is configured correctly, and the LDAP client is using the correct configuration file.
Q5. How do I enable LDAP debugging?
To enable LDAP debugging, add the following lines to the LDAP client configuration file:
loglevel 256
debug yes
- LDAP Tutorial
- LDAP Authentication
- LDAP Server Configuration
We hope that this guide has helped you to fix ldap_bind invalid credentials (49) error. If you have any further questions or need assistance, please feel free to contact us.
Follow through this tutorial to learn how to integrate sysPass with OpenLDAP for authentication and account management.
Integrate sysPass with OpenLDAP for Authentication
- Install and Setup OpenLDAP server
In our previous tutorials, we covered how to install and setup OpenLDAP server. Follow the link below to check them.
Install and Setup OpenLDAP server
- Install and Setup sysPass
Follow the link below to install and setup sysPass.
Install and setup sysPass on Linux
- Integrate sysPass with OpenLDAP for Authentication
To begin, ensure sysPass is installed with PHP-LDAP modules.
php -m | grep ldap- Create OpenLDAP User Group for sysPass
Create an group of OpenLDAP that can be used to control access to sysPass. All members of the group to be created will allowed to access/login to sysPass.
Follow our guide below to learn how to setup OpenLDAP groups.
How to Create OpenLDAP Member Groups
In our OpenLDAP server, we have created a group called syspass.
Some members have been added to this group as evident in the command output below;
ldapsearch -H ldapi:/// -Y EXTERNAL -LLL -Q -b "dc=ldapmaster,dc=kifarunix-demo,dc=com" cn=syspassSample output;
dn: cn=syspass,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com
objectClass: groupOfNames
cn: syspass
member: uid=johndoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
member: uid=janedoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
member: uid=devadmin,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
Integrate sysPass with OpenLDAP for Authentication
Once you have setup your OpenLDAP user/groups for sysPass authentication, login to sysPass web user interface as administrator.
- Create OpenLDAP users group.
This will be required to specify the default group under which OpenLDAP users belong to on sysPass.
To create group, click Users and accesses icon > GROUPS > New Group.
Save the group.
- Next, create OpenLDAP Users default Profile
This is where you define the default permissions to be assigned to a specific user profile. To create a profile, click Users and accesses icon > PROFILE > New Profile.
Sample account permissioms.
For the rest of the accesses, we didn’t give any for this particular profile. Feel Free to set the accesses accordingly.
So we now have a group, ldapuser-gp, and profile, ldapusers-pf.
Note that you should be able to define the specific profile/groups once the LDAP users are in the sysPass system.
- Next, click the gear icon to access the configuration menu and click LDAP.
- Define sysPass OpenLDAP Configuration options
- Toggle the button to enable LDAP based authentication.
- Also turn on TLS connection if your OpenLDAP server is configured with TLS.
- To be able to use TLS connection, you need to;
- Install LDAP CA cert on the sysPass server
- Define the LDAP CA Path on sysPass server as shown below.
- To be able to use TLS connection, you need to;
- Server type:
standard. - Server:
- This is the LDAP server url or IP address. In our setup, ldap.kifarunix-demo.com.
- Bind User:
- This is the DN of the user to authenticate. In our setup, it is
cn=readonly,ou=system,dc=ldapmaster,dc=kifarunix-demo,dc=com.
- This is the DN of the user to authenticate. In our setup, it is
- Bind Password:
- The credentials for the user to authenticate
- This is the password for the user specified by the bind DN above.
- Search Base:
- defines the location in the OpenLDAP directory where the search for a particular directory object begins.
- In our setup, the search base for users and groups is
dc=ldapmaster,dc=kifarunix-demo,dc=com.
- Group:
- This defines the group to which the user must belong to to be able to login to sysPass.
- As seen above, the group in our setup is
cn=syspass,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com.
- Default Group and Default Profile, leave empty.
- Next, click the “exchange” icon to check connection to LDAP server. Ensure you have installed OpenLDAP CA certs if you enabled TLS before you can test the connection.
- If the connection is successful, you should see a list of all users in the OpenLDAP sysPass group.
Install OpenLDAP server CA cert and define the path on sysPass server.
Install OpenLDAP utilities on the sysPass server;
apt install ldap-utils -yDownload LDAP CA cert;
openssl s_client -connect ldap:389 -starttls ldap -showcerts </dev/null 2>/dev/null | openssl x509
-----BEGIN CERTIFICATE-----
MIIDozCCAougAwIBAgIUDd/aVBaJgUpWFNUbXOHYZTIb5KYwDQYJKoZIhvcNAQEL
BQAwYTELMAkGA1UEBhMCWFgxFTATBgNVBAcMDERlZmF1bHQgQ2l0eTEcMBoGA1UE
CgwTRGVmYXVsdCBDb21wYW55IEx0ZDEdMBsGA1UEAwwUKi5raWZhcnVuaXgtZGVt
by5jb20wHhcNMjIwMTIyMjAwOTUwWhcNMjMwMTIyMjAwOTUwWjBhMQswCQYDVQQG
EwJYWDEVMBMGA1UEBwwMRGVmYXVsdCBDaXR5MRwwGgYDVQQKDBNEZWZhdWx0IENv
bXBhbnkgTHRkMR0wGwYDVQQDDBQqLmtpZmFydW5peC1kZW1vLmNvbTCCASIwDQYJ
KoZIhvcNAQEBBQADggEPADCCAQoCggEBANVwVxFtjvHrgTHADFmE/NfsBjnnsorD
d6Hww+RDKTTdwpSQtAi5e9roP4umjLelQmIs2iPijBwFzTwh1ok7e40K0WFUCXwW
O2R2FomvwXe5D5VmlXLc4jY8/z6QuSv/j27q3DT44ywV8WmtWQ732cLo6YT1e441
LeXcCn258zvH8QE4UJOErJqDijFzuSxTj0gAsHe7ef+B2rhhD9Jzh6g4RYzDWmI3
oAZT/oArfWJFf+yP9eCunn/Q+b2RVWB9/Do9MYGdqOJJcDJ1w3pAyuEUWnDqTrhR
wjpIFub8lRlqrlNv7raw++aIIIUzCkl74/ReLgMRYlHAHC2pfMgLYjkCAwEAAaNT
MFEwHQYDVR0OBBYEFMN/TE6ZSw95erqDLAXa/LOfRFtqMB8GA1UdIwQYMBaAFMN/
TE6ZSw95erqDLAXa/LOfRFtqMA8GA1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQEL
BQADggEBAL+PuCNgR0MnOzl6IrxVZA9dDH0/DnMm2WjxkS3w5sfIPpUlVgSHmVeT
+a9raqFrve7RXHRBwouWlO/3n0218WSns6nyl9hTWbYIlIjCTFVCEFe68Q0ulcPy
AUEQBoKc6fUZCtenJDo2SVKt7dnX1EAi4Ohnig+f9zMrYFxYajdFAxJJV6wxJnnF
duLYpRexUxdzOvPUP4vkP2haZmRRWBDfmj2bSQF/r3DE4Yg8nVxHndsmxcVls4wF
7ddAL/Gx5Lv3QZPpxi8ZcHV8SRCP8N5VZP+hINr/M4gw3YO/S5F0TXnq5LQP0ePD
bkc1+yvlgKUPaXH20/C1COiGI+r8UGA=
-----END CERTIFICATE-----
Install the OpenLDAP CA cert on specific path;
cat > /etc/ssl/certs/openldap-ca.pem << 'EOL'
-----BEGIN CERTIFICATE-----
MIIDozCCAougAwIBAgIUDd/aVBaJgUpWFNUbXOHYZTIb5KYwDQYJKoZIhvcNAQEL
BQAwYTELMAkGA1UEBhMCWFgxFTATBgNVBAcMDERlZmF1bHQgQ2l0eTEcMBoGA1UE
CgwTRGVmYXVsdCBDb21wYW55IEx0ZDEdMBsGA1UEAwwUKi5raWZhcnVuaXgtZGVt
by5jb20wHhcNMjIwMTIyMjAwOTUwWhcNMjMwMTIyMjAwOTUwWjBhMQswCQYDVQQG
EwJYWDEVMBMGA1UEBwwMRGVmYXVsdCBDaXR5MRwwGgYDVQQKDBNEZWZhdWx0IENv
bXBhbnkgTHRkMR0wGwYDVQQDDBQqLmtpZmFydW5peC1kZW1vLmNvbTCCASIwDQYJ
KoZIhvcNAQEBBQADggEPADCCAQoCggEBANVwVxFtjvHrgTHADFmE/NfsBjnnsorD
d6Hww+RDKTTdwpSQtAi5e9roP4umjLelQmIs2iPijBwFzTwh1ok7e40K0WFUCXwW
O2R2FomvwXe5D5VmlXLc4jY8/z6QuSv/j27q3DT44ywV8WmtWQ732cLo6YT1e441
LeXcCn258zvH8QE4UJOErJqDijFzuSxTj0gAsHe7ef+B2rhhD9Jzh6g4RYzDWmI3
oAZT/oArfWJFf+yP9eCunn/Q+b2RVWB9/Do9MYGdqOJJcDJ1w3pAyuEUWnDqTrhR
wjpIFub8lRlqrlNv7raw++aIIIUzCkl74/ReLgMRYlHAHC2pfMgLYjkCAwEAAaNT
MFEwHQYDVR0OBBYEFMN/TE6ZSw95erqDLAXa/LOfRFtqMB8GA1UdIwQYMBaAFMN/
TE6ZSw95erqDLAXa/LOfRFtqMA8GA1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQEL
BQADggEBAL+PuCNgR0MnOzl6IrxVZA9dDH0/DnMm2WjxkS3w5sfIPpUlVgSHmVeT
+a9raqFrve7RXHRBwouWlO/3n0218WSns6nyl9hTWbYIlIjCTFVCEFe68Q0ulcPy
AUEQBoKc6fUZCtenJDo2SVKt7dnX1EAi4Ohnig+f9zMrYFxYajdFAxJJV6wxJnnF
duLYpRexUxdzOvPUP4vkP2haZmRRWBDfmj2bSQF/r3DE4Yg8nVxHndsmxcVls4wF
7ddAL/Gx5Lv3QZPpxi8ZcHV8SRCP8N5VZP+hINr/M4gw3YO/S5F0TXnq5LQP0ePD
bkc1+yvlgKUPaXH20/C1COiGI+r8UGA=
-----END CERTIFICATE-----
EOL
You can use one command though;
openssl s_client -connect ldap:389 -starttls ldap
-showcerts </dev/null 2>/dev/null |
openssl x509 > /etc/ssl/certs/openldap-ca.pemsysPass OpenLDAP User Login
Once you have configured sysPass for OpenLDAP authentication, you need to generate a temporary master password as it is required for every first login. Temporary master password is used so as not to reveal the original admin password.
To generate temporary master password, login to sysPass as admin and navigate to Configuration > Encryption > Temporary Password. Note the lifetime of the password.
For every new user logging in, share with them the temporary master password generated.
For example, logging in as our LDAP user janedoe;
When you first enter your credentials and press Enter, authentication will fail with Master password is not saved or wrong.
The enter the username/password and temporary master password provided.
From Administrator site, you should be able to see LDAP accounts added to the sysPass system.
And that is how easily you can integrate sysPass with OpenLDAP for authentication.
Other Tutorials
Configure SSSD for LDAP Authentication on Ubuntu 22.04
Integrate Gitlab with OpenLDAP for Authentication
If you are getting error below after giving the correct password
Nov 2 03:56:42 testserver sshd[30173]: pam_ldap: error trying to bind as user «uid=testuser,ou=People,dc=test,dc=testdomain,dc=com» (Invalid credentials)
Nov 2 03:56:43 testserver sshd[30173]: Failed password for testuser from 10.17.0.3 port 51306 ssh2
Reason: Password is not syncing properly to all client server during the scheduled window
Solution : Restart the slapd service on LDAP server & it will sync to all server.
#/etc/init.d/slapd restart
Hope it helps.
Config LDAP tab’s test return Success with xx number users found.
When I try to login I got wrong user/pass. [Can’t contact LDAP server (-1]
Event Log:
3 2015-10-08 11:25:22 Log in 192.168.XXX.XXX (MySQL)
Incorrect login
User: USERNAME@XXXX.local
2 2015-10-08 11:25:22 ldapBind 192.168.XXX.XXX Connection error (BIND)
LDAP ERROR: Can’t contact LDAP server (-1)
LDAP DN: LDAP
1 2015-10-08 11:25:18 Clear Events ADMIN 192.168.XXX.XXX Clear event log
~ Event Log end ~
‘ldap_ads’ => true,
‘ldap_base’ => ‘OU=SBSUsers,OU=Users,OU=XXXXXX,DC=XXXXXXX,DC=local’,
‘ldap_bindpass’ => ‘XXXXXXXX’,
‘ldap_binduser’ => ‘LDAP’,
‘ldap_defaultgroup’ => 2,
‘ldap_defaultprofile’ => 2,
‘ldap_enabled’ => true,
‘ldap_group’ => false,
‘ldap_server’ => ‘XXXXXXXX.local’,
‘ldap_userattr’ => »,
git log —abbrev-commit —name-status HEAD^..HEAD
commit d039ac6
Author: nuxsmin nuxsmin@users.noreply.github.com
Date: Wed Oct 7 02:24:00 2015 +0200
M README.md
sysPass version 1.2.0.05
Database SERVER_VERSION : 5.5.5-10.0.20-MariaDB-0+deb8u1
CLIENT_VERSION : mysqlnd 5.0.11-dev — 20120503 — $Id: 3c688b6bbc30d36af3ac34fdd4b7b5b787fe5555 $
SERVER_INFO : Uptime: 610603 Threads: 1 Questions: 9201 Slow queries: 0 Opens: 84 Flush tables: 1 Open tables: 121 Queries per second avg: 0.015
CONNECTION_STATUS : Localhost via UNIX socket
Name: syspass@localhost
PHP Version: 5.6.13-0+deb8u1
Extensions: Core, date, ereg, libxml, openssl, pcre, zlib, bcmath, bz2, calendar, ctype, dba, dom, hash, fileinfo, filter, ftp, gettext, SPL, iconv, mbstring, session, posix, Reflection, standard, shmop, SimpleXML, soap, sockets, Phar, exif, sysvmsg, sysvsem, sysvshm, tokenizer, wddx, xml, xmlreader, xmlwriter, zip, apache2handler, mysqlnd, PDO, apcu, curl, gd, imagick, imap, intl, json, ldap, mcrypt, memcache, mysql, mysqli, pdo_mysql, pdo_sqlite, pspell, readline, recode, snmp, sqlite3, tidy, xmlrpc, xsl, mhash, apc, Zend OPcache
Used Memory: 768 KB
User: root
Server Apache/2.4.10 (Debian)
Можете ли вы заглянуть в журнал событий sysPass? Он должен зарегистрировать ошибку LDAP и строку фильтрации.
Спасибо за быстрый ответ!!!
Ошибка при поиске DN пользователя
Пользователь: firstname.lastname
ФИЛЬТР LDAP:
(& (| (samaccountname = firstname.lastname) (cn = firstname.lastname) (uid = firstname.lastname)) (| (objectClass = inetOrgPerson) (objectClass = person) (objectClass = simpleSecurityOb
ject)) (objectCategory = человек))
Пользователь существует в базе поиска?
да. Я могу заставить логин работать, кажется, если я введу DN пользователя, который я тестирую, в качестве базы поиска. Пример:
DN пользователя: CN = имя пользователя, OU = Network_Engineering, OU = Technical_Services, OU = Users, OU =
REP, DC = пример, DC = сеть
База поиска: OU = Network_Engineering, OU = Technical_Services, OU = Users, OU =
REP, DC = пример, DC = сеть
Но если я попробую использовать: DC = example, DC = net
Я получаю такую ошибку:
searchBase ADMIN 10.1.1.33 Ошибка при поиске объектов в базовом DN
ОШИБКА LDAP: ошибка операций (1)
ФИЛЬТР LDAP: (& (| (memberOf = _) (groupMembership = _)) (| (objectClass = inetOrgPerson) (objectClass = person) (objectClass = simpleSecurityObject)))
Кажется, рекурсивный поиск не работает должным образом?
В идеале я хотел бы использовать DC = example, DC = net в качестве базы поиска, поскольку наша среда AD слишком сложна, а пользователи организованы по множеству контейнеров diff и ou.
Да, это должно работать, даже членство во вложенных группах. На самом деле поиск выполняется ADS, поэтому sysPass не выполняет никаких действий при поиске.
Можете ли вы выполнить какой-нибудь тест с помощью утилиты ldp или любой другой утилиты LDAP, используя строку фильтрации?
Здравствуйте, можете ли вы опробовать последнюю фиксацию? Есть несколько исправлений, связанных с LDAP.
Я попробую последний коммит и доложу. Спасибо.
По-прежнему наблюдается та же проблема после обновления до последней фиксации 
Опять таки. Если я наведу базовый поиск туда, где находится DN моего тестового аккаунта, я смогу заставить его работать. В противном случае я не могу авторизоваться. Дайте мне знать, если я могу предоставить дополнительную информацию. Похоже, что это будет работать с простыми настройками, когда все пользователи живут в одном OU. В моем окружении это не так.
OU = Network_Engineering, OU = Technical_Services, OU = Пользователи, OU =
REP, DC = пример, DC = сеть
А как насчет теста ldp? Сможете ли вы выполнить это? Было бы полезно попробовать с внешним инструментом.
В настоящее время эта установка выполняется в среде ADS Windows 2012 без каких-либо проблем, а база поиска настроена на несколько уровней вплоть до пользовательских подразделений.
Я также тестировал его на сервисах openLdap и edirectory.
Я использую ldapsearch на Ubuntu. Не уверен на 100%, как применить указанную выше строку к моему поиску. Я пробую сейчас.
Хорошо. Я перепробовал все фильтры
& (| (samaccountname = firstname.lastname) (cn = firstname.lastname) (uid = firstname.lastname)) (| (objectClass = inetOrgPerson) (objectClass = person) (objectClass = simpleSecurityOb
ject)) (objectCategory = человек))
По-прежнему не работает.
Хорошо…
ldapsearch -x -W -D «bind_dn» -h servername -b «search_base» «строка фильтра внутри ()»
Можете ли вы добавить атрибут cn в конец команды?
Это выглядело бы так: ldapsearch …. «cn»
Таким образом, он вернет только этот атрибут … извините, я должен упомянуть об этом выше
root<strong i="5">@vault</strong>:/opt/apps/syspass# ldapsearch -x -D "CN=_ldap_lookup,OU=ServiceAccounts,OU=Central_IT,DC=example,DC=net" -w "somepass" -h someserver.example.net -b "DC=example,DC=net" "(&(|(samaccountname=firstname.lastname)(cn=firstname.lastname)(uid=firstname.lastname))(|(objectClass=inetOrgPerson)(objectClass=person)(objectClass=simpleSecurityObject))(objectCategory=person))" "cn"
# extended LDIF
#
# LDAPv3
# base <DC=example,DC=net> with scope subtree
# filter: (&(|(samaccountname=firstname.lastname)(cn=firstname.lastname)(uid=firstname.lastname))(|(objectClass=inetOrgPerson)(objectClass=person)(objectClass=simpleSecurityObject))(objectCategory=person))
# requesting: cn
#
# Firstname Lastname, Network_Engineering, Technical_Services, Users, DER, example
.net
dn: CN=Firstname Lastname,OU=Network_Engineering,OU=Technical_Services,OU=Users,OU=
derp,DC=example,DC=net
cn: Firstname Lastname
# search reference
ref: ldap://ForestDnsZones.example.net/DC=ForestDnsZones,DC=example,DC=net
# search reference
ref: ldap://DomainDnsZones.example.net/DC=DomainDnsZones,DC=example,DC=net
# search reference
ref: ldap://example.net/CN=Configuration,DC=example,DC=net
# search result
search: 2
result: 0 Success
# numResponses: 5
# numEntries: 1
# numReferences: 3
Хорошо, поиски работают …
Вы установили пользователя привязки как «cn = user, dc = example, dc = net» ?. Я не вижу этого в некоторых комментариях выше?
Что касается комментария, вы опубликовали ошибку, которая показывает фильтр LDAP, например «memberof = blank», верно?
Текущая привязка
CN = _ldap_lookup, OU = ServiceAccounts, OU = Central_IT, DC = example, DC = net
Ошибка теста
Ошибка при поиске объектов в базовом DN
ОШИБКА LDAP: ошибка операций (1)
ФИЛЬТР LDAP: (& (| (memberOf = _) (groupMembership = _)) (| (objectClass = inetOrgPerson) (objectClass = person) (objectClass = simpleSecurityObject)))
Ошибка входа
Ошибка при поиске DN пользователя
Пользователь: test.user
ОШИБКА LDAP: ошибка операций (1)
ФИЛЬТР LDAP:
(& (| (samaccountname = test.user) (cn = test.user) (uid = test.user)) (| (objectClass = inetOrgPerson) (objectClass = person) (objectClass = simpleSecurityObject)) (objectCa
тегоры = человек))
Блок конфигурации AD
‘ldap_ads’ => правда,
‘ldap_base’ => ‘DC = пример, DC = net’,
‘ldap_bindpass’ => ‘somepass’,
‘ldap_binduser’ => ‘CN = ldapuser, OU = ServiceAccounts, OU = Central_IT, DC = example, DC = net’,
‘ldap_defaultgroup’ => 2,
‘ldap_defaultprofile’ => 2,
‘ldap_enabled’ => правда,
‘ldap_group’ => ложь,
‘ldap_server’ => ‘ldaps: // someip’,
‘ldap_userattr’ => »,
Я это уже выполнил. Я упоминал, что это работает, когда я использую DN тестовых пользователей в качестве основы, поэтому я не думаю, что проблема заключается в сертификате.
Конечно, но эта «ошибка операций» означает, что сервер ADS не отвечает правильно.
Ваш ADS работает под управлением Windows 2003?
Отрывок из PHP:
Для выполнения поиска в Windows 2003 Server Active Directory необходимо установить для параметра LDAP_OPT_REFERRALS значение 0:
ldap_set_option ($ ldap, LDAP_OPT_REFERRALS, 0);
Без этого вы получите «Операционную ошибку», если попытаетесь выполнить поиск по всей схеме AD (используя корень домена как $ base_dn).
В отличие от Windows 2000 Server, где эта опция была необязательной и только увеличивала производительность.
Это конкретный DC 2012 года. Также у меня есть много веб-приложений, которые используют аутентификацию AD с использованием этого DC.
Хорошо, но каков функциональный уровень домена?
Кстати, я программирую фрагмент кода, чтобы получить необработанные данные из ADS с помощью PHP.
Можете ли вы установить группу LDAP на «*» ?. Это заставит тест работать.
Хорошо, но каков функциональный уровень домена?
2008 r2
Можете ли вы установить группу LDAP на «*» ?. Это заставит тест работать.
Я сделаю это сейчас.
Результаты тестирования ниже.
2016-08-30 11:45:49 searchGroupDN ADMIN someip Error while searching group RDN
Group: (cn=*)
LDAP FILTER: (cn=*)
Я ценю помощь с этим. Я бы хотел, чтобы это работало 
Вы также можете взглянуть на http://stackoverflow.com/a/6222836 (LDAP_OPT_REFERRALS закомментирован в скрипте), поэтому кажется, что это может быть полезно для любой версии ADS …
Когда я просматриваю сценарий, я получаю только это
Array
(
)
Можете ли вы прокомментировать строку «LDAP_OPT_REFERRALS»?
Казалось бы, это уже закомментировано?
$groupName = '';
$ldapConn = @ldap_connect($ldapServer);
@ldap_set_option($ldapConn, LDAP_OPT_NETWORK_TIMEOUT, 10); // Set timeout
@ldap_set_option($ldapConn, LDAP_OPT_PROTOCOL_VERSION, 3); // Set LDAP version
//@ldap_set_option($ldapConn, LDAP_OPT_REFERRALS, 0); // Uncomment if "operations error"
@ldap_bind($ldapConn, $bindUser, $bindPass);
preg_match('/^(cn=[\w\s-]+)(,.*)?$/i', $groupName, $groupFilter);
$searchGroup = ldap_get_entries($ldapConn, ldap_search($ldapConn, $searchBase, $groupFilter[1], array("dn", "cn")));
$userFilter = '(memberof:1.2.840.113556.1.4.1941:=' . $searchGroup[0]["dn"] . ')';
$searchUser = ldap_get_entries($ldapConn, ldap_search($ldapConn, $searchBase, $userFilter, array("sAMAccountName")));
echo '<pre>';
print_r($groupFilter);
print_r($searchGroup);
print_r($searchUser);
echo '</pre>';
Извините, я имел в виду раскомментировать …
Эмм … пожалуйста, введите «groupName», потому что скрипт не позаботится о том, чтобы он не был установлен, поэтому он не будет работать.
Вот отрывок из вывода скрипта, конечно, запутанного. Кажется, это работает.
96] => Array
(
[samaccountname] => Array
(
[count] => 1
[0] => firstname.lastname
)
[0] => samaccountname
[count] => 1
[dn] => CN=Firstname Lastname,OU=Application_Development,OU=Technical_Services,OU=Users,OU=EEE,DC=example,DC=net
Отлично !!, можешь попробовать последний коммит?
Абсолютно. Я отчитаюсь. Спасибо.
Вот что у меня есть. Отличие состоит в том, что я больше не получаю ошибку «Неправильный пользователь / пароль». Я также пробовал использовать без ldaps.
Конфиг
‘ldap_ads’ => правда,
‘ldap_base’ => ‘DC = пример, DC = net’,
‘ldap_bindpass’ => ‘somepass’,
‘ldap_binduser’ => ‘CN = ldapuser, OU = ServiceAccounts, OU = Central_IT, DC = example, DC = net’,
‘ldap_defaultgroup’ => 2,
‘ldap_defaultprofile’ => 2,
‘ldap_enabled’ => правда,
‘ldap_group’ => ‘example’, ((( _Также попробовал полное DN группы, как в ldap.php_ )))
‘ldap_server’ => ‘ldaps: // someip’,
‘ldap_userattr’ => »,
Ошибка при входе в систему
Ошибка при поиске RDN группы
Группа: (cn = Groupname)
ФИЛЬТР LDAP: (cn = имя группы)
Ошибка теста
696 30-08-2016 16:54:33 searchGroupDN ADMIN someip Ошибка при поиске RDN группы
Группа: (cn = Group)
ОШИБКА LDAP: ошибка операций (1)
ФИЛЬТР LDAP: (cn = Group)
Также. В выводе ldap.php и мои тесты user samaccountname. У меня есть попытки нескольких пользователей, чтобы быть уверенным.
Что касается ldap.php, есть 3 строки, которые должны выводить некоторую информацию:
Выводит групповой фильтр (строка): print_r ($ groupFilter);
Выводит найденные группы (массив): print_r ($ searchGroup);
Выводит найденных пользователей (массив): print_r ($ searchUser);
Вы видите эти результаты?
Весь вывод, который я вижу, находится в формате ниже, конечно, за исключением первых двух строк.
96] => Array
(
[samaccountname] => Array
(
[count] => 1
[0] => firstname.lastname
)
[0] => samaccountname
[count] => 1
[dn] => CN=Firstname Lastname,OU=Application_Development,OU=Technical_Services,OU=Users,OU=EEE,DC=example,DC=net
Можете ли вы попробовать последний «ldap.php» ?. Я только что обновил его с некоторыми изменениями и полезными комментариями. Важным моментом является «Групповые записи», в котором должна быть указана группа, по которой вы выполняете фильтрацию.
ldap.php
<?php
// Customization - Start
$ldapServer = 'someip';
$bindUser = 'CN=ldapuser,OU=ServiceAccounts,OU=Central_IT,DC=example,DC=net';
$bindPass = 'somepass';
$searchBase = 'DC=example,DC=net';
$groupName = 'CN=example,OU=Security,OU=Groups,OU=Central_IT,DC=example,DC=net'; // Please use DN syntax
// Customization - End
$ldapConn = @ldap_connect($ldapServer);
@ldap_set_option($ldapConn, LDAP_OPT_NETWORK_TIMEOUT, 10); // Set timeout
@ldap_set_option($ldapConn, LDAP_OPT_PROTOCOL_VERSION, 3); // Set LDAP version
@ldap_set_option($ldapConn, LDAP_OPT_REFERRALS, 0); // Uncomment if ADS
@ldap_bind($ldapConn, $bindUser, $bindPass);
preg_match('/^(cn=[\w\s-]+)(,.*)?$/i', $groupName, $groupFilter);
$searchGroup = ldap_get_entries($ldapConn, ldap_search($ldapConn, $searchBase, $groupName, array("dn", "cn")));
$searchGroup = ldap_get_entries($ldapConn, ldap_search($ldapConn, $searchBase, $groupFilter[1], array("dn", "cn")));
$userFilter = '(memberof:1.2.840.113556.1.4.1941:=' . $searchGroup[0]["dn"] . ')';
$searchUser = ldap_get_entries($ldapConn, ldap_search($ldapConn, $searchBase, $userFilter, array("sAMAccountName")));
echo '<pre>';
print_r('Group Filter (regex): ' . $groupFilter);
echo PHP_EOL;
print_r('Group Entries: ' . $searchGroup);
echo PHP_EOL;
print_r('User Filter: ' . $userFilter);
echo PHP_EOL;
print_r('User Entries: ' . $searchUser);
echo '</pre>';
Выход
Group Filter (regex): Array
Group Entries: Array
User Filter: (memberof:1.2.840.113556.1.4.1941:=CN=example,OU=Security,OU=Groups,OU=Central_IT,DC=example,DC=net)
User Entries: Array
Айв также попытался раскомментировать строку 16.
Извините, у меня была ошибка, поэтому массивы не отображались. Уже обновлено …
Один вопрос, включает ли ваша группа числа? Фактически допустимые символы: буквы, «_», «-» и пробелы.
Вывод похож на предыдущий скрипт. Что-нибудь конкретное, что я должен искать? Кроме того, это работает, только если я раскомментирую строку 21.
Вот результат без раскомментирования строки 21.
## Group Filter (regex):
Array
(
[0] => CN=example,OU=Security,OU=Groups,OU=Central_IT,DC=example,DC=net
[1] => CN=example
[2] => ,OU=Security,OU=Groups,OU=Central_IT,DC=example,DC=net
)
## Group Entries:
Array
(
[count] => 0
)
## User Filter:
(memberof:1.2.840.113556.1.4.1941:=)## User Entries:
Array
(
[count] => 0
)
Пожалуйста, задавайте название группы без синтаксиса DN, то есть «пример»
Эммм, это должно быть «cn = example»
Хорошо, это работает. Теперь я вижу имена самаккаунтов.
Я также вижу групповые записи.
## Group Filter (regex):
Array
(
[0] => CN=example
[1] => CN=example
)
## Group Entries:
Array
(
[count] => 16
[0] => Array
(
[cn] => Array
(
[count] => 1
[0] => example
)
[0] => cn
[count] => 1
[dn] => CN=example,OU=Security,OU=Groups,OU=Central_IT,DC=example,DC=net
)
[1] => Array
(
[cn] => Array
(
[count] => 1
[0] => example
)
[0] => cn
[count] => 1
[dn] => CN=example,CN=mail,CN=ypServ30,CN=RpcServices,CN=System,DC=example,DC=net
)
[2] => Array
(
[cn] => Array
(
[count] => 1
[0] => example
)
[0] => cn
[count] => 1
[dn] => CN=example,CN=services,CN=ypServ30,CN=RpcServices,CN=System,DC=example,DC=net
)
[3] => Array
(
[cn] => Array
(
[count] => 1
[0] => example
)
[0] => cn
[count] => 1
[dn] => CN=example,CN=ethers,CN=ypServ30,CN=RpcServices,CN=System,DC=example,DC=net
)
[4] => Array
(
[cn] => Array
(
[count] => 1
[0] => example
)
[0] => cn
[count] => 1
[dn] => CN=example,CN=rpc,CN=ypServ30,CN=RpcServices,CN=System,DC=example,DC=net
)
[5] => Array
(
[cn] => Array
(
[count] => 1
[0] => example
)
[0] => cn
[count] => 1
[dn] => CN=example,CN=netgroup,CN=ypServ30,CN=RpcServices,CN=System,DC=example,DC=net
)
[6] => Array
(
[cn] => Array
(
[count] => 1
[0] => example
)
[0] => cn
[count] => 1
[dn] => CN=example,CN=bootparams,CN=ypServ30,CN=RpcServices,CN=System,DC=example,DC=net
)
[7] => Array
(
[cn] => Array
(
[count] => 1
[0] => example
)
[0] => cn
[count] => 1
[dn] => CN=example,CN=networks,CN=ypServ30,CN=RpcServices,CN=System,DC=example,DC=net
)
[8] => Array
(
[cn] => Array
(
[count] => 1
[0] => example
)
[0] => cn
[count] => 1
[dn] => CN=example,CN=netmasks,CN=ypServ30,CN=RpcServices,CN=System,DC=example,DC=net
)
[9] => Array
(
[cn] => Array
(
[count] => 1
[0] => example
)
[0] => cn
[count] => 1
[dn] => CN=example,CN=hosts,CN=ypServ30,CN=RpcServices,CN=System,DC=example,DC=net
)
[10] => Array
(
[cn] => Array
(
[count] => 1
[0] => example
)
[0] => cn
[count] => 1
[dn] => CN=example,CN=protocols,CN=ypServ30,CN=RpcServices,CN=System,DC=example,DC=net
)
[11] => Array
(
[cn] => Array
(
[count] => 1
[0] => example
)
[0] => cn
[count] => 1
[dn] => CN=example,CN=ypservers,CN=ypServ30,CN=RpcServices,CN=System,DC=example,DC=net
)
[12] => Array
(
[cn] => Array
(
[count] => 1
[0] => example
)
[0] => cn
[count] => 1
[dn] => CN=example,CN=group,CN=ypServ30,CN=RpcServices,CN=System,DC=example,DC=net
)
[13] => Array
(
[cn] => Array
(
[count] => 1
[0] => example
)
[0] => cn
[count] => 1
[dn] => CN=example,CN=shadow,CN=ypServ30,CN=RpcServices,CN=System,DC=example,DC=net
)
[14] => Array
(
[cn] => Array
(
[count] => 1
[0] => example
)
[0] => cn
[count] => 1
[dn] => CN=example,CN=passwd,CN=ypServ30,CN=RpcServices,CN=System,DC=example,DC=net
)
[15] => Array
(
[cn] => Array
(
[count] => 1
[0] => example
)
[0] => cn
[count] => 1
[dn] => CN=example,CN=netid,CN=ypServ30,CN=RpcServices,CN=System,DC=example,DC=net
Хотите, чтобы я попробовал последний коммит?
Да, но приложение не знает, какую группу использовать, поэтому оно выберет первую, потому что ищет имя группы, а не весь dn.
Можете ли вы создать новую группу для входа в sysPass?
Если вы хотите разрешить каждому пользователю в этих группах, это невозможно, потому что приложению придется перебирать каждую группу и получать информацию о том, находится ли в ней пользователь (это требует времени и накладных расходов на сервер). Вместо этого вы можете использовать иерархию групп, то есть создать группу для sysPass, а затем добавить в нее все эти группы.
Кажется, теперь все работает !!!
Тест не пройден, но теперь я могу войти в syspass с указанной группой.
Я очень признателен за терпение и усилия, которые вы приложили, чтобы это исправить.
Я очень рад, что теперь все работает нормально.
Большое спасибо за ваши отзывы и навыки тестирования;)
Была ли эта страница полезной?
0 / 5 — 0 рейтинги