Не удается подключится к OpenVPN серверу с Windows клиента с ошибкой в openvpn.log:
TCP/UDP: Socket bind failed on local address [AF_INET]127.0.0.1:22194: Cannot assign requested address Exiting due to fatal error
Для решения этой проблемы мне приходится перезагружать компьютер или перезапускать службу Service Host: Network Service, что очень неудобно.
Я сталкивался с этой проблемой только когда в качестве протокола подключения к OpenVPN серверу используется TCP. C UDP такой проблемы не было ни разу.
Если проблема возникает, если вы пытаетесь подключиться к нескольким OpenVPN серверам одновременно, проверьте что в Windows установлены несколько виртуальных сетевых адаптера TAP/WinTun (по одному для каждого VPN сеанса, который вы хотите держать активным).
При этом в openvpn.log и/или OpenVPN GUI будет появляться ошибка:
All TAP-Windows/WinTun adapters on this system are currently in use
Если в Windows доступно несколько сетевых адаптеров, проверьте каким процессом/программой занят указанный в ошибке исходящий порт. Можно найти и завершить процесс, который слушает порт с помощью netstat или PowerShell:
- TCP порт:
Get-Process -Id (Get-NetTCPConnection -LocalPort 22194).OwningProcess - UDP порт:
Get-Process -Id (Get-NetUDPEndpoint -LocalPort 22194).OwningProcess
Если указанный порт никем не слушается, возможно, что на компьютере установлены службы Hyper-V или запущена WSL2.
Дело в том, что Windows резервирует определенный динамический диапазон портов TCP для Hyper-V/WSL. Вы можете вывести этот диапазон с помощью команды:
netsh int ipv4 show excludedportrange tcp
Protocol tcp Port Exclusion Ranges Start Port End Port ---------- -------- 5985 5985 47001 47001
Если этот диапазон пересекается с диапазоном исходящих портов клиента OpenVPN, вы получите ошибку:
TCP/UDP: Socket bind failed on local address
Измените диапазон исходящих портов клиента OpenVPN:
- Щелкните правой кнопкой по иконке OpenVPN GUI в трее;
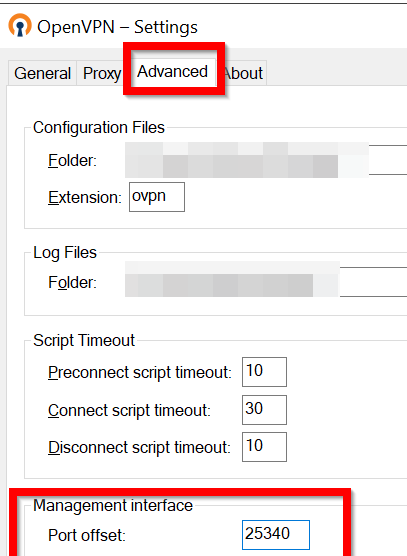
- Выберите Settings -> Advanced -> Management interface, измените значение в поле Port offset чтобы оно не входило в зарезервированный диапазон;
- Сохраните изменения.
После этого вы сможете подключиться к вашем OpenVPN серверу.
Также вы можете задать фиксированный исходящий порт для OpenVPN клиента в конфигурационном файле .ovpn с помощью директивы:
lport 10001
Thank you both. I tried restarting it, stop and start it and configured the server.con file as discussed in the other topic:
Code: Select all
local 192.168.2.16 # SWAP THIS NUMBER WITH YOUR RASPBERRY PI IP ADDRESS
dev tun
proto udp #Some people prefer to use tcp. Don't change it if you don't know.
port 1194
ca /etc/openvpn/easy-rsa/keys/ca.crt
cert /etc/openvpn/easy-rsa/keys/Home.crt # SWAP WITH YOUR CRT NAME
key /etc/openvpn/easy-rsa/keys/Home.key # SWAP WITH YOUR KEY NAME
dh /etc/openvpn/easy-rsa/keys/dh1024.pem # If you changed to 2048, change that here!
server 10.8.0.0 255.255.255.0
# server and remote endpoints
ifconfig 10.8.0.1 10.8.0.2
# Add route to Client routing table for the OpenVPN Server
push "route 10.8.0.1 255.255.255.255"
# Add route to Client routing table for the OpenVPN Subnet
push "route 10.8.0.0 255.255.255.0"
# your local subnet
push "route 192.168.2.0 255.255.255.0" # SWAP THE IP NUMBER WITH YOUR RASPBERRY PI IP ADDRESS
# Set primary domain name server address to the SOHO Router
# If your router does not do DNS, you can use Google DNS 8.8.8.8
push "dhcp-option DNS 192.168.2.245" # This should already match your router address and not need to$
# Override the Client default gateway by using 0.0.0.0/1 and
# 128.0.0.0/1 rather than 0.0.0.0/0. This has the benefit of
# overriding but not wiping out the original default gateway.
push "redirect-gateway def1"
client-to-client
duplicate-cn
keepalive 10 120
tls-auth /etc/openvpn/easy-rsa/keys/ta.key 0
cipher AES-128-CBC
comp-lzo
user nobody
group nogroup
persist-key
persist-tun
status /var/log/openvpn-status.log 20
log /var/log/openvpn.log
verb 5This is my client log
Code: Select all
2016-02-10 18:44:36 *Tunnelblick: openvpnstart starting OpenVPN
2016-02-10 18:44:36 *Tunnelblick: OS X 10.11.3; Tunnelblick 3.5.5 (build 4270.4461)
2016-02-10 18:44:36 *Tunnelblick: Attempting connection with Bas1; Set nameserver = 1; monitoring connection
2016-02-10 18:44:36 *Tunnelblick: openvpnstart start Bas1.tblk 1338 1 0 3 0 16688 -ptADGNWradsgnw 2.3.6
2016-02-10 18:44:38 *Tunnelblick: openvpnstart log:
OpenVPN started successfully. Command used to start OpenVPN (one argument per displayed line):
/Applications/Tunnelblick.app/Contents/Resources/openvpn/openvpn-2.3.6/openvpn
--daemon
--log
/Library/Application Support/Tunnelblick/Logs/-SLibrary-SApplication Support-STunnelblick-SShared-SBas1.tblk-SContents-SResources-Sconfig.ovpn.1_0_3_0_16688.1338.openvpn.log
--cd
/Library/Application Support/Tunnelblick/Shared/Bas1.tblk/Contents/Resources
--config
/Library/Application Support/Tunnelblick/Shared/Bas1.tblk/Contents/Resources/config.ovpn
--cd
/Library/Application Support/Tunnelblick/Shared/Bas1.tblk/Contents/Resources
--management
127.0.0.1
1338
--management-query-passwords
--management-hold
--script-security
2
--up
/Applications/Tunnelblick.app/Contents/Resources/client.up.tunnelblick.sh -d -f -m -w -ptADGNWradsgnw
--down
/Applications/Tunnelblick.app/Contents/Resources/client.down.tunnelblick.sh -d -f -m -w -ptADGNWradsgnw
2016-02-10 18:44:37 OpenVPN 2.3.6 x86_64-apple-darwin [SSL (OpenSSL)] [LZO] [PKCS11] [MH] [IPv6] built on Dec 4 2015
2016-02-10 18:44:37 library versions: OpenSSL 1.0.1q 3 Dec 2015, LZO 2.08
2016-02-10 18:44:38 *Tunnelblick: Established communication with OpenVPN
2016-02-10 18:44:38 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
2016-02-10 18:44:44 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
2016-02-10 18:44:44 Control Channel Authentication: tls-auth using INLINE static key file
2016-02-10 18:44:44 UDPv4 link local: [undef]
2016-02-10 18:44:44 UDPv4 link remote: [AF_INET]MYINETIP:1194
2016-02-10 18:44:51 [Home] Peer Connection Initiated with [AF_INET]MYINETIP:1194
2016-02-10 18:44:53 Opening utun (connect(AF_SYS_CONTROL)): Resource busy
2016-02-10 18:44:53 Opened utun device utun1
2016-02-10 18:44:53 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
2016-02-10 18:44:53 /sbin/ifconfig utun1 delete
ifconfig: ioctl (SIOCDIFADDR): Can't assign requested address
2016-02-10 18:44:53 NOTE: Tried to delete pre-existing tun/tap instance -- No Problem if failure
2016-02-10 18:44:53 /sbin/ifconfig utun1 10.8.0.6 10.8.0.5 mtu 1500 netmask 255.255.255.255 up
2016-02-10 18:44:53 /Applications/Tunnelblick.app/Contents/Resources/client.up.tunnelblick.sh -d -f -m -w -ptADGNWradsgnw utun1 1500 1558 10.8.0.6 10.8.0.5 init
**********************************************
Start of output from client.up.tunnelblick.sh
Retrieved from OpenVPN: name server(s) [ 192.168.2.245 ], search domain(s) [ ] and SMB server(s) [ ] and using default domain name [ openvpn ]
Not aggregating ServerAddresses because running on OS X 10.6 or higher
Setting search domains to 'openvpn' because running under OS X 10.6 or higher and the search domains were not set manually and 'Prepend domain name to search domains' was not selected
Saved the DNS and SMB configurations so they can be restored
Changed DNS ServerAddresses setting from '172.20.10.1' to '192.168.2.245'
Changed DNS SearchDomains setting from '' to 'openvpn'
Changed DNS DomainName setting from '' to 'openvpn'
Did not change SMB NetBIOSName setting of ''
Did not change SMB Workgroup setting of ''
Did not change SMB WINSAddresses setting of ''
DNS servers '192.168.2.245' will be used for DNS queries when the VPN is active
The DNS servers do not include any free public DNS servers known to Tunnelblick. This may cause DNS queries to fail or be intercepted or falsified even if they are directed through the VPN. Specify only known public DNS servers or DNS servers located on the VPN network to avoid such problems.
Flushed the DNS cache via dscacheutil
/usr/sbin/discoveryutil not present. Not flushing the DNS cache via discoveryutil
Notified mDNSResponder that the DNS cache was flushed
Setting up to monitor system configuration with process-network-changes
End of output from client.up.tunnelblick.sh
**********************************************
add net MYINETIP: gateway 172.20.10.1
add net 0.0.0.0: gateway 10.8.0.5
add net 128.0.0.0: gateway 10.8.0.5
add net 10.8.0.1: gateway 10.8.0.5
add net 10.8.0.0: gateway 10.8.0.5
add net 192.168.2.0: gateway 10.8.0.5
route: writing to routing socket: File exists
add net 10.8.0.0: gateway 10.8.0.5: File exists
2016-02-10 18:44:57 Initialization Sequence Completed
2016-02-10 18:44:57 *Tunnelblick: No 'connected.sh' script to execute
2016-02-10 18:45:01 *Tunnelblick process-network-changes: A system configuration change was ignored
2016-02-10 18:45:38 *Tunnelblick: After 30.0 seconds, gave up trying to fetch IP address information using the ipInfo host's name after connecting.
2016-02-10 18:46:14 *Tunnelblick: After 30.0 seconds, gave up trying to fetch IP address information using the ipInfo host's IP address after connecting.This is my openvpn log file:
Code: Select all
Wed Feb 10 17:44:30 2016 us=502949 Data Channel MTU parms [ L:1558 D:1450 EF:58 EB:135 ET:0 EL:0 AF:3/1 ]
Wed Feb 10 17:44:30 2016 us=507340 GID set to nogroup
Wed Feb 10 17:44:30 2016 us=507743 UID set to nobody
Wed Feb 10 17:44:30 2016 us=507874 UDPv4 link local (bound): [AF_INET]192.168.2.16:1194
Wed Feb 10 17:44:30 2016 us=507966 UDPv4 link remote: [undef]
Wed Feb 10 17:44:30 2016 us=508054 MULTI: multi_init called, r=256 v=256
Wed Feb 10 17:44:30 2016 us=508555 IFCONFIG POOL: base=10.8.0.4 size=62, ipv6=0
Wed Feb 10 17:44:30 2016 us=508807 Initialization Sequence Completed
Wed Feb 10 17:44:42 2016 us=356277 MULTI: multi_create_instance called
Wed Feb 10 17:44:42 2016 us=356828 143.179.67.21:21832 Re-using SSL/TLS context
Wed Feb 10 17:44:42 2016 us=357110 143.179.67.21:21832 LZO compression initialized
Wed Feb 10 17:44:42 2016 us=358474 143.179.67.21:21832 Control Channel MTU parms [ L:1558 D:166 EF:66 EB:0 ET:0 EL:0 ]
Wed Feb 10 17:44:42 2016 us=358631 143.179.67.21:21832 Data Channel MTU parms [ L:1558 D:1450 EF:58 EB:135 ET:0 EL:0 AF:3/1 ]
Wed Feb 10 17:44:42 2016 us=359015 143.179.67.21:21832 Local Options String: 'V4,dev-type tun,link-mtu 1558,tun-mtu 1500,proto UDPv4,comp-lzo,keydir 0,cipher AES-128-CBC,auth SHA1,keysize 128,tls-auth,ke$
Wed Feb 10 17:44:42 2016 us=359108 143.179.67.21:21832 Expected Remote Options String: 'V4,dev-type tun,link-mtu 1558,tun-mtu 1500,proto UDPv4,comp-lzo,keydir 1,cipher AES-128-CBC,auth SHA1,keysize 128,t$
Wed Feb 10 17:44:42 2016 us=359305 143.179.67.21:21832 Local Options hash (VER=V4): 'a2e63101'
Wed Feb 10 17:44:42 2016 us=359452 143.179.67.21:21832 Expected Remote Options hash (VER=V4): '272f1b58'
RWed Feb 10 17:44:42 2016 us=359723 143.179.67.21:21832 TLS: Initial packet from [AF_INET]143.179.67.21:21832, sid=70fa9e45 a6252187
Wed Feb 10 17:44:48 2016 us=784925 143.179.67.21:21832 VERIFY OK: depth=1, C=US, ST=CA, L=Sa$
Wed Feb 10 17:44:48 2016 us=786804 143.179.67.21:21832 VERIFY OK: depth=0, C=US, ST=CA, L=SanFrancisco, O=Fort-Funston, OU=MyOrganizationalUnit, CN=Bas1, name=EasyRSA, emailAddress=me@myhost.mydomain
Wed Feb 10 17:44:48 2016 us=925449 143.179.67.21:21832 Data Channel Encrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Wed Feb 10 17:44:48 2016 us=925644 143.179.67.21:21832 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Wed Feb 10 17:44:48 2016 us=925749 143.179.67.21:21832 Data Channel Decrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Wed Feb 10 17:44:48 2016 us=925855 143.179.67.21:21832 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
WWWRRRWed Feb 10 17:44:49 2016 us=3012 143.179.67.21:21832 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 1024 bit RSA
Wed Feb 10 17:44:49 2016 us=3232 143.179.67.21:21832 [Bas1] Peer Connection Initiated with [AF_INET]143.179.67.21:21832
Wed Feb 10 17:44:49 2016 us=3425 Bas1/143.179.67.21:21832 MULTI_sva: pool returned IPv4=10.8.0.6, IPv6=(Not enabled)
Wed Feb 10 17:44:49 2016 us=3760 Bas1/143.179.67.21:21832 MULTI: Learn: 10.8.0.6 -> Bas1/143.179.67.21:21832
Wed Feb 10 17:44:49 2016 us=3873 Bas1/143.179.67.21:21832 MULTI: primary virtual IP for Bas1/143.179.67.21:21832: 10.8.0.6
RWed Feb 10 17:44:51 2016 us=99827 Bas1/143.179.67.21:21832 PUSH: Received control message: 'PUSH_REQUEST'
Wed Feb 10 17:44:51 2016 us=100002 Bas1/143.179.67.21:21832 send_push_reply(): safe_cap=940
Wed Feb 10 17:44:51 2016 us=100330 Bas1/143.179.67.21:21832 SENT CONTROL [Bas1]: 'PUSH_REPLY,route 10.8.0.1 255.255.255.255,route 10.8.0.0 255.255.255.0,route 192.168.2.0 255.255.255.0,dhcp-option DNS 19
Wed Feb 10 17:50:59 2016 us=38875 Bas1/143.179.67.21:21832 SIGUSR1[soft,ping-restart] received, client-instance restarting
This is my /etc/network/interfaces file:
Code: Select all
# interfaces(5) file used by ifup(8) and ifdown(8)
# Please note that this file is written to be used with dhcpcd
# For static IP, consult /etc/dhcpcd.conf and 'man dhcpcd.conf'
# Include files from /etc/network/interfaces.d:
source-directory /etc/network/interfaces.d
auto lo
iface lo inet loopback
iface eth0 inet manual
pre-up /etc/firewall-openvpn-rules.sh
allow-hotplug wlan0
iface wlan0 inet manual
wpa-conf /etc/wpa_supplicant/wpa_supplicant.conf
allow-hotplug wlan1
iface wlan1 inet manual
wpa-conf /etc/wpa_supplicant/wpa_supplicant.conf
This is my /etc/firewall-openvpn-rules.sh file
Code: Select all
#!/bin/sh
iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth0 -j SNAT --to-source 192.168.2.16What is the best way to go now?
thx!
I’m suddenly getting this error on this version, for every VPN config I try:
The log shows this:
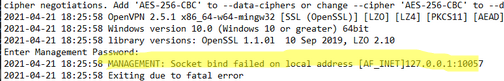
2021-04-20 18:39:23 DEPRECATED OPTION: --cipher set to 'AES-256-CBC' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM). Future OpenVPN version will ignore --cipher for cipher negotiations. Add 'AES-256-CBC' to --data-ciphers or change --cipher 'AES-256-CBC' to --data-ciphers-fallback 'AES-256-CBC' to silence this warning.
2021-04-20 18:39:23 OpenVPN 2.5.1 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Feb 24 2021
2021-04-20 18:39:23 Windows version 10.0 (Windows 10 or greater) 64bit
2021-04-20 18:39:23 library versions: OpenSSL 1.1.1j 16 Feb 2021, LZO 2.10
Enter Management Password:
2021-04-20 18:39:23 MANAGEMENT: Socket bind failed on local address [AF_INET]127.0.0.1:25459
2021-04-20 18:39:23 Exiting due to fatal error
I have tried changing the port in the settings tab, but I still always get the same error.
Anyone have any ideas?
If changing port offset by small values leads to similar error, there could be some running process that reserves a large swath of ports in that range. If so, change the port offset to be well out that range. Some one else had reported a third party app that opens a large number of ports in the 25000 to 26000 range.
Also make sure stale openvpn.exe processes are not getting left behind due to some other issue. That could lead to errors like this on attempting to restart the connection. Check running processes using task manager.
@selvanair ty for helping. I can’t seem t o find why OVPN GUI thinks that/those ports are taken?
I just did a complete uninstall using IOBit Uninsttaller, that also does a scan for anything leftover in the registry, etc., double-checked to make sure that no openvpn services were leftover, and then installed this:
http://build.openvpn.net/downloads/snapshots/openvpn-install-2.5.1-I900-release-2.5-20210420113725-8a06459d.exe
Tried to connect with a previously working .ovpn file and still got the same error:
2021-04-21 18:08:01 DEPRECATED OPTION: --cipher set to 'AES-256-CBC' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM). Future OpenVPN version will ignore --cipher for cipher negotiations. Add 'AES-256-CBC' to --data-ciphers or change --cipher 'AES-256-CBC' to --data-ciphers-fallback 'AES-256-CBC' to silence this warning.
2021-04-21 18:08:01 OpenVPN 2.5.1 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Apr 20 2021
2021-04-21 18:08:01 Windows version 10.0 (Windows 10 or greater) 64bit
2021-04-21 18:08:01 library versions: OpenSSL 1.1.0l 10 Sep 2019, LZO 2.10
Enter Management Password:
2021-04-21 18:08:01 MANAGEMENT: Socket bind failed on local address [AF_INET]127.0.0.1:25340
2021-04-21 18:08:01 Exiting due to fatal error
Then I looked at all current ports using Nirsoft Curports, and there’s nothing using port 25340, or anything even near the 25000 range.:
I also just changed the port to 9999, double-checked curports to make sure 9999 wasn’t in use, and same error. Although looking at the log it’s not even trying to use the port that I specified:
I’m at a loss here as to what could be the issue?
This is baffling. As snapshots are largely untested, can you try the latest release from [here] (https://openvpn.net/community-downloads/) ?
I suppose you have interactive service running so that the GUI can be run as limited user? That’s not critical, but good to know there are no unusual things going on.
To narrow this down, could you directly start openvpn from a command prompt? Open a cmd window, cd to the folder where the config is and run, say,
C:\Program Files\OpenVPN\bin\openvpn.exe —config Johannesburg01.ovpn —management localhost 25340
That will not fully succeed because of limited user privileges, but we can check whether it shows the same error. If the config has a log file specified in it, you may have to do a Ctrl-C and open the log file to check. Else the logs will appear on the terminal.
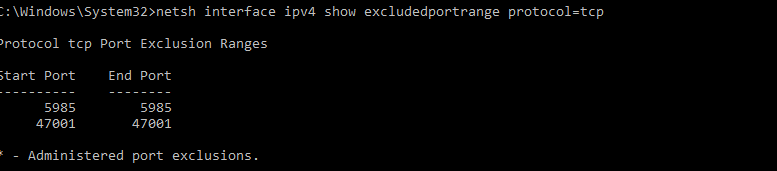
Also check any excluded ports using
netsh int ipv4 show excludedportrange tcp
This is baffling. As snapshots are largely untested, can you try the latest release from [here] (https://openvpn.net/community-downloads/) ?
Ok, I uninstalled the snapshot and installed from the page you linked:
https://swupdate.openvpn.org/community/releases/OpenVPN-2.5.2-I601-amd64.msi
Unfortunately I got the same error.
I suppose you have interactive service running so that the GUI can be run as limited user? That’s not critical, but good to know there are no unusual things going on.
I just let the installer set up the service however it wanted:
To narrow this down, could you directly start openvpn from a command prompt? Open a cmd window, cd to the folder where the config is and run, say,
C:\Program Files\OpenVPN\bin\openvpn.exe —config Johannesburg01.ovpn —management localhost 25340
That will not fully succeed because of limited user privileges, but we can check whether it shows the same error. If the config has a log file specified in it, you may have to do a Ctrl-C and open the log file to check. Else the logs will appear on the terminal.
Here is the result of running from a command-line:
Also check any excluded ports using
netsh int ipv4 show excludedportrange tcp
Looking about midway through that screenshot it looks like the range 25302-25401 is excluded? Does this mean any port within that range can’t be used? If so, how do I find what might be causing them to be blocked from use?
Another question; does the computer need to be rebooted between each of these installations? I don’t see any notice from the installer saying to do so, so I haven’t been.
Yes, default install will setup the service and start it. Reboot is not required except in some situations where the installation would prompt for it if required.
The reservation list shows 25102 to 25901 are reserved and that is causing the error. I do not know how to find what is doing it. Apparently hyperv and docker is know to reserve large ranges though no idea whether this range is common. You could probably remove it using «netsh int ipv4 delete excludedportrange …. » command and then do an «administrative» reservation for your own use. Well-behaved programs will notice it and change their reservation when restarted. But that would require first stopping the offending program or use some registry edits and reboot. I don’t know.
An easier option may be to find a range that is free, add an administrative exclusion like
netsh int ipv4 add excludedportrange tcp 45000 50
and then set the offset to 45000 in the GUI settings.
To copy text from a command prompt, simply highlight the text with your mouse and then press Enter.
You can then paste the text into Notepad.
Well, I might be onto something but not sure what or why, lol.
Using that excluded ports command I got a massive list: https://pastebin.com/b9Hz0WEx
Then I looked at the very top and it says that port 1063 shouldn’t be excluded; confirmed it wasn’t in use with CurPorts and it wasnt; set t hat port in OpenGUI settings and got the same error. The log said it was trying 1064. So thinking that OGUI adds 1 port to anything I set in it, I set the port in it to 1062. THAT connected!
But looking in CurPorts, it literally connected to port 1062 instead of adding 1 port.
So it looks like an issue with excluded ports, but I have NO idea why my list would be THAT HUGE. Also, I don’t understand why OGUI doesn’t just use the specified port every single time rather than adding port numbers? If the idea is to start at the given port, and keep attempting at ports that’ll connect by adding 1 port at a time, it seems like it should still find a port when set to port 1063?
To copy text from a command prompt, simply highlight the text with your mouse and then press Enter.
You can then paste the text into Notepad.
I know, but I figured a screenshot would be fine in this case.
So it looks like an issue with excluded ports, but I have NO idea why my list would be THAT HUGE. Also, I don’t understand why OGUI doesn’t just use the specified port every single time rather than adding port numbers? If the idea is to start at the given port, and keep attempting at ports that’ll connect by adding 1 port at a time, it seems like it should still find a port when set to port 1063?
The number you specify in the settings is an offset. The index of the config is added to that number to find the port to use. configs are generally alphabetically indexed but its a bit more complex [*] than that so not that easy to predict the port number especially if you have many configs. Its not random though. This logic is not perfect and the actual port used could span over a wide range if there are 100’s of configs. Yet, its somewhat predictable 
The port offset + config index is used as is — no attempt is made at finding an unused port as that’s not possible the way openvpn works. The GUI has to pick the port and openvpn core has to bind to it. Otherwise we would have used dynamic ports and avoided this issue altogether.
[*] User configs are scanned first, global configs after that and Windows has a mind of its own how it orders directory traversal when recursing into sub directories.
To copy text from a command prompt, simply highlight the text with your mouse and then press Enter.
You can then paste the text into Notepad.I know, but I figured a screenshot would be fine in this case.
If I get my magnifying glass out then I can just about read it, although it is not exactly clear.
You list yourself as «Girl Coder», so hopefully my gentle nudge will make you a better coder in future 
If I get my magnifying glass out then I can just about read it, although it is not exactly clear.
ProTip: Click the image. 
To copy text from a command prompt, simply highlight the text with your mouse and then press Enter.
You can then paste the text into Notepad.I know, but I figured a screenshot would be fine in this case.
If I get my magnifying glass out then I can just about read it, although it is not exactly clear.
You list yourself as «Girl Coder», so hopefully my gentle nudge will make you a better coder in future
If you are trying to read her username and password, its not just you — it has been blanked out. Don’t blame your glasses 
So it looks like an issue with excluded ports, but I have NO idea why my list would be THAT HUGE. Also, I don’t understand why OGUI doesn’t just use the specified port every single time rather than adding port numbers? If the idea is to start at the given port, and keep attempting at ports that’ll connect by adding 1 port at a time, it seems like it should still find a port when set to port 1063?
The number you specify in the settings is an offset. The index of the config is added to that number to find the port to use. configs are generally alphabetically indexed but its a bit more complex [*] than that so not that easy to predict the port number especially if you have many configs. Its not random though. This logic is not perfect and the actual port used could span over a wide range if there are 100’s of configs. Yet, its somewhat predictable
I know this can benefit from some improvement.
The port offset + config index is used as is — no attempt is made at finding an unused port as that’s not possible the way openvpn works. The GUI has to pick the port and openvpn core has to bind to it. Otherwise we would have used dynamic ports and avoided this issue altogether.
[*] User configs are scanned first, global configs after that and Windows has a mind of its own how it orders directory traversal when recursing into sub directories.
Ok, thank you again for helping me sort this all out. 
At least I’m back in business again and able to connect, lol.
One last quick one, that I don’t know if I should just toss in here real quick or start up a whole new issue for?
Is there a quick 1-liner I need to add to my .ovpn file to fix that «DEPRECATED OPTION:» notice w/out fully disabling the cipher, or lowering it to 128?
From my searches I’m only able to find command-line flags to use (rather than the line for a config file), and also they basically give a line that disables the cipher.
@YouveGotMeowxy Pro-tip: A Pro never print-screens a DOS prompt. 🏁
A pro uses whatever tool is available to get the job effectively done; you’re only a click away from seeing the same result as a copy/paste. 
A Pro chooses to use the correct tools to explain the problem clearly to their intended audience.
I’ll leave it there because I don’t want to start a war — Sorry for the intrusion.
Please accept my apologies for any inadvertent offence, that was not my intention.
A Pro chooses to use the correct tools to explain the problem clearly to their intended audience.
I’ll leave it there because I don’t want to start a war — Sorry for the intrusion.
Please accept my apologies for any inadvertent offence, that was not my intention.
A screenshot is a correct tool to explain. That’s why there are hundreds of screenshot utilities, as well as millions of screenshots all over the internet on tutorial pages. 
Apology accepted, no offense taken. 
Is there a quick 1-liner I need to add to my .ovpn file to fix that «DEPRECATED OPTION:» notice w/out fully disabling the cipher, or lowering it to 128?
One liner would be to replace «cipher» by «data-ciphers-fallback». But read on.
Assuming your server supports ncp, the cipher is negotiated and AES-256-GCM or AES-128-GCM may be getting selected (check the logs). If so the cipher you are specifying is only a fallback. In 2.5, the preferred way to do that is using —data-ciphers-fallback instead of —cipher. The deprecation message does indicate that as one of the ways of fixing it.
Command line options are the same as what goes into the config file except config file also supports inline certs and keys etc. And, the starting «—» is required on command-line but optional in the config file. So you could write
—data-ciphers-fallback AES-256-CBC
or
data-ciphers-fallback AES-256-CBC
The latter form is generally preferred in the config file, but nothing wrong with the former.
As the former form with «—» is required on command line, that’s how its generally described in documentation and logs.
P.S. Be careful and do check the logs to see what cipher is negotiated after you make changes.
@selvanair ok, tyvm for everything! It looks like the original problem is due to Hyper-V reserving all those ports, and not the fault of OpenVPN/GUI, so I’ll leave it up to you whether or not to Close the issue; I’ll go digging into why and how to stop MS from totally owning my puter, once again, lol. 
Os there a fix for detecting an avoiding the excluded ports in the code? (or informing the user of the issue and the setting to change)
As mentioned in the top of this thread, the user can change the port offset in the settings menu (see the Advanced tab) — defaults tot 25340. The port used would be the offset + ordinal index of the config. If you have, say, 3 config files, they are indexed 0, 1, 2.
Recently we have added code to also check whether the port is free and find an alternate port if not (PR #509). Hopefully that will work transparently to the user. Will be in the next release.
Thanks, that would help. (Port numbers is not something that most users would understand)
The excluded ports are a mess — they change randomly with reboots and the error messages did not make it obvious that that is what is going on. (Some other applications sometimes use hard-coded ports which means that they break until you reboot) (I have Hyper-V installed, with one VM created that is not running. I do have WSL1 as well, not sure if that also affects the excluded ports)
(It also doesn’t help that the classic troubleshooting of checking what is listening on the port also fails for the excluded ports)
I ran into the same problem but didn´t check if the port was on an excluded range. After restarting the «Host Network Service» the problem was gone.
It’s not a fix but is faster than multiple restarts of the machine.
gian110 reacted with heart emoji
If you’re reading this in 2019 and using Ubuntu 16.x or 18.x, especially if you’re running multiple IPs, a libvirt/kvm host, or expect that your OpenVPN instance only listen on a single specified port, and are encountering the following error:
Socket bind failed on local address [AF_INET]XXX.XXX.XXX.XXX:10e94: Cannot assign requested address
All of the other answers are incorrect or poor solutions, the correct solution is to:
In /etc/default/openvpn
AUTOSTART="none"
In /etc/network/interfaces
iface ethX inet static
address XXX.XXX.XXX.XX
netmask 255.255.255.0
openvpn my_vpn_name
Where ethX is your interface (ex, eth0 for a regular interface, eth0:1 for an alias of an interface), my_vpn_name is the base filename without the .conf suffix of your /etc/openvpn/my_vpn_name.conf file.
To explain, the above causes the script /etc/network/if-up.d/openvpn to get executed, this in turn executes systemctl —no-block start openvpn@my_vpn_name which starts the openvpn after the interfeace or alias is brought up.
Why do I say the other answers are poor or incorrect? because they’re either unnecessarily complex or require you to instruct your openvpn instance to listen on all IPs which is highly undesireable for obvious reasons.
I am on Windows 10 21H1, and I use OpenVPN to connect to office.
Sometimes I ran into this error:
MANAGEMENT: Socket bind failed on local address [AF_INET]127.0.0.1:25340
When it happens, I can find a line indicating that the port is in the exclusion range, like blow.
PS C:\> netsh interface ipv4 show excludedportrange protocol=tcp
Protocol tcp Port Exclusion Ranges
Start Port End Port
---------- --------
25305 25404
There are many ranges, I have omitted them.
I know this error is related to Hyper-V (https://superuser.com/a/1586869/614603), but I need WSL2, which is based on Hyper-V. Besides, I don’t want to change dynamic TCP port range since I run many things 
I am wondering if I can change the local port or port range used by OpenVPN.