Skip to content
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and
privacy statement. We’ll occasionally send you account related emails.
Already on GitHub?
Sign in
to your account
Assignees
Labels
Enhancement
A new feature or improvement to an existing feature.
Help Wanted
We would love to have help on this issue! This may be a good issue for first time contributors.
I have the same NLA Error 2825.
It’s a clean install so don’t know if this scenario worked previous to the update.
mRemoteNG v1.75.7012.16814
Windows 10 1709 OS Build 16299.248
Happy to test an update/fix.
Thanks.
Do you have Use CredSSP enabled for that connection (Protocol section in the config window)?
Hi David
No, CredSSP is off.
CredSSP is enabled on the computers on the domain of today’s client, and I think on the others I manage. (And has been for a long time, predating this problem.) But it’s not enabled in mRemoteNG.
My computer is not a domain member, so CredSSP won’t work even if enabled…but should not cause a problem. It doesn’t bother MSTSC.
Thanks!
…
—
Jeff Vandervoort
Crescent IT Systems
From: David Sparer [mailto:notifications@github.com]
Sent: Wednesday, February 14, 2018 2:53 PM
To: mRemoteNG/mRemoteNG <mRemoteNG@noreply.github.com>
Cc: Jeff Vandervoort <jvandervoort@crescent-systems.com>; Author <author@noreply.github.com>
Subject: Re: [mRemoteNG/mRemoteNG] NLA error 2825 (#875)
Do you have Use CredSSP enabled for that connection (Protocol section in the config window)?
—
You are receiving this because you authored the thread.
Reply to this email directly, view it on GitHub<#875 (comment)>, or mute the thread<https://github.com/notifications/unsubscribe-auth/AiVu_Pbrm44HGd0tr82Ax8Y3bfWf9EGBks5tU0eigaJpZM4R0VgX>.
I would recommend attempting a connection from mRemoteNG with CredSSP turned on. According to the CredSSP protocol specification, the client and sever do not need to be on the same domain for the protocol to work. All it does is provide a TLS connection during authentication and help with selecting an authentication protocol that both hosts support.
I admit it seems odd that this issue cropped up after updating mremoteng though.
Wow, David, you’re absolutely right. It worked.
From an admin’s perspective, CredSSP’s purpose in life is Single Sign-On, so the user doesn’t have to log on to the RD session. For that to work, the RDSH and the client have to be members of the same domain, because the client passes the user’s logon credentials to the RDSH, which then has to have its DC authenticate them. So I would not have thought it needed to be turned on.
In fact, by default, CredSSP is DISABLED on RDSH’s. It requires a registry edit or GPO to enable. That makes it even more surprising that this would make any difference. But maybe what’s disabled on the server is the auth piece and not the protocol piece.
So, problem solved, and I learned something.
Maybe I disabled CredSSP at the same time as I did the upgrade. And then when I did the clean install, it was either off by default or I turned it off. Too many weeks have gone by to know, now.
Thanks!
…
—
Jeff Vandervoort
Crescent IT Systems
From: David Sparer [mailto:notifications@github.com]
Sent: Wednesday, February 14, 2018 4:17 PM
To: mRemoteNG/mRemoteNG <mRemoteNG@noreply.github.com>
Cc: Jeff Vandervoort <jvandervoort@crescent-systems.com>; Author <author@noreply.github.com>
Subject: Re: [mRemoteNG/mRemoteNG] NLA error 2825 (#875)
I would recommend attempting a connection from mRemoteNG with CredSSP turned on. According to the CredSSP protocol specification, the client and sever do not need to be on the same domain for the protocol to work. All it does is provide a TLS connection during authentication and help with selecting an authentication protocol that both hosts support.
I admit it seems odd that this issue cropped up after updating mremoteng though.
—
You are receiving this because you authored the thread.
Reply to this email directly, view it on GitHub<#875 (comment)>, or mute the thread<https://github.com/notifications/unsubscribe-auth/AiVu_I1la_cSwq_ALCObcaj5mvLqlRi1ks5tU1tDgaJpZM4R0VgX>.
Hi David, I concur this works. I had tried with CredSSP in both states but this was combined with bad credentials so confused the result.
Thanks for your prompt suggestion.
Simon.
Glad to hear that worked for both of you. I learned something as well — had to do a bit of digging to figure out what credssp was really doing for us.
I’ve created issue #885 to look into improving the error message for rdp error 2825.
David, it’s more than an error message problem. NLA and CredSSP are two different things.
I’m a little rusty now, but RDS was my life a few years ago, and I still support a small RDS infrastructure for one of my clients.
NLA is the feature that prompts for credentials on the client instead of using the GINA on the server. It functions whether you’re passing creds from Windows (CredSSP), using stored creds from mRemoteNG, or typing them. MSTSC requests NLA unless otherwise set in a custom RDP file, and if the RDSH accepts (or requires) NLA, is capable of using it. If the RDSH doesn’t accept NLA, MSTSC falls back to using the RDSH’s GINA for authentication.
CredSSP uses NLA to pass credentials from Windows and won’t function without NLA. CredSSP is disabled by default in MSTSC, and if you want to use it, it must be enabled through a custom RDP file. It’s most often used for RemoteApps in order to provide a UX similar to running a program locally. CredSSP falls back to prompting for credentials if Windows credentials don’t work.
I don’t have visibility into what’s happening under the hood. But empirically, it looks like “Use CredSSP” in mRemoteNG is enabling/disabling client-side NLA AND client-side CredSSP. It should only be enabling/disabling CredSSP. To duplicate functionality of MSTSC v6+, there should NEVER be a time when mRemoteNG, can’t authenticate by NLA if the RDSH supports it, regardless of the “Use CredSSP” setting. With “Use CredSSP” turned on, Windows is ALSO trying to log on with local creds, but that’s harmless. If Windows creds fail, NLA will fall back to mRemoteNG creds, and finally, the credential prompt. We shouldn’t HAVE to enable it to use mRemoteNG, but it won’t hurt anything if we do.
HTH
…
—
Jeff Vandervoort
Crescent IT Systems
From: David Sparer [mailto:notifications@github.com]
Sent: Wednesday, February 14, 2018 5:21 PM
To: mRemoteNG/mRemoteNG <mRemoteNG@noreply.github.com>
Cc: Jeff Vandervoort <jvandervoort@crescent-systems.com>; Author <author@noreply.github.com>
Subject: Re: [mRemoteNG/mRemoteNG] NLA error 2825 (#875)
Glad to hear that worked for both of you. I learned something as well — had to do a bit of digging to figure out what credssp was really doing for us.
I’ve created issue #885<#885> to look into improving the error message for rdp error 2825.
—
You are receiving this because you authored the thread.
Reply to this email directly, view it on GitHub<#875 (comment)>, or mute the thread<https://github.com/notifications/unsubscribe-auth/AiVu_KhtTzNgPCDIeqxNUrZA-kGu2wM7ks5tU2pwgaJpZM4R0VgX>.
The only AxMstsc property we set based on the Use CredSsp value is _rdpClient.AdvancedSettings7.EnableCredSspSupport (RdpProtocol.cs:151). Related documentation page here: https://msdn.microsoft.com/en-us/library/gg130858(v=vs.85).aspx
The only somewhat related value seems to be _rdpClient.AdvancedSettings5.AuthenticationLevel (RdpProtocol.cs:143) which we currently hardcode to 0. Related documentation here: https://msdn.microsoft.com/en-us/library/aa380846(v=vs.85).aspx. Though this seems to be more about authenticating that the server is valid via certs than requesting creds from a client.
I cant find any property that specifically references NLA.
It may be that the AxMstsc library lacks the distinction between CredSSP and NLA.
OK, thanks for the followup, David. That’s interesting. Yes the authentication level does sound like the MSTSC feature where it pops up a security warning if it doesn’t trust the RDSH.
Then, I guess all you can do is change the help text. It does mean that mRemoteNG won’t ever behave like MSTSC does, but that’s on MS.
Thanks!
…
—
Jeff Vandervoort
Crescent IT Systems
From: David Sparer [mailto:notifications@github.com]
Sent: Thursday, February 15, 2018 5:45 PM
To: mRemoteNG/mRemoteNG <mRemoteNG@noreply.github.com>
Cc: Jeff Vandervoort <jvandervoort@crescent-systems.com>; Author <author@noreply.github.com>
Subject: Re: [mRemoteNG/mRemoteNG] NLA error 2825 (#875)
The only AxMstsc property we set based on the Use CredSsp value is _rdpClient.AdvancedSettings7.EnableCredSspSupport (RdpProtocol.cs:151). Related documentation page here: https://msdn.microsoft.com/en-us/library/gg130858(v=vs.85).aspx
The only somewhat related value seems to be _rdpClient.AdvancedSettings5.AuthenticationLevel (RdpProtocol.cs:143) which we currently hardcode to 0. Related documentation here: https://msdn.microsoft.com/en-us/library/aa380846(v=vs.85).aspx. Though this seems to be more about authenticating that the server is valid via certs than requesting creds from a client.
I cant find any property that specifically references NLA.
It may be that the AxMstsc library lacks the distinction between CredSSP and NLA.
—
You are receiving this because you authored the thread.
Reply to this email directly, view it on GitHub<#875 (comment)>, or mute the thread<https://github.com/notifications/unsubscribe-auth/AiVu_OecDuThCrP-yIA52edRm_hPime_ks5tVKaXgaJpZM4R0VgX>.
Np @JRVcr, there may be work-arounds for it or something I’m still missing, so I’ll keep this open for a bit. I am doing a bit of work on our RDP components next release so I may take a look at this again
Cool, thanks, David.
I need to also mention that I’m really glad I found mRemoteNG. It provides the functionality of the commercial RD manager I used years ago, can’t recall the name of it any more. Especially the External Tools feature I use almost as much as RDS. But mRemoteNG is available at my favorite price!
I love that it scales the Remote Desktop for my Surface Pro hi-res display automatically. That’s what initially drew me to it. When I got my Surface Pro, I couldn’t see the servers I was working on any more with MSTSC without manually scaling, or RDCMAN which has no scaling at all.
Speaking of scaling…any thought of creating a RemoteApp client instead of using MSTSC.EXE? RemoteApps on hi-res displays have no scaling provisions at all, even manually, and are pretty much unusable. At least against WS2012 RDSH’s. I think I read MS has done better with scaling on WS2016 but don’t have experience with it. (That would also put the CredSSP feature to good use!<g>)
…
—
Jeff Vandervoort
Crescent IT Systems
From: David Sparer [mailto:notifications@github.com]
Sent: Friday, February 16, 2018 11:30 AM
To: mRemoteNG/mRemoteNG <mRemoteNG@noreply.github.com>
Cc: Jeff Vandervoort <jvandervoort@crescent-systems.com>; Mention <mention@noreply.github.com>
Subject: Re: [mRemoteNG/mRemoteNG] NLA error 2825 (#875)
Np @JRVcr<https://github.com/jrvcr>, there may be work-arounds for it or something I’m still missing, so I’ll keep this open for a bit. I am doing a bit of work on our RDP components next release so I may take a look at this again
—
You are receiving this because you were mentioned.
Reply to this email directly, view it on GitHub<#875 (comment)>, or mute the thread<https://github.com/notifications/unsubscribe-auth/AiVu_Ntb8H4aHuT8No7eJI_BLvRYwDqXks5tVbsCgaJpZM4R0VgX>.
@sparerd The afore mentioned Authentication Level property https://msdn.microsoft.com/en-us/library/aa380846(v=vs.85).aspx should in fact be the reference to NLA you are looking for. The equivalent is «authentication level:i:n» for .RDP files (as referenced to here), where «n» can be any of the levels described in https://msdn.microsoft.com/en-us/library/aa380846(v=vs.85).aspx
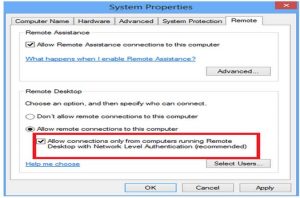
If you’re hard-coding the value to 0, end-users will not be able to connect to systems set with the «Allow connections only from computers running Remote Desktop with Network Level Authentication» option enabled on the remote system. Unless something changed though, requiring NLA should be off by default in Windows (so it’s not a common need), but it can be enabled locally and/or via GPO.
Thus, _rdpClient.AdvancedSettings5.AuthenticationLevel should be made into a configurable flag with a default of 0 to keep current functionality while allowing end-users to alter the setting when needed.
Thanks for clarifying @guidez. We can get this added as a configurable option with a default of ‘0’ as you’ve suggested. I’ll tentatively add this to the v1.77 release. That release is getting a bit full, but this change is fairly straight forward.
sparerd
changed the title
NLA error 2825
Allow setting RDP AuthenticationLevel to prevent NLA error 2825
Jun 13, 2018
NLA is on by default in WS2012 and later. It is, in fact, a near-universal need for system administrators in my experience.
The MSTSC client GUI doesn’t offer a setting for NLA. It used it if the server requests it and falls back to the servers GINA if it does not. That is how mRemoteNG should work, in my opinion.
Having a flag for this could be a moderately useful diagnostic tool, but something that most users will not want to have to fuss with, any more than they do with MSTSC.
…
@JRVcr Wouldn’t go so far as to say it’s a «near-universal need»: Search for «windows 2012 nla«, and you’ll find most of the links are for requests to turn NLA off on remote end-points.
You are correct though, MSTSC does not provide an option to alter the AuthenticationLevel setting from the GUI itself, but it is a simple tweak in a saved RDP file to alter the setting.
Having a flag for this could be a moderately useful diagnostic tool, but something that most users will not want to have to fuss with, any more than they do with MSTSC.
The point of the flag is to just move away from the currently hardcoded variant and give end-users the option to alter it when needed. If we’re just talking about truly imitating native MSTSC/.RDP file functionality, I’d concur that the default value for _rdpClient.AdvancedSettings5.AuthenticationLevel should be 2, but perhaps on a later release?
The hardcoded variant has been 0 for who knows how long, and introducing it as both a configurable option and altering the current hardcoded/default value in one go might make some heads spin.
edit
To clarify, changing the value from 0 to 2 will potentially cause an additional prompt on the end-users side of things, so while it’s the «native» MSTSC experience, it’s not native to the mRemoteNG experience.
0: No authentication of the server.
2: Attempt authentication of the server. If authentication fails, the user will be prompted with the option to cancel the connection or to proceed without server authentication.
Really Microsoft should have added a fourth option… «3»: Attempt auth, if auth fails, continue automatically. But Microsoft did… well it did what Microsoft does.
@guidez You make a good point about the default value. Retaining the ‘0’ default value provides an easy transition for users who are not affected by this issue. We don’t want to ‘break’ existing functionality unless we have a good reason.
For users who will always want NLA, they can set the default connection info property to ‘2’. Newly created connections will have NLA turned on.
The largest issue will come for users who need NLA turned on for many connections. Because we do not yet support mass editing of connections, users will have to do a find & replace of the XML file or edit each individual connection in the app. Though this would be an issue with whichever default value we chose.
Another downside is that users who do still need NLA will receive that somewhat unhelpful error message. We can mitigate this drawback by improving the error message. Best practice is to (1) inform the user what went wrong and (2) include several suggestions for how to fix it or how to troubleshoot further. Currently this error message (and most of our error messages actually..) lacks that 2nd part.
Hi,
Thanks for posting here.
Could you try connecting to any other client machine that listed in «Connect to a Computer» and see if it will working properly.
Meanwhile, could you verify that if any Event ID 303 entry had been recorded on SBS 2008 host ?
Path:
Application and Services Logs | MicrosoftWindows | TerminalServices-GatewayOperational
Here is the workaround for solving this issue ,please try and post back the result :
These steps need to be applied on the SBS 2008 as well as any potential Terminal Server in the domain
Open Terminal serveries configuration console: Administrative Tools | Terminal Services | Terminal Services Configuration
1) in Terminal Services Configuration: ServerName, open Properties of RDP-Tcp
2) Select General tab
3) Make sure the check box is not checked:
» Allow connections only from computers running Remote Desktop with Network Level Authentication»
4) click OK on the following windows pop-up
—————————
Terminal Services Configuration
—————————
Configuration changes have been made to the system registry; however, the user
session now active on the RDP-Tcp connection will not be changed.
—————————
OK
—————————
Thanks.
Tiger Li
TechNet Subscriber Support in forum
If you have any feedback on our support, please contact
tngfb@microsoft.com
Please remember to click “Mark as Answer” on the post that helps you, and to click “Unmark as Answer” if a marked post does not actually answer your question. This can be beneficial to other community members reading the thread.
-
Marked as answer by
Thursday, February 10, 2011 9:18 AM
Category:
Windows 7
— SkyHi @ Sunday, May 23, 2010
Recently while trying to connect to a remote PC using the Remote Desktop manager called “mRemote”, I received a rather unhelpful error message:
RDP Disconnected! Error Code: 2825 Error Description:
However, if using Windows built in Remote Desktop Connection software (mstsc.exe) I was able to connect.
The answer was so simple, I almost did a facepalm. The remote machine had remote desktop enabled, but required Network Level Authentication (NLA). As soon as I enabled the option “Allow connections from computers running any version of Remote Desktop (less secure)” I was able to connect via mRemote.
My only guess as to why mRemote couldn’t connect is that I’m using the portable version of mRemote which requires you to manually register the various components used to connect to remote clients. The version of “AxInterop.MSTSCLib.dll” that came with mRemote and is registered for remote desktop usage must not support NLA. I couldn’t find an updated version of that file.
Maybe someday I’ll spring for VisionApp Remote Desktop, which is the product that the mRemote creator merged all further updates of mRemote into. You can also read my review of mRemote over here.
REFERENCES
http://www.thenubbyadmin.com/2010/05/21/solved-rdp-disconnected-error-code-2825/
I have the same NLA Error 2825.
It’s a clean install so don’t know if this scenario worked previous to the update.
mRemoteNG v1.75.7012.16814
Windows 10 1709 OS Build 16299.248
Happy to test an update/fix.
Thanks.
Do you have Use CredSSP enabled for that connection (Protocol section in the config window)?
Hi David
No, CredSSP is off.
CredSSP is enabled on the computers on the domain of today’s client, and I think on the others I manage. (And has been for a long time, predating this problem.) But it’s not enabled in mRemoteNG.
My computer is not a domain member, so CredSSP won’t work even if enabled…but should not cause a problem. It doesn’t bother MSTSC.
Thanks!
…
—
Jeff Vandervoort
Crescent IT Systems
From: David Sparer [mailto:notifications@github.com]
Sent: Wednesday, February 14, 2018 2:53 PM
To: mRemoteNG/mRemoteNG <mRemoteNG@noreply.github.com>
Cc: Jeff Vandervoort <jvandervoort@crescent-systems.com>; Author <author@noreply.github.com>
Subject: Re: [mRemoteNG/mRemoteNG] NLA error 2825 (#875)
Do you have Use CredSSP enabled for that connection (Protocol section in the config window)?
—
You are receiving this because you authored the thread.
Reply to this email directly, view it on GitHub<#875 (comment)>, or mute the thread<https://github.com/notifications/unsubscribe-auth/AiVu_Pbrm44HGd0tr82Ax8Y3bfWf9EGBks5tU0eigaJpZM4R0VgX>.
I would recommend attempting a connection from mRemoteNG with CredSSP turned on. According to the CredSSP protocol specification, the client and sever do not need to be on the same domain for the protocol to work. All it does is provide a TLS connection during authentication and help with selecting an authentication protocol that both hosts support.
I admit it seems odd that this issue cropped up after updating mremoteng though.
Wow, David, you’re absolutely right. It worked.
From an admin’s perspective, CredSSP’s purpose in life is Single Sign-On, so the user doesn’t have to log on to the RD session. For that to work, the RDSH and the client have to be members of the same domain, because the client passes the user’s logon credentials to the RDSH, which then has to have its DC authenticate them. So I would not have thought it needed to be turned on.
In fact, by default, CredSSP is DISABLED on RDSH’s. It requires a registry edit or GPO to enable. That makes it even more surprising that this would make any difference. But maybe what’s disabled on the server is the auth piece and not the protocol piece.
So, problem solved, and I learned something.
Maybe I disabled CredSSP at the same time as I did the upgrade. And then when I did the clean install, it was either off by default or I turned it off. Too many weeks have gone by to know, now.
Thanks!
…
—
Jeff Vandervoort
Crescent IT Systems
From: David Sparer [mailto:notifications@github.com]
Sent: Wednesday, February 14, 2018 4:17 PM
To: mRemoteNG/mRemoteNG <mRemoteNG@noreply.github.com>
Cc: Jeff Vandervoort <jvandervoort@crescent-systems.com>; Author <author@noreply.github.com>
Subject: Re: [mRemoteNG/mRemoteNG] NLA error 2825 (#875)
I would recommend attempting a connection from mRemoteNG with CredSSP turned on. According to the CredSSP protocol specification, the client and sever do not need to be on the same domain for the protocol to work. All it does is provide a TLS connection during authentication and help with selecting an authentication protocol that both hosts support.
I admit it seems odd that this issue cropped up after updating mremoteng though.
—
You are receiving this because you authored the thread.
Reply to this email directly, view it on GitHub<#875 (comment)>, or mute the thread<https://github.com/notifications/unsubscribe-auth/AiVu_I1la_cSwq_ALCObcaj5mvLqlRi1ks5tU1tDgaJpZM4R0VgX>.
Hi David, I concur this works. I had tried with CredSSP in both states but this was combined with bad credentials so confused the result.
Thanks for your prompt suggestion.
Simon.
Glad to hear that worked for both of you. I learned something as well — had to do a bit of digging to figure out what credssp was really doing for us.
I’ve created issue #885 to look into improving the error message for rdp error 2825.
David, it’s more than an error message problem. NLA and CredSSP are two different things.
I’m a little rusty now, but RDS was my life a few years ago, and I still support a small RDS infrastructure for one of my clients.
NLA is the feature that prompts for credentials on the client instead of using the GINA on the server. It functions whether you’re passing creds from Windows (CredSSP), using stored creds from mRemoteNG, or typing them. MSTSC requests NLA unless otherwise set in a custom RDP file, and if the RDSH accepts (or requires) NLA, is capable of using it. If the RDSH doesn’t accept NLA, MSTSC falls back to using the RDSH’s GINA for authentication.
CredSSP uses NLA to pass credentials from Windows and won’t function without NLA. CredSSP is disabled by default in MSTSC, and if you want to use it, it must be enabled through a custom RDP file. It’s most often used for RemoteApps in order to provide a UX similar to running a program locally. CredSSP falls back to prompting for credentials if Windows credentials don’t work.
I don’t have visibility into what’s happening under the hood. But empirically, it looks like “Use CredSSP” in mRemoteNG is enabling/disabling client-side NLA AND client-side CredSSP. It should only be enabling/disabling CredSSP. To duplicate functionality of MSTSC v6+, there should NEVER be a time when mRemoteNG, can’t authenticate by NLA if the RDSH supports it, regardless of the “Use CredSSP” setting. With “Use CredSSP” turned on, Windows is ALSO trying to log on with local creds, but that’s harmless. If Windows creds fail, NLA will fall back to mRemoteNG creds, and finally, the credential prompt. We shouldn’t HAVE to enable it to use mRemoteNG, but it won’t hurt anything if we do.
HTH
…
—
Jeff Vandervoort
Crescent IT Systems
From: David Sparer [mailto:notifications@github.com]
Sent: Wednesday, February 14, 2018 5:21 PM
To: mRemoteNG/mRemoteNG <mRemoteNG@noreply.github.com>
Cc: Jeff Vandervoort <jvandervoort@crescent-systems.com>; Author <author@noreply.github.com>
Subject: Re: [mRemoteNG/mRemoteNG] NLA error 2825 (#875)
Glad to hear that worked for both of you. I learned something as well — had to do a bit of digging to figure out what credssp was really doing for us.
I’ve created issue #885<#885> to look into improving the error message for rdp error 2825.
—
You are receiving this because you authored the thread.
Reply to this email directly, view it on GitHub<#875 (comment)>, or mute the thread<https://github.com/notifications/unsubscribe-auth/AiVu_KhtTzNgPCDIeqxNUrZA-kGu2wM7ks5tU2pwgaJpZM4R0VgX>.
The only AxMstsc property we set based on the Use CredSsp value is _rdpClient.AdvancedSettings7.EnableCredSspSupport (RdpProtocol.cs:151). Related documentation page here: https://msdn.microsoft.com/en-us/library/gg130858(v=vs.85).aspx
The only somewhat related value seems to be _rdpClient.AdvancedSettings5.AuthenticationLevel (RdpProtocol.cs:143) which we currently hardcode to 0. Related documentation here: https://msdn.microsoft.com/en-us/library/aa380846(v=vs.85).aspx. Though this seems to be more about authenticating that the server is valid via certs than requesting creds from a client.
I cant find any property that specifically references NLA.
It may be that the AxMstsc library lacks the distinction between CredSSP and NLA.
OK, thanks for the followup, David. That’s interesting. Yes the authentication level does sound like the MSTSC feature where it pops up a security warning if it doesn’t trust the RDSH.
Then, I guess all you can do is change the help text. It does mean that mRemoteNG won’t ever behave like MSTSC does, but that’s on MS.
Thanks!
…
—
Jeff Vandervoort
Crescent IT Systems
From: David Sparer [mailto:notifications@github.com]
Sent: Thursday, February 15, 2018 5:45 PM
To: mRemoteNG/mRemoteNG <mRemoteNG@noreply.github.com>
Cc: Jeff Vandervoort <jvandervoort@crescent-systems.com>; Author <author@noreply.github.com>
Subject: Re: [mRemoteNG/mRemoteNG] NLA error 2825 (#875)
The only AxMstsc property we set based on the Use CredSsp value is _rdpClient.AdvancedSettings7.EnableCredSspSupport (RdpProtocol.cs:151). Related documentation page here: https://msdn.microsoft.com/en-us/library/gg130858(v=vs.85).aspx
The only somewhat related value seems to be _rdpClient.AdvancedSettings5.AuthenticationLevel (RdpProtocol.cs:143) which we currently hardcode to 0. Related documentation here: https://msdn.microsoft.com/en-us/library/aa380846(v=vs.85).aspx. Though this seems to be more about authenticating that the server is valid via certs than requesting creds from a client.
I cant find any property that specifically references NLA.
It may be that the AxMstsc library lacks the distinction between CredSSP and NLA.
—
You are receiving this because you authored the thread.
Reply to this email directly, view it on GitHub<#875 (comment)>, or mute the thread<https://github.com/notifications/unsubscribe-auth/AiVu_OecDuThCrP-yIA52edRm_hPime_ks5tVKaXgaJpZM4R0VgX>.
Np @JRVcr, there may be work-arounds for it or something I’m still missing, so I’ll keep this open for a bit. I am doing a bit of work on our RDP components next release so I may take a look at this again
Cool, thanks, David.
I need to also mention that I’m really glad I found mRemoteNG. It provides the functionality of the commercial RD manager I used years ago, can’t recall the name of it any more. Especially the External Tools feature I use almost as much as RDS. But mRemoteNG is available at my favorite price!
I love that it scales the Remote Desktop for my Surface Pro hi-res display automatically. That’s what initially drew me to it. When I got my Surface Pro, I couldn’t see the servers I was working on any more with MSTSC without manually scaling, or RDCMAN which has no scaling at all.
Speaking of scaling…any thought of creating a RemoteApp client instead of using MSTSC.EXE? RemoteApps on hi-res displays have no scaling provisions at all, even manually, and are pretty much unusable. At least against WS2012 RDSH’s. I think I read MS has done better with scaling on WS2016 but don’t have experience with it. (That would also put the CredSSP feature to good use!<g>)
…
—
Jeff Vandervoort
Crescent IT Systems
From: David Sparer [mailto:notifications@github.com]
Sent: Friday, February 16, 2018 11:30 AM
To: mRemoteNG/mRemoteNG <mRemoteNG@noreply.github.com>
Cc: Jeff Vandervoort <jvandervoort@crescent-systems.com>; Mention <mention@noreply.github.com>
Subject: Re: [mRemoteNG/mRemoteNG] NLA error 2825 (#875)
Np @JRVcr<https://github.com/jrvcr>, there may be work-arounds for it or something I’m still missing, so I’ll keep this open for a bit. I am doing a bit of work on our RDP components next release so I may take a look at this again
—
You are receiving this because you were mentioned.
Reply to this email directly, view it on GitHub<#875 (comment)>, or mute the thread<https://github.com/notifications/unsubscribe-auth/AiVu_Ntb8H4aHuT8No7eJI_BLvRYwDqXks5tVbsCgaJpZM4R0VgX>.
@sparerd The afore mentioned Authentication Level property https://msdn.microsoft.com/en-us/library/aa380846(v=vs.85).aspx should in fact be the reference to NLA you are looking for. The equivalent is «authentication level:i:n» for .RDP files (as referenced to here), where «n» can be any of the levels described in https://msdn.microsoft.com/en-us/library/aa380846(v=vs.85).aspx
If you’re hard-coding the value to 0, end-users will not be able to connect to systems set with the «Allow connections only from computers running Remote Desktop with Network Level Authentication» option enabled on the remote system. Unless something changed though, requiring NLA should be off by default in Windows (so it’s not a common need), but it can be enabled locally and/or via GPO.
Thus, _rdpClient.AdvancedSettings5.AuthenticationLevel should be made into a configurable flag with a default of 0 to keep current functionality while allowing end-users to alter the setting when needed.
Thanks for clarifying @guidez. We can get this added as a configurable option with a default of ‘0’ as you’ve suggested. I’ll tentatively add this to the v1.77 release. That release is getting a bit full, but this change is fairly straight forward.
sparerd
changed the title
NLA error 2825
Allow setting RDP AuthenticationLevel to prevent NLA error 2825
Jun 13, 2018
NLA is on by default in WS2012 and later. It is, in fact, a near-universal need for system administrators in my experience.
The MSTSC client GUI doesn’t offer a setting for NLA. It used it if the server requests it and falls back to the servers GINA if it does not. That is how mRemoteNG should work, in my opinion.
Having a flag for this could be a moderately useful diagnostic tool, but something that most users will not want to have to fuss with, any more than they do with MSTSC.
…
@JRVcr Wouldn’t go so far as to say it’s a «near-universal need»: Search for «windows 2012 nla«, and you’ll find most of the links are for requests to turn NLA off on remote end-points.
You are correct though, MSTSC does not provide an option to alter the AuthenticationLevel setting from the GUI itself, but it is a simple tweak in a saved RDP file to alter the setting.
Having a flag for this could be a moderately useful diagnostic tool, but something that most users will not want to have to fuss with, any more than they do with MSTSC.
The point of the flag is to just move away from the currently hardcoded variant and give end-users the option to alter it when needed. If we’re just talking about truly imitating native MSTSC/.RDP file functionality, I’d concur that the default value for _rdpClient.AdvancedSettings5.AuthenticationLevel should be 2, but perhaps on a later release?
The hardcoded variant has been 0 for who knows how long, and introducing it as both a configurable option and altering the current hardcoded/default value in one go might make some heads spin.
edit
To clarify, changing the value from 0 to 2 will potentially cause an additional prompt on the end-users side of things, so while it’s the «native» MSTSC experience, it’s not native to the mRemoteNG experience.
0: No authentication of the server.
2: Attempt authentication of the server. If authentication fails, the user will be prompted with the option to cancel the connection or to proceed without server authentication.
Really Microsoft should have added a fourth option… «3»: Attempt auth, if auth fails, continue automatically. But Microsoft did… well it did what Microsoft does.
@guidez You make a good point about the default value. Retaining the ‘0’ default value provides an easy transition for users who are not affected by this issue. We don’t want to ‘break’ existing functionality unless we have a good reason.
For users who will always want NLA, they can set the default connection info property to ‘2’. Newly created connections will have NLA turned on.
The largest issue will come for users who need NLA turned on for many connections. Because we do not yet support mass editing of connections, users will have to do a find & replace of the XML file or edit each individual connection in the app. Though this would be an issue with whichever default value we chose.
Another downside is that users who do still need NLA will receive that somewhat unhelpful error message. We can mitigate this drawback by improving the error message. Best practice is to (1) inform the user what went wrong and (2) include several suggestions for how to fix it or how to troubleshoot further. Currently this error message (and most of our error messages actually..) lacks that 2nd part.
I am running an SBS 2008 Premium server network and just installed a second web IIS server with SQL 2008 installed.
In the past I was able to use RWW to RDP to any servers or computers in the network.
I now get a RDP error within the RWW login when I try to connect from any computer in the network. The error is «VBScript: Remote Desktop Disconnected» error box «An internal error has occurred (error 2825)»
I tried this from my Win7Pro64bit machine. I noted the Remote Desktop settings are greyed out and stuck on «Allow any version of RDP ..option 2».
How do i enable this greyed out area for the desktop?..I want to change to 3rd option (NLA) for this desktop.
Is there a group policy controlling this option to force it to be greyed out?
I have tried to login as local and network admin user to this machine and another however these options are still greyed out no matter what the user is?
I noted if i change the Remote Desktop settings for both servers to «ALLOW ANY version (option2) of RDP settings on the local PC, the RWW connection to the servers works fine.
I dont really want to reinstall OS. Please help.!
Asked By
40 points
N/A
Posted on — 04/12/2017
Hi, I am using Windows Remote Desktop Connection to connect to my other desktop. But when I enter my username and password I get this rdp error code 2825(An Internal error has occurred (error 2825)). Please let me know how I can fix this.
Hi, RDP errors on Windows machine usually occur due to registry errors. You need to fix registry. There are various software such as RegCure Pro, Reimage PC repair tool which you can install and repair and fix any registry errors.
After doing this try to connect again. If it is still not working, first check if you can connect to your remote machine through another system. If you are unable to connect, it means that the issue is with the remote machine. To fix the issue on the remote machine: Go to Administrative tools->Click on Remote desktop services and select remote desktop session host configurations. Click on Connections-> properties-> general->Chose “Allow connections from computers running any version of Remote Desktop(less secure)”. Click OK
Hi,
Thanks for posting here.
Could you try connecting to any other client machine that listed in «Connect to a Computer» and see if it will working properly.
Meanwhile, could you verify that if any Event ID 303 entry had been recorded on SBS 2008 host ?
Path:
Application and Services Logs | MicrosoftWindows | TerminalServices-GatewayOperational
Here is the workaround for solving this issue ,please try and post back the result :
These steps need to be applied on the SBS 2008 as well as any potential Terminal Server in the domain
Open Terminal serveries configuration console: Administrative Tools | Terminal Services | Terminal Services Configuration
1) in Terminal Services Configuration: ServerName, open Properties of RDP-Tcp
2) Select General tab
3) Make sure the check box is not checked:
» Allow connections only from computers running Remote Desktop with Network Level Authentication»
4) click OK on the following windows pop-up
—————————
Terminal Services Configuration
—————————
Configuration changes have been made to the system registry; however, the user
session now active on the RDP-Tcp connection will not be changed.
—————————
OK
—————————
Thanks.
Tiger Li
TechNet Subscriber Support in forum
If you have any feedback on our support, please contact
tngfb@microsoft.com
Please remember to click “Mark as Answer” on the post that helps you, and to click “Unmark as Answer” if a marked post does not actually answer your question. This can be beneficial to other community members reading the thread.
-
Marked as answer by
Thursday, February 10, 2011 9:18 AM
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and
privacy statement. We’ll occasionally send you account related emails.
Already on GitHub?
Sign in
to your account
Assignees
Labels
Enhancement
A new feature or improvement to an existing feature.
Help Wanted
We would love to have help on this issue! This may be a good issue for first time contributors.
I have the same NLA Error 2825.
It’s a clean install so don’t know if this scenario worked previous to the update.
mRemoteNG v1.75.7012.16814
Windows 10 1709 OS Build 16299.248
Happy to test an update/fix.
Thanks.
Do you have Use CredSSP enabled for that connection (Protocol section in the config window)?
Hi David
No, CredSSP is off.
CredSSP is enabled on the computers on the domain of today’s client, and I think on the others I manage. (And has been for a long time, predating this problem.) But it’s not enabled in mRemoteNG.
My computer is not a domain member, so CredSSP won’t work even if enabled…but should not cause a problem. It doesn’t bother MSTSC.
Thanks!
…
—
Jeff Vandervoort
Crescent IT Systems
From: David Sparer [mailto:notifications@github.com]
Sent: Wednesday, February 14, 2018 2:53 PM
To: mRemoteNG/mRemoteNG <mRemoteNG@noreply.github.com>
Cc: Jeff Vandervoort <jvandervoort@crescent-systems.com>; Author <author@noreply.github.com>
Subject: Re: [mRemoteNG/mRemoteNG] NLA error 2825 (#875)
Do you have Use CredSSP enabled for that connection (Protocol section in the config window)?
—
You are receiving this because you authored the thread.
Reply to this email directly, view it on GitHub<#875 (comment)>, or mute the thread<https://github.com/notifications/unsubscribe-auth/AiVu_Pbrm44HGd0tr82Ax8Y3bfWf9EGBks5tU0eigaJpZM4R0VgX>.
I would recommend attempting a connection from mRemoteNG with CredSSP turned on. According to the CredSSP protocol specification, the client and sever do not need to be on the same domain for the protocol to work. All it does is provide a TLS connection during authentication and help with selecting an authentication protocol that both hosts support.
I admit it seems odd that this issue cropped up after updating mremoteng though.
Wow, David, you’re absolutely right. It worked.
From an admin’s perspective, CredSSP’s purpose in life is Single Sign-On, so the user doesn’t have to log on to the RD session. For that to work, the RDSH and the client have to be members of the same domain, because the client passes the user’s logon credentials to the RDSH, which then has to have its DC authenticate them. So I would not have thought it needed to be turned on.
In fact, by default, CredSSP is DISABLED on RDSH’s. It requires a registry edit or GPO to enable. That makes it even more surprising that this would make any difference. But maybe what’s disabled on the server is the auth piece and not the protocol piece.
So, problem solved, and I learned something.
Maybe I disabled CredSSP at the same time as I did the upgrade. And then when I did the clean install, it was either off by default or I turned it off. Too many weeks have gone by to know, now.
Thanks!
…
—
Jeff Vandervoort
Crescent IT Systems
From: David Sparer [mailto:notifications@github.com]
Sent: Wednesday, February 14, 2018 4:17 PM
To: mRemoteNG/mRemoteNG <mRemoteNG@noreply.github.com>
Cc: Jeff Vandervoort <jvandervoort@crescent-systems.com>; Author <author@noreply.github.com>
Subject: Re: [mRemoteNG/mRemoteNG] NLA error 2825 (#875)
I would recommend attempting a connection from mRemoteNG with CredSSP turned on. According to the CredSSP protocol specification, the client and sever do not need to be on the same domain for the protocol to work. All it does is provide a TLS connection during authentication and help with selecting an authentication protocol that both hosts support.
I admit it seems odd that this issue cropped up after updating mremoteng though.
—
You are receiving this because you authored the thread.
Reply to this email directly, view it on GitHub<#875 (comment)>, or mute the thread<https://github.com/notifications/unsubscribe-auth/AiVu_I1la_cSwq_ALCObcaj5mvLqlRi1ks5tU1tDgaJpZM4R0VgX>.
Hi David, I concur this works. I had tried with CredSSP in both states but this was combined with bad credentials so confused the result.
Thanks for your prompt suggestion.
Simon.
Glad to hear that worked for both of you. I learned something as well — had to do a bit of digging to figure out what credssp was really doing for us.
I’ve created issue #885 to look into improving the error message for rdp error 2825.
David, it’s more than an error message problem. NLA and CredSSP are two different things.
I’m a little rusty now, but RDS was my life a few years ago, and I still support a small RDS infrastructure for one of my clients.
NLA is the feature that prompts for credentials on the client instead of using the GINA on the server. It functions whether you’re passing creds from Windows (CredSSP), using stored creds from mRemoteNG, or typing them. MSTSC requests NLA unless otherwise set in a custom RDP file, and if the RDSH accepts (or requires) NLA, is capable of using it. If the RDSH doesn’t accept NLA, MSTSC falls back to using the RDSH’s GINA for authentication.
CredSSP uses NLA to pass credentials from Windows and won’t function without NLA. CredSSP is disabled by default in MSTSC, and if you want to use it, it must be enabled through a custom RDP file. It’s most often used for RemoteApps in order to provide a UX similar to running a program locally. CredSSP falls back to prompting for credentials if Windows credentials don’t work.
I don’t have visibility into what’s happening under the hood. But empirically, it looks like “Use CredSSP” in mRemoteNG is enabling/disabling client-side NLA AND client-side CredSSP. It should only be enabling/disabling CredSSP. To duplicate functionality of MSTSC v6+, there should NEVER be a time when mRemoteNG, can’t authenticate by NLA if the RDSH supports it, regardless of the “Use CredSSP” setting. With “Use CredSSP” turned on, Windows is ALSO trying to log on with local creds, but that’s harmless. If Windows creds fail, NLA will fall back to mRemoteNG creds, and finally, the credential prompt. We shouldn’t HAVE to enable it to use mRemoteNG, but it won’t hurt anything if we do.
HTH
…
—
Jeff Vandervoort
Crescent IT Systems
From: David Sparer [mailto:notifications@github.com]
Sent: Wednesday, February 14, 2018 5:21 PM
To: mRemoteNG/mRemoteNG <mRemoteNG@noreply.github.com>
Cc: Jeff Vandervoort <jvandervoort@crescent-systems.com>; Author <author@noreply.github.com>
Subject: Re: [mRemoteNG/mRemoteNG] NLA error 2825 (#875)
Glad to hear that worked for both of you. I learned something as well — had to do a bit of digging to figure out what credssp was really doing for us.
I’ve created issue #885<#885> to look into improving the error message for rdp error 2825.
—
You are receiving this because you authored the thread.
Reply to this email directly, view it on GitHub<#875 (comment)>, or mute the thread<https://github.com/notifications/unsubscribe-auth/AiVu_KhtTzNgPCDIeqxNUrZA-kGu2wM7ks5tU2pwgaJpZM4R0VgX>.
The only AxMstsc property we set based on the Use CredSsp value is _rdpClient.AdvancedSettings7.EnableCredSspSupport (RdpProtocol.cs:151). Related documentation page here: https://msdn.microsoft.com/en-us/library/gg130858(v=vs.85).aspx
The only somewhat related value seems to be _rdpClient.AdvancedSettings5.AuthenticationLevel (RdpProtocol.cs:143) which we currently hardcode to 0. Related documentation here: https://msdn.microsoft.com/en-us/library/aa380846(v=vs.85).aspx. Though this seems to be more about authenticating that the server is valid via certs than requesting creds from a client.
I cant find any property that specifically references NLA.
It may be that the AxMstsc library lacks the distinction between CredSSP and NLA.
OK, thanks for the followup, David. That’s interesting. Yes the authentication level does sound like the MSTSC feature where it pops up a security warning if it doesn’t trust the RDSH.
Then, I guess all you can do is change the help text. It does mean that mRemoteNG won’t ever behave like MSTSC does, but that’s on MS.
Thanks!
…
—
Jeff Vandervoort
Crescent IT Systems
From: David Sparer [mailto:notifications@github.com]
Sent: Thursday, February 15, 2018 5:45 PM
To: mRemoteNG/mRemoteNG <mRemoteNG@noreply.github.com>
Cc: Jeff Vandervoort <jvandervoort@crescent-systems.com>; Author <author@noreply.github.com>
Subject: Re: [mRemoteNG/mRemoteNG] NLA error 2825 (#875)
The only AxMstsc property we set based on the Use CredSsp value is _rdpClient.AdvancedSettings7.EnableCredSspSupport (RdpProtocol.cs:151). Related documentation page here: https://msdn.microsoft.com/en-us/library/gg130858(v=vs.85).aspx
The only somewhat related value seems to be _rdpClient.AdvancedSettings5.AuthenticationLevel (RdpProtocol.cs:143) which we currently hardcode to 0. Related documentation here: https://msdn.microsoft.com/en-us/library/aa380846(v=vs.85).aspx. Though this seems to be more about authenticating that the server is valid via certs than requesting creds from a client.
I cant find any property that specifically references NLA.
It may be that the AxMstsc library lacks the distinction between CredSSP and NLA.
—
You are receiving this because you authored the thread.
Reply to this email directly, view it on GitHub<#875 (comment)>, or mute the thread<https://github.com/notifications/unsubscribe-auth/AiVu_OecDuThCrP-yIA52edRm_hPime_ks5tVKaXgaJpZM4R0VgX>.
Np @JRVcr, there may be work-arounds for it or something I’m still missing, so I’ll keep this open for a bit. I am doing a bit of work on our RDP components next release so I may take a look at this again
Cool, thanks, David.
I need to also mention that I’m really glad I found mRemoteNG. It provides the functionality of the commercial RD manager I used years ago, can’t recall the name of it any more. Especially the External Tools feature I use almost as much as RDS. But mRemoteNG is available at my favorite price!
I love that it scales the Remote Desktop for my Surface Pro hi-res display automatically. That’s what initially drew me to it. When I got my Surface Pro, I couldn’t see the servers I was working on any more with MSTSC without manually scaling, or RDCMAN which has no scaling at all.
Speaking of scaling…any thought of creating a RemoteApp client instead of using MSTSC.EXE? RemoteApps on hi-res displays have no scaling provisions at all, even manually, and are pretty much unusable. At least against WS2012 RDSH’s. I think I read MS has done better with scaling on WS2016 but don’t have experience with it. (That would also put the CredSSP feature to good use!<g>)
…
—
Jeff Vandervoort
Crescent IT Systems
From: David Sparer [mailto:notifications@github.com]
Sent: Friday, February 16, 2018 11:30 AM
To: mRemoteNG/mRemoteNG <mRemoteNG@noreply.github.com>
Cc: Jeff Vandervoort <jvandervoort@crescent-systems.com>; Mention <mention@noreply.github.com>
Subject: Re: [mRemoteNG/mRemoteNG] NLA error 2825 (#875)
Np @JRVcr<https://github.com/jrvcr>, there may be work-arounds for it or something I’m still missing, so I’ll keep this open for a bit. I am doing a bit of work on our RDP components next release so I may take a look at this again
—
You are receiving this because you were mentioned.
Reply to this email directly, view it on GitHub<#875 (comment)>, or mute the thread<https://github.com/notifications/unsubscribe-auth/AiVu_Ntb8H4aHuT8No7eJI_BLvRYwDqXks5tVbsCgaJpZM4R0VgX>.
@sparerd The afore mentioned Authentication Level property https://msdn.microsoft.com/en-us/library/aa380846(v=vs.85).aspx should in fact be the reference to NLA you are looking for. The equivalent is «authentication level:i:n» for .RDP files (as referenced to here), where «n» can be any of the levels described in https://msdn.microsoft.com/en-us/library/aa380846(v=vs.85).aspx
If you’re hard-coding the value to 0, end-users will not be able to connect to systems set with the «Allow connections only from computers running Remote Desktop with Network Level Authentication» option enabled on the remote system. Unless something changed though, requiring NLA should be off by default in Windows (so it’s not a common need), but it can be enabled locally and/or via GPO.
Thus, _rdpClient.AdvancedSettings5.AuthenticationLevel should be made into a configurable flag with a default of 0 to keep current functionality while allowing end-users to alter the setting when needed.
Thanks for clarifying @guidez. We can get this added as a configurable option with a default of ‘0’ as you’ve suggested. I’ll tentatively add this to the v1.77 release. That release is getting a bit full, but this change is fairly straight forward.
sparerd
changed the title
NLA error 2825
Allow setting RDP AuthenticationLevel to prevent NLA error 2825
Jun 13, 2018
NLA is on by default in WS2012 and later. It is, in fact, a near-universal need for system administrators in my experience.
The MSTSC client GUI doesn’t offer a setting for NLA. It used it if the server requests it and falls back to the servers GINA if it does not. That is how mRemoteNG should work, in my opinion.
Having a flag for this could be a moderately useful diagnostic tool, but something that most users will not want to have to fuss with, any more than they do with MSTSC.
…
@JRVcr Wouldn’t go so far as to say it’s a «near-universal need»: Search for «windows 2012 nla«, and you’ll find most of the links are for requests to turn NLA off on remote end-points.
You are correct though, MSTSC does not provide an option to alter the AuthenticationLevel setting from the GUI itself, but it is a simple tweak in a saved RDP file to alter the setting.
Having a flag for this could be a moderately useful diagnostic tool, but something that most users will not want to have to fuss with, any more than they do with MSTSC.
The point of the flag is to just move away from the currently hardcoded variant and give end-users the option to alter it when needed. If we’re just talking about truly imitating native MSTSC/.RDP file functionality, I’d concur that the default value for _rdpClient.AdvancedSettings5.AuthenticationLevel should be 2, but perhaps on a later release?
The hardcoded variant has been 0 for who knows how long, and introducing it as both a configurable option and altering the current hardcoded/default value in one go might make some heads spin.
edit
To clarify, changing the value from 0 to 2 will potentially cause an additional prompt on the end-users side of things, so while it’s the «native» MSTSC experience, it’s not native to the mRemoteNG experience.
0: No authentication of the server.
2: Attempt authentication of the server. If authentication fails, the user will be prompted with the option to cancel the connection or to proceed without server authentication.
Really Microsoft should have added a fourth option… «3»: Attempt auth, if auth fails, continue automatically. But Microsoft did… well it did what Microsoft does.
@guidez You make a good point about the default value. Retaining the ‘0’ default value provides an easy transition for users who are not affected by this issue. We don’t want to ‘break’ existing functionality unless we have a good reason.
For users who will always want NLA, they can set the default connection info property to ‘2’. Newly created connections will have NLA turned on.
The largest issue will come for users who need NLA turned on for many connections. Because we do not yet support mass editing of connections, users will have to do a find & replace of the XML file or edit each individual connection in the app. Though this would be an issue with whichever default value we chose.
Another downside is that users who do still need NLA will receive that somewhat unhelpful error message. We can mitigate this drawback by improving the error message. Best practice is to (1) inform the user what went wrong and (2) include several suggestions for how to fix it or how to troubleshoot further. Currently this error message (and most of our error messages actually..) lacks that 2nd part.
Category:
Windows 7
— SkyHi @ Sunday, May 23, 2010
Recently while trying to connect to a remote PC using the Remote Desktop manager called “mRemote”, I received a rather unhelpful error message:
RDP Disconnected! Error Code: 2825 Error Description:
However, if using Windows built in Remote Desktop Connection software (mstsc.exe) I was able to connect.
The answer was so simple, I almost did a facepalm. The remote machine had remote desktop enabled, but required Network Level Authentication (NLA). As soon as I enabled the option “Allow connections from computers running any version of Remote Desktop (less secure)” I was able to connect via mRemote.
My only guess as to why mRemote couldn’t connect is that I’m using the portable version of mRemote which requires you to manually register the various components used to connect to remote clients. The version of “AxInterop.MSTSCLib.dll” that came with mRemote and is registered for remote desktop usage must not support NLA. I couldn’t find an updated version of that file.
Maybe someday I’ll spring for VisionApp Remote Desktop, which is the product that the mRemote creator merged all further updates of mRemote into. You can also read my review of mRemote over here.
REFERENCES
http://www.thenubbyadmin.com/2010/05/21/solved-rdp-disconnected-error-code-2825/
Sidebar
Recently Changed Pages:
View All Pages
View All Tags
WIKI Disclaimer:
As with most other things on the Internet, the content on this wiki is not supported. It was contributed by me and is published “as is”. It has worked for me, and might work for you.
Also note that any view or statement expressed anywhere on this site are strictly mine and not the opinions or views of my employer.
Pages with comments
View All Comments
fixmremote2825
Fix: Error 2825 when using mRemote RDP sessions
This happens when RDP sessions from older RDP clients are not allowed. On the server you want to connect do the following:
-
Start Server Manager
-
Click on Configure Remote Desktop
-
Set the Remote Desktop option to :Allow connections from computers running any version of Remote Desktop (less secure)
-
Click OK
Retry the RDP session and you’ll see it works.
You could leave a comment if you were logged in.
fixmremote2825.txt
· Last modified: 2021/09/24 00:24 (external edit)
Category:
Windows 7
— SkyHi @ Sunday, May 23, 2010
Recently while trying to connect to a remote PC using the Remote Desktop manager called “mRemote”, I received a rather unhelpful error message:
RDP Disconnected! Error Code: 2825 Error Description:
However, if using Windows built in Remote Desktop Connection software (mstsc.exe) I was able to connect.
The answer was so simple, I almost did a facepalm. The remote machine had remote desktop enabled, but required Network Level Authentication (NLA). As soon as I enabled the option “Allow connections from computers running any version of Remote Desktop (less secure)” I was able to connect via mRemote.
My only guess as to why mRemote couldn’t connect is that I’m using the portable version of mRemote which requires you to manually register the various components used to connect to remote clients. The version of “AxInterop.MSTSCLib.dll” that came with mRemote and is registered for remote desktop usage must not support NLA. I couldn’t find an updated version of that file.
Maybe someday I’ll spring for VisionApp Remote Desktop, which is the product that the mRemote creator merged all further updates of mRemote into. You can also read my review of mRemote over here.
REFERENCES
http://www.thenubbyadmin.com/2010/05/21/solved-rdp-disconnected-error-code-2825/