| title | description | ms.date | author | ms.author | ms.editor | ms.reviewer | ms.service | ms.subservice | keywords |
|---|---|---|---|---|---|---|---|---|---|
|
Error AADSTS50020 — User account from identity provider does not exist in tenant |
Troubleshoot scenarios in which a guest user unsuccessfully tries to sign in to the resource tenant and error code AADSTS50020 is returned. |
03/28/2023 |
DennisLee-DennisLee |
v-dele |
v-jsitser |
rrajan,haelshab,sungow |
active-directory |
app-mgmt |
Error AADSTS50020 — User account from identity provider does not exist in tenant
This article helps you troubleshoot error code AADSTS50020 that’s returned if a guest user from an identity provider (IdP) can’t sign in to a resource tenant in Azure Active Directory (Azure AD).
Symptoms
When a guest user tries to access an application or resource in the resource tenant, the sign-in fails, and the following error message is displayed:
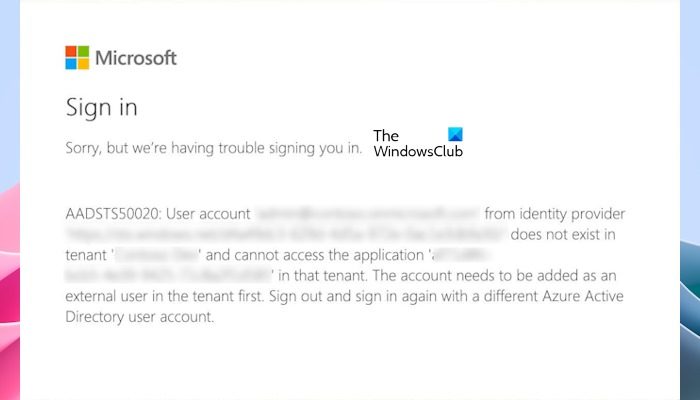
AADSTS50020: User account ‘user@domain.com’ from identity provider {IdentityProviderURL} does not exist in tenant {ResourceTenantName}.
When an administrator reviews the sign-in logs on the home tenant, a «90072» error code entry indicates a sign-in failure. The error message states:
User account {email} from identity provider {idp} does not exist in tenant {tenant} and cannot access the application {appId}({appName}) in that tenant. The account needs to be added as an external user in the tenant first. Sign out and sign in again with a different Azure Active Directory user account.
Cause 1: Used unsupported account type (multitenant and personal accounts)
If your app registration is set to a single-tenant account type, users from other directories or identity providers can’t sign in to that application.
Solution: Change the sign-in audience setting in the app registration manifest
To make sure that your app registration isn’t a single-tenant account type, perform the following steps:
-
In the Azure portal, search for and select App registrations.
-
Select the name of your app registration.
-
In the sidebar, select Manifest.
-
In the JSON code, find the signInAudience setting.
-
Check whether the setting contains one of the following values:
- AzureADandPersonalMicrosoftAccount
- AzureADMultipleOrgs
- PersonalMicrosoftAccount
If the signInAudience setting doesn’t contain one of these values, re-create the app registration by having the correct account type selected. You currently can’t change signInAudience in the manifest.
For more information about how to register applications, see Quickstart: Register an application with the Microsoft identity platform.
Cause 2: Used the wrong endpoint (personal and organization accounts)
Your authentication call must target a URL that matches your selection if your app registration’s supported account type was set to one of the following values:
-
Accounts in any organizational directory (Any Azure AD directory — Multitenant)
-
Accounts in any organizational directory (Any Azure AD directory — Multitenant) and personal Microsoft accounts (e.g. Skype, Xbox)
-
Personal Microsoft accounts only
If you use https://login.microsoftonline.com/<YourTenantNameOrID>, users from other organizations can’t access the application. You have to add these users as guests in the tenant that’s specified in the request. In that case, the authentication is expected to be run on your tenant only. This scenario causes the sign-in error if you expect users to sign in by using federation with another tenant or identity provider.
Solution: Use the correct sign-in URL
Use the corresponding sign-in URL for the specific application type, as listed in the following table:
| Application type | Sign-in URL |
|---|---|
| Multitenant applications | https://login.microsoftonline.com/organizations |
| Multitenant and personal accounts | https://login.microsoftonline.com/common |
| Personal accounts only | https://login.microsoftonline.com/consumers |
In your application code, apply this URL value in the Authority setting. For more information about Authority, see Microsoft identity platform application configuration options.
Cause 3: Signed in to the wrong tenant
When users try to access your application, either they’re sent a direct link to the application, or they try to gain access through https://myapps.microsoft.com. In either situation, users are redirected to sign in to the application. In some cases, the user might already have an active session that uses a different personal account than the one that’s intended to be used. Or they have a session that uses their organization account although they intended to use a personal guest account (or vice versa).
To make sure that this scenario is the issue, look for the User account and Identity provider values in the error message. Do those values match the expected combination or not? For example, did a user sign in by using their organization account to your tenant instead of their home tenant? Or did a user sign in to the live.com identity provider by using a different personal account than the one that was already invited?
Solution: Sign out, then sign in again from a different browser or a private browser session
Instruct the user to open a new in-private browser session or have the user try to access from a different browser. In this case, users must sign out from their active session, and then try to sign in again.
Cause 4: Guest user wasn’t invited
The guest user who tried to sign in was not invited to the tenant.
Solution: Invite the guest user
Make sure that you follow the steps in Quickstart: Add guest users to your directory in the Azure portal to invite the guest user.
Cause 5: App requires user assignment
If your application is an enterprise application that requires user assignment, error AADSTS50020 occurs if the user isn’t on the list of allowed users who are assigned access to the application. To check whether your enterprise application requires user assignment:
-
In the Azure portal, search for and select Enterprise applications.
-
Select your enterprise application.
-
In the sidebar, select Properties.
-
Check whether the Assignment required option is set to Yes.
Solution: Assign access to users individually or as part of a group
Use one of the following options to assign access to users:
-
To individually assign the user access to the application, see Assign a user account to an enterprise application.
-
To assign users if they’re a member of an assigned group or a dynamic group, see Manage access to an application.
Cause 6: Tried to use a resource owner password credentials flow for personal accounts
If a user tries to use the resource owner password credentials (ROPC) flow for personal accounts, error AADSTS50020 occurs. The Microsoft identity platform supports ROPC only within Azure AD tenants, not personal accounts.
Solution: Use an endpoint that’s specific to the tenant or organization
Use a tenant-specific endpoint (https://login.microsoftonline.com/<TenantIDOrName>) or the organization’s endpoint. Personal accounts that are invited to an Azure AD tenant can’t use ROPC. For more information, see Microsoft identity platform and OAuth 2.0 Resource Owner Password Credentials.
Cause 7: A previously deleted user name was re-created by the home tenant administrator
Error AADSTS50020 might occur if the name of a guest user who was deleted in a resource tenant is re-created by the administrator of the home tenant. To verify that the guest user account in the resource tenant isn’t associated with a user account in the home tenant, use one of the following options:
Verification option 1: Check whether the resource tenant’s guest user is older than the home tenant’s user account
The first verification option involves comparing the age of the resource tenant’s guest user against the home tenant’s user account. You can make this verification by using Microsoft Graph or MSOnline PowerShell.
Microsoft Graph
Issue a request to the MS Graph API to review the user creation date, as follows:
GET https://graph.microsoft.com/v1.0/users/{id | userPrincipalName}/createdDateTime
Then, check the creation date of the guest user in the resource tenant against the creation date of the user account in the home tenant. The scenario is confirmed if the guest user was created before the home tenant’s user account was created.
MSOnline PowerShell
[!NOTE]
The MSOnline PowerShell module is set to be deprecated.
Because it’s also incompatible with PowerShell Core, make sure that you’re using a compatible PowerShell version so that you can run the following commands.
Run the Get-MsolUser PowerShell cmdlet to review the user creation date, as follows:
Get-MsolUser -SearchString user@contoso.com | Format-List whenCreated
Then, check the creation date of the guest user in the resource tenant against the creation date of the user account in the home tenant. The scenario is confirmed if the guest user was created before the home tenant’s user account was created.
Verification option 2: Check whether the resource tenant’s guest alternative security ID differs from the home tenant’s user net ID
[!NOTE]
The MSOnline PowerShell module is set to be deprecated.
Because it’s also incompatible with PowerShell Core, make sure that you’re using a compatible PowerShell version so that you can run the following commands.
When a guest user accepts an invitation, the user’s LiveID attribute (the unique sign-in ID of the user) is stored within AlternativeSecurityIds in the key attribute. Because the user account was deleted and created in the home tenant, the NetID value for the account will have changed for the user in the home tenant. Compare the NetID value of the user account in the home tenant against the key value that’s stored within AlternativeSecurityIds of the guest account in the resource tenant, as follows:
-
In the home tenant, retrieve the value of the
LiveIDattribute using theGet-MsolUserPowerShell cmdlet:Get-MsolUser -SearchString tuser1 | Select-Object -ExpandProperty LiveID -
In the resource tenant, convert the value of the
keyattribute withinAlternativeSecurityIdsto a base64-encoded string:[convert]::ToBase64String((Get-MsolUser -ObjectId 01234567-89ab-cdef-0123-456789abcdef ).AlternativeSecurityIds.key) -
Convert the base64-encoded string to a hexadecimal value by using an online converter (such as base64.guru).
-
Compare the values from step 1 and step 3 to verify that they’re different. The
NetIDof the user account in the home tenant changed when the account was deleted and re-created.
Solution: Reset the redemption status of the guest user account
Reset the redemption status of the guest user account in the resource tenant. Then, you can keep the guest user object without having to delete and then re-create the guest account. You can reset the redemption status by using the Azure portal, Azure PowerShell, or the Microsoft Graph API. For instructions, see Reset redemption status for a guest user.
[!INCLUDE Azure Help Support]
I am developing a desktop app with Java for a uni project and I have used Azure Active Directory to register the app. I am very new with all of this so please forgive me if I have misunderstood something. I had no problems with Azure AD until this week. When logging into the portal I am receiving the following error message:
The portal is having issues getting an authentication token. The experience rendered may be degraded.
Additional information from the call to get a token:
Extension: Microsoft_AAD_IAM
Resource: microsoft.graph
Details: The logged in user is not authorized to fetch tokens for extension ‘Microsoft_AAD_IAM’ because the user account is not a member of tenant ‘f8cdef31-a31e-4b4a-93e4-5f571e91255a’.
Error details: AADSTS50020: User account ‘{EmailHidden}’ from identity provider ‘live.com’ does not exist in tenant ‘Microsoft Services’ and cannot access the application ‘c44b4083-3bb0-49c1-b47d-974e53cbdf3c'(Azure Portal) in that tenant. The account needs to be added as an external user in the tenant first.
Sign out and sign in again with a different Azure Active Directory user account.
Trace ID: 4b11e8b6-8400-4a15-8553-270679f41300
Correlation ID: f0f3259b-9c04-4299-82c3-9d88a994c91c
Timestamp: 2022-04-03 15:02:23Z
This happens every time I try to access ANYTHING on the Azure dashboard. I have tried clearing my browser’s history and cookies, using a private browser, using a different browser, using a different device, using a different network and nothing has worked.
I really don’t know what caused this since I am fairly convinced I didn’t change anything, so I don’t know why the (personal) account I have been using the whole time would now not be a part of the tenant. But since (I think) I am the admin, I have no way of accessing the ‘Users’ page of Azure AD and adding me back to the tenant as a user. I can’t even create a new support request the Help + Support page as it just hangs — probably due to this authentication error.
Any guidance or help would be very much appreciated, thank you.
#office-addins #azure-ad-graph-api
#дополнения office #azure-ad-graph-api
Вопрос:
Я смог зарегистрировать приложение, созданное другим клиентом, как корпоративное приложение моего собственного клиента. Я вошел в приложение как пользователь, но получил следующую ошибку.
AADSTS50020: учетная запись пользователя ‘test001@testdomain001.onmicrosoft.com » от поставщика удостоверений личности «https://sts.windows.net/aaaaaaaa-bbbb-cccc-dddd-eeeeeeeeeeee /’ не существует в клиенте ‘testdomain002’ и не может получить доступ к приложению ‘55555555-6666-7777-8888-999999999999’ (OneDriveAPIBrowser_test001) в этом клиенте. Сначала необходимо добавить учетную запись в качестве внешнего пользователя в клиенте. Выйдите и войдите снова с другой учетной записью пользователя Azure Active Directory.
Как пользователь другого клиента может использовать ее без выполнения какой-либо обработки клиентом-создателем приложения?
Комментарии:
1. В каком клиенте зарегистрировано ваше приложение Azure AD? testdomain001 или testdomain002?
2. Та же ошибка. За исключением того, что я пытаюсь войти в систему с учетной записью, которая является владельцем организации. Как владелец, который является глобальным администратором, может быть не авторизован?
Ответ №1:
Если приложение Azure AD зарегистрировано в клиенте A и вы добавили его как корпоративное приложение в клиент B, для входа в систему следует использовать пользователя из клиента B.
В вашем случае, если зарегистрированное приложение находится в testdomain001 и добавлено в testdomain002, вам необходимо использовать пользователя из testdomain002. Пользователь «test001@testdomain001.onmicrosoft.com » не разрешается входить в приложение в testdomain002, если он не является гостевым пользователем testdomain002.
Комментарии:
1. Спасибо за ответ. Моего объяснения было недостаточно. Взаимосвязь следующая. Tenant A = testdomain001 = Создатель приложения Tenant B = testdomain002 = Пользователь приложения Регистрация приложения для клиента B была завершена администратором клиента B. Ошибка AADSTS50020 произошла, когда пользователь tenant B попытался использовать приложение. Есть ли способ заставить пользователей Tenant B использовать приложение только с работой Tenant B.
2. @MuneSeiji Спасибо за ваше объяснение. Но, судя по вашему сообщению об ошибке, вы используете эту учетную запись ‘test001@testdomain001.onmicrosoft.com ‘который принадлежит Арендатору A (а не арендатору B) для использования приложения. В любом случае, я думаю, что понял вашу идею. Вам нужно указать полномочия как
https://login.microsoftonline.com/{tenant B}/oauth2/v2.0/authorize, а неhttps://login.microsoftonline.com/{tenant A}/oauth2/v2.0/authorizeилиhttps://login.microsoftonline.com/common/oauth2/v2.0/authorize. И не забудьте использовать пользователя из клиента B.3. Спасибо за быстрый ответ. Поскольку приложение не предназначено для конкретного клиента, я подумал об использовании ‘ login.microsoftonline.com/common/oauth2/v2.0/authorize «. И я понял, что для использования ‘common’ вместо идентификатора клиента необходимо правильно создать приложение. Приложение использует ‘ github.com/OneDrive/onedrive-sample-apibrowser-dotnet — как есть, но я не совсем понимаю это. Я до сих пор не понимаю API аутентификации в деталях. Начните с ознакомления с API аутентификации.
4. @MuneSeiji Если вам нужно использовать
common, просто убедитесь, что вам нужно зарегистрировать приложение как многопользовательское приложение. См. i.stack.imgur.com/xebls.png .5. @MuneSeiji С какой проблемой вы столкнулись сейчас? Можете ли вы объяснить это подробно? Исходя из обсуждаемой нами информации, причина этой проблемы заключается в том, что для входа в систему используется пользователь из клиента A. Но здесь вы должны использовать пользователя tenant B.
Ответ №2:
Я попробовал следующие шаги, и у меня это сработало.
-
Перейдите к azure.microsoft.com
-
Выберите Бесплатную учетную запись.
-
Войдите в систему с помощью своей электронной почты.
-
Он обнаружит, что у вас уже есть подписка, и предоставит вам возможность ее использовать.
I am working on an app that manages azure resources for customers (provision VMs, create VNets).
We have created a multi-tenant application in the azure portal that is configured for Delegated permissions of Windows Azure Service Management API and Windows Azure Active Directory.
We are able to login AAD based account without a problem. But when a live.com based account logs in, the user gets a AADSTS50020 error.
We for the login, we are navigating to https://login.microsoftonline.com/common/OAuth2/Authorize
with the following parameters:
client_id=XXX&response_mode=query&response_type=code&redirect_uri=XXX&prompt=consent
Here is the full error message:
AADSTS50020: User account ‘xxx@hotmail.com’ from identity provider
‘live.com’ does not exist in tenant ‘XXX’ and cannot access the
application ‘xxx’ in that tenant. The account needs to be added as an
external user in the tenant first. Sign out and sign in again with a
different Azure Active Directory user account.
asked Mar 10, 2017 at 22:03
Michael SabinMichael Sabin
1,6791 gold badge20 silver badges33 bronze badges
4
You need to use V2 endpoints in order to allow access from personal microsoft accounts. I run into the same problems by using the v1 endpoint.
Use this endpoint:
https://login.microsoftonline.com/common/oauth2/v2.0/authorize
For example:
https://login.microsoftonline.com/common/oauth2/v2.0/authorize
?client_id=ffffff-1111-2222-3333-37fd4f8c20ee
&response_type=id_token
&redirect_uri=http://localhost:8080/login/microsoft/callback
&response_mode=form_post
&prompt=consent
&scope=openid
&state=12345
&nonce=RandomGUI
Good luck
answered Sep 5, 2019 at 19:14
In this article, we will discuss possible fixes to resolve the AADSTS50020, User account from identity provider does not exist in tenant error. This error usually occurs when a guest user from an identity provider (IdP) can’t sign in to a resource tenant in Azure Active Directory (Azure AD). You may see this error in different situations. Each situation requires a different way to troubleshoot.
The complete error message that the guest user sees when trying to access an application or resource in the resource tenant is:
AADSTS50020: User account ‘[email protected]’ from identity provider {IdentityProviderURL} does not exist in tenant {ResourceTenantName}.
On reviewing the logs on the home tenant, the administrator will see the following error message:
User account {email} from identity provider {idp} does not exist in tenant {tenant} and cannot access the application {appId}({appName}) in that tenant. The account needs to be added as an external user in the tenant first. Sign out and sign in again with a different Azure Active Directory user account.
The solutions below will help you fix the AADSTS50020, User account from identity provider does not exist in tenant error.
- Change the sign-in audience setting in the app registration manifest
- Use the correct sign-in URL
- Sign out, then sign in again from a different browser or a private browser session
- Invite the guest user
- Assign access to users (if applicable)
- Use an endpoint that’s specific to the tenant or organization
- Reset the redemption status of the guest user account
Let’s see all these fixes in detail.
1] Change the sign-in audience setting in the app registration manifest
One possible cause of this error is when a tenant uses an unsupported account type. For example, If a single-tenant account type is set for your app registration, a user from another identified provider can’t sign in to the application.
To fix the AADSTS50020 error, change the sign-in audience setting in the app registration manifest as follows:
- Go to the Azure portal.
- Select App registrations.
- Select the name of your app registration.
- Select Manifest, from the Sidebar.
- In the JSON code, find the signInAudience setting.
- Check the setting from one of the following values:
-
- AzureADandPersonalMicrosoftAccount
- AzureADMultipleOrgs
- PersonalMicrosoftAccount
The SignInAudience should contain one of the above-mentioned values. If you do not find any of these values in the SignInAudience setting, you have to create the app registration again.
2] Use the correct sign-in URL
Another cause of this error is using the incorrect sign-in URL. For example, if you use https://login.Microsoftonline.com/<YourTenantNameOrID> URL, the authentication is expected to be run on your tenant only. That’s why users in other organizations cannot access the application. When other users try to do so, they will receive a sign-in error.
To resolve this problem, you must add these users as guests in the tenant specified in the request. You can use the corresponding sign-in URL for a specific type of application. Some examples are mentioned below:
For the Multitenant applications type, you can use the following sign-in URL.
https://login.microsoftonline.com/organizations
If you’re using Multitenant and personal accounts type, then you can use the following sign-in URL.
https://login.microsoftonline.com/common
For personal accounts only, use this sign-in URL.
https://login.microsoftonline.com/consumers
3] Sign out, then sign in again from a different browser or a private browser session
Sometimes this error occurs when the user signed in to the wrong tenant. For example, when a user already has an active session in his web browser and he/she tries to access your application by clicking on the respective link or entering the required URL in a new tab.
In this situation, ask the guest user to do one of the following things:
- Sign out of the account already opened in his/her web browser. This will end the already active session. Now, he/she can sign in by using the correct link and credentials.
- Sign in using a different web browser.
- Sign in in the Private or Incognito window in the same web browser.
4] Invite the guest user
This error also appears when the guest user is not invited. The solution to this situation is straightforward. Invite the guest user.
5] Assign access to users (if applicable)
If your application is an enterprise application that requires user assignment and the user is not in the list of allowed users who have been assigned access to the application, then this error will occur.
You can check if your enterprise application requires user assignment or not by following the steps provided below:
- Go to the Azure portal.
- Select the Enterprise application(s).
- Select your enterprise application.
- Select Properties.
- Check whether the Assignment Required option is set to Yes. If it is set to Yes, then that application requires the user assignment.
In this situation, Assign access to users individually or as part of a group.
6] Use an endpoint that’s specific to the tenant or organization
The error code AADSTS50020 can also occur when a user tries to use the Resource Owner Password Credential (ROPC) flow for his/her personal account(s). Microsoft Identity Platform only supports ROPC within Azure AD tenants and not personal accounts.
In this situation, the user has to use the endpoint that is specific to the tenant or organization. Do note that personal accounts cannot use ROPC even if they are invited to an Azure AD tenant.
7] Reset the redemption status of the guest user account
If the administrator has deleted the username of the guest user in the resource tenant and re-created it in the home tenant, the guest user will encounter this error. The administrator should also verify that the guest user account in the resource tenant is not associated with the guest user account in the home tenant.
To fix the error in this situation, reset the redemption status of the guest user account in the resource tenant.
That’s it. I hope this helps.
What tenant ID is used in Azure?
The tenant ID in Azure is a unique identifier for an Azure Active Directory (Azure AD) tenant. It is also called Office 365 tenant ID. There are different ways to get your Azure Tenant ID.
Who is tenant admin?
A tenant admin is a user who has the highest level of permissions in an Azure Active Directory (Azure AD) tenant. He/she can manage all aspects of the tenant, including users, groups, permissions, and settings.
Read next: Error AADSTS90100, Login Parameter is empty or not valid.