ИД события 4000:
DNS-серверу не удалось открыть Active Directory. Этот DNS-сервер настроен на получение и использование сведений из каталога для этой зоны и не может загрузить зону без нее. Убедитесь, что Active Directory работает правильно, и перезагрузим зону. Данные события — это код ошибки.
The DNS server was unable to open Active Directory. This DNS server is configured to obtain and use information from the directory for this zone and is unable to load the zone without it. Check that the Active Directory is functioning properly and reload the zone. The event data is the error code.
ИД события 4007:
DNS-серверу не удалось открыть зону в Active Directory из раздела <zone> каталога <partition name> приложений. Этот DNS-сервер настроен на получение и использование сведений из каталога для этой зоны и не может загрузить зону без нее. Убедитесь, что Active Directory работает правильно, и перезагрузим зону. Данные события — это код ошибки.
The DNS server was unable to open zone <zone> in the Active Directory from the application directory partition <partition name>. This DNS server is configured to obtain and use information from the directory for this zone and is unable to load the zone without it. Check that the Active Directory is functioning properly and reload the zone. The event data is the error code.
Решение
Если в среде есть другой контроллер домена или DNS-сервер, настройте сервер, на который возникли проблемы, чтобы указать на другой активный DNS-сервер в свойствах TCP/IP.
- Остановите службу KDC на dc, где возникли проблемы.
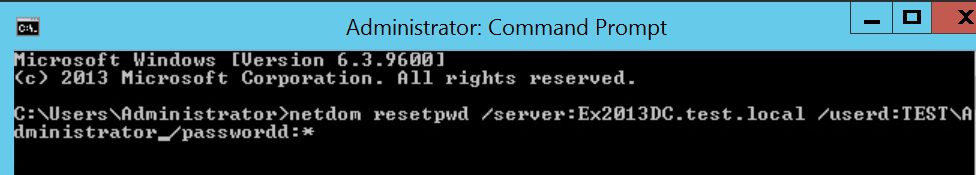
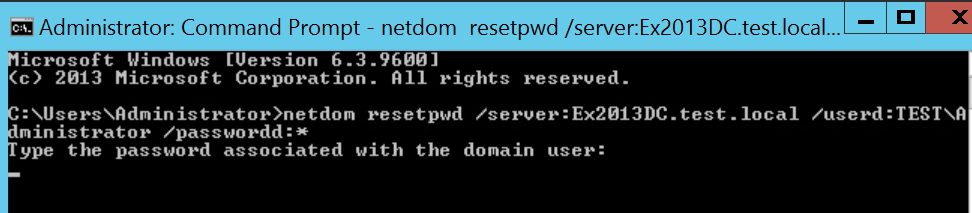
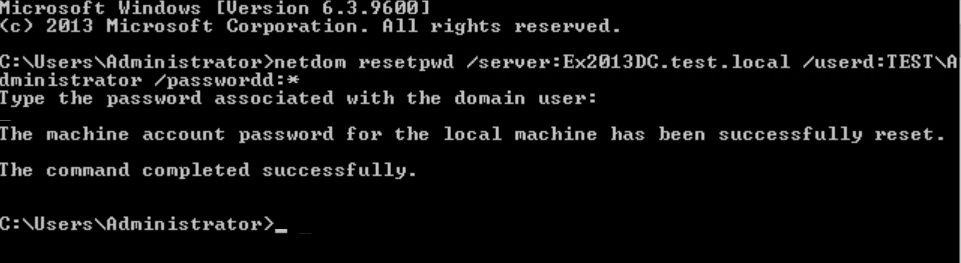
net stop KDC- Запустите следующую команду с повышенными правами:
netdom resetpwd /server:<PDC.domain.com> /userd:<Domain\domain_admin> /passwordd:*
пример: netdom resetpwd /server:10.0.10.10 /userd:mydomain.local\VasyaVS /passwordd:MyPassw0rd
- Включаем службу KDC на dc.
net start KDC- Синхронизируем изменения и убедимся, что ошибок при выполнении команды нет:
repadmin /syncall- Перезагружаем сервер
Остановите службу KDC на контроллере домена, в котором возникла ошибка.
Выполните следующую команду с повышенными правами:
c:/> netdom resetpwd /server:servername /userd:domain\domain_admin /password: *Запросит пароль учетной записи администратора домена, можно использовать, введите.
После выполнения команды перезагрузите сервер.
Теперь следует загрузить DNS-зонах.
Если это является единственным контроллером домена в среде и нет других DNS-серверов выполните те же шаги но replate «PDC. Domain.com» с IP-адресом сервера (поскольку он сам по себе является основной контроллер домена)
- Remove From My Forums
-
Вопрос
-
Hi,
I’m having problems with the DNS server that lauches a 4000 error, on a 2008 r2 server.
After reading about the problem, one of the steps is to report the dcdiag output. But here there are problems to… so the output is:
Directory Server Diagnosis Performing initial setup: Trying to find home server... Home Server = kaos * Identified AD Forest. Done gathering initial info. Doing initial required tests Testing server: Default-First-Site-Name\KAOS Starting test: Connectivity The host 18c0aea1-dec5-445e-b4df-0d593f8994ee._msdcs.EPBJCPORTO.LAN could not be resolved to an IP address. Check the DNS server, DHCP, server name, etc. Got error while checking LDAP and RPC connectivity. Please check your firewall settings. ......................... KAOS failed test Connectivity Doing primary tests Testing server: Default-First-Site-Name\KAOS Skipping all tests, because server KAOS is not responding to directory service requests. Running partition tests on : ForestDnsZones Starting test: CheckSDRefDom ......................... ForestDnsZones passed test CheckSDRefDom Starting test: CrossRefValidation ......................... ForestDnsZones passed test CrossRefValidation Running partition tests on : DomainDnsZones Starting test: CheckSDRefDom ......................... DomainDnsZones passed test CheckSDRefDom Starting test: CrossRefValidation ......................... DomainDnsZones passed test CrossRefValidation Running partition tests on : Schema Starting test: CheckSDRefDom ......................... Schema passed test CheckSDRefDom Starting test: CrossRefValidation ......................... Schema passed test CrossRefValidation Running partition tests on : Configuration Starting test: CheckSDRefDom ......................... Configuration passed test CheckSDRefDom Starting test: CrossRefValidation ......................... Configuration passed test CrossRefValidation Running partition tests on : EPBJCPORTO Starting test: CheckSDRefDom ......................... EPBJCPORTO passed test CheckSDRefDom Starting test: CrossRefValidation ......................... EPBJCPORTO passed test CrossRefValidation Running enterprise tests on : EPBJCPORTO.LAN Starting test: LocatorCheck ......................... EPBJCPORTO.LAN passed test LocatorCheck Starting test: Intersite ......................... EPBJCPORTO.LAN passed test Intersitethe network config is this (ipconfig /all output)
Windows IP Configuration Host Name . . . . . . . . . . . . : kaos Primary Dns Suffix . . . . . . . : EPBJCPORTO.LAN Node Type . . . . . . . . . . . . : Hybrid IP Routing Enabled. . . . . . . . : No WINS Proxy Enabled. . . . . . . . : No DNS Suffix Search List. . . . . . : EPBJCPORTO.LAN Ethernet adapter Local Area Connection 2: Connection-specific DNS Suffix . : Description . . . . . . . . . . . : Intel(R) PRO/1000 PM Network Connection Physical Address. . . . . . . . . : 00-15-17-50-07-1A DHCP Enabled. . . . . . . . . . . : No Autoconfiguration Enabled . . . . : Yes IPv4 Address. . . . . . . . . . . : 192.168.1.1(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 192.168.1.254 DNS Servers . . . . . . . . . . . : 192.168.1.1 Primary WINS Server . . . . . . . : 192.168.1.1 NetBIOS over Tcpip. . . . . . . . : Enabled Ethernet adapter Local Area Connection: Media State . . . . . . . . . . . : Media disconnected Connection-specific DNS Suffix . : Description . . . . . . . . . . . : Intel(R) PRO/1000 MT Network Connection Physical Address. . . . . . . . . : 00-15-17-50-07-1B DHCP Enabled. . . . . . . . . . . : Yes Autoconfiguration Enabled . . . . : Yes Tunnel adapter isatap.{BBA6ABAF-7E07-4241-975E-F9FD5655F86D}: Media State . . . . . . . . . . . : Media disconnected Connection-specific DNS Suffix . : Description . . . . . . . . . . . : Microsoft ISATAP Adapter Physical Address. . . . . . . . . : 00-00-00-00-00-00-00-E0 DHCP Enabled. . . . . . . . . . . : No Autoconfiguration Enabled . . . . : Yes Tunnel adapter isatap.{7A57B408-0A28-4129-A7E9-90AD1AD3ECEE}: Media State . . . . . . . . . . . : Media disconnected Connection-specific DNS Suffix . : Description . . . . . . . . . . . : Microsoft ISATAP Adapter #2 Physical Address. . . . . . . . . : 00-00-00-00-00-00-00-E0 DHCP Enabled. . . . . . . . . . . : No Autoconfiguration Enabled . . . . : Yes Tunnel adapter Teredo Tunneling Pseudo-Interface: Connection-specific DNS Suffix . : Description . . . . . . . . . . . : Teredo Tunneling Pseudo-Interface Physical Address. . . . . . . . . : 00-00-00-00-00-00-00-E0 DHCP Enabled. . . . . . . . . . . : No Autoconfiguration Enabled . . . . : Yes IPv6 Address. . . . . . . . . . . : 2001:0:5ef5:79fd:84b:7d52:a83b:ac5(Preferred) Link-local IPv6 Address . . . . . : fe80::84b:7d52:a83b:ac5%15(Preferred) Default Gateway . . . . . . . . . : :: NetBIOS over Tcpip. . . . . . . . : Disabledthe 192.168.1.254 gateway is proxy under linux (endia)
thanks in advance
Carlos
PS:sorry my bad english
Ответы
-
Solved!
the step were:
analyzing the hosts file i’ve detected this entry:
127.0.0.1 localhost127.0.0.1 localhosti haven’t edit this file, so i don’t understand how became like this !?!?!
then edit the hosts file putting this entries (because of the dcdiag error reported):
127.0.0.1 localhost
192.168.1.1 18c0aea1-dec5-445e-b4df-0d593f8994ee._msdcs.EPBJCPORTO.LANthen activate IPV6 protocol in the NIC et voila, access to DNS role permitted.
Thanks all for your support!
-
Помечено в качестве ответа
11 апреля 2011 г. 8:24
-
Помечено в качестве ответа
Recently we had “Patch Monday” – unusual since we usually patch on Fridays (in case something goes wrong we have weekend ahead), but this one time was good opportunity since there was some infrastructure work and we had planed downtime and we took the opportunity to patch.
Unfortunately something went very wrong. First after rebooting one of the Exchange servers I got following error:
Exchange ECP / The LDAP Server is unavailable
“Topology Provider couldn’t find the Microsoft Exchange Active Directory”
In logs event id 2142 MSExchangeADTopology was logged with error “Topology discovery failed”
At first I thought it was a bad patch, but soon after that still unpatched Exchange
reported errors.
Errors obviously point to AD. I looked at domain controller since it also was updated. Immediately after logging onto DC I was greeted with unpleasant surprise.
After opening DNS console “Access Denied” message appeared.
DNS was unreachable.
On DC following events were logged:
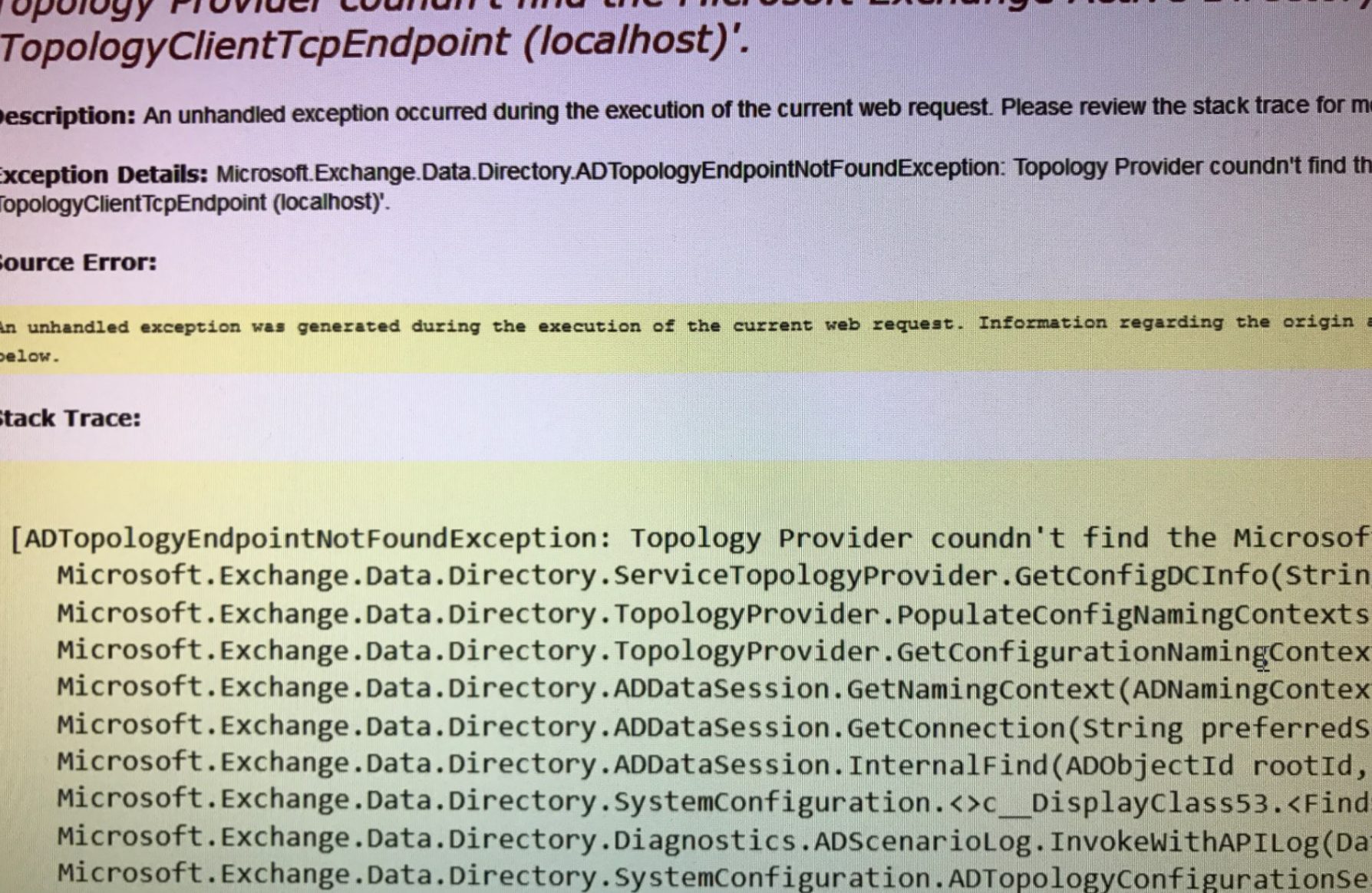
Microsoft-Windows-DNS-Server-Service Event ID 4000
The description for Event ID ( 4000 ) in Source ( Microsoft-Windows-DNS-Server-Service ) cannot be found. Either the component that raises this event is not installed on your local computer, or the installation is corrupted. You can install or repair the component on the local computer, or contact the component manufacturer for a newer version.
If the event was saved from another computer or forwarded from a remote computer, you might have to include display information with the events when saving them or when setting up the forwarding s
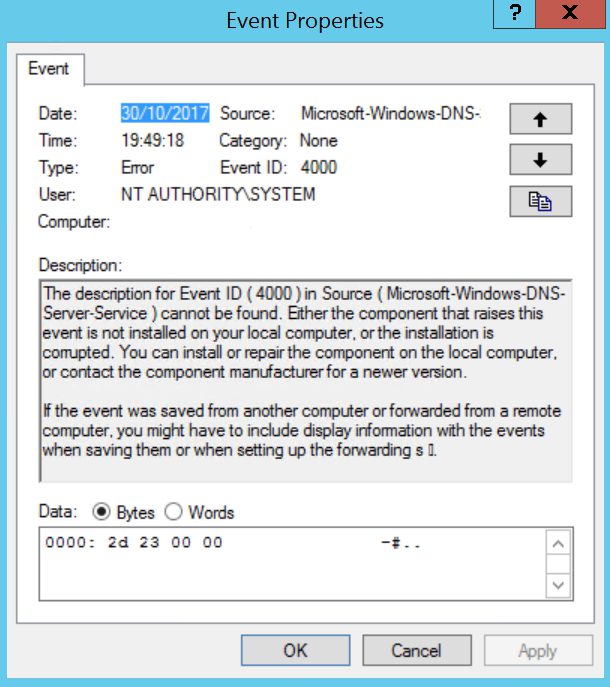
Microsoft-Windows-DNS-Server-Service Event ID 4007
The description for Event ID ( 4007 ) in Source ( Microsoft-Windows-DNS-Server-Service ) cannot be found. Either the component that raises this event is not installed on your local computer, or the installation is corrupted. You can install or repair the component on the local computer, or contact the component manufacturer for a newer version.
If the event was saved from another computer or forwarded from a remote computer, you might have to include display information with the events when saving them or when setting up the forwarding
According to Microsoft / https://support.microsoft.com/en-us/help/2751452/dns-zones-do-not-load–event-4000–4007 this happens in two cases:
This happens when that particular DC/DNS server has lost its Secure channel with itself or PDC.
This can also happen in a single DC environment where that DC/DNS server holds all the FSMO roles and is pointing to itself as Primary DNS server.
I’m still not sure why this happened in my case, but here are steps that resolved this problem for me
Stop KDC (Kerberos Key Distribution Center) Service in Service Console on DC that doesn’t work.
Run command prompt with elevated priviledges (as Administrator) and enter following command
netdom resetpwd /server:DC.domain.local /userd:Domain\domain_admin /passwordd:*(change dc.domain.local with fqdn of your DC, and DOMAIN\domain_admin with your domain and admin account)
You will be prompted for the password. Enter domain admin password that you use for that account.
Once command is executed restart the server.
DNS zones after that worked for me and Exchange Servers were fine.
Disclaimer
Server 20012 R2 — Single DC in Windows Domain
This morning after an after-hours server reboot (power outage — the single domain DC is on a very good UPS and the restart appears to have been flawless) our DNS Server service would not start. A network admin removed, then re-installed the DNS Role.
Now DNS queries by domain PCs and over WiFI VLAN are able to resolve DNS queries using the domain DNS. Everyone can log-on to the domain now, and everyone has Internet access. PIng to FQDN of the server (DC) results in the correct LAN IP.
Event Viewer still shows — DNS Server, Event ID 4000, connect to Active Directory
Log Name: DNS Server
Source: Microsoft-Windows-DNS-Serv
Date: 10/3/2014 9:34:42 AM
Event ID: 4000
Task Category: None
Level: Error
Keywords: (65536)
User: SYSTEM
Computer: Server1.ourdomain.local
Description:
The DNS server was unable to open Active Directory. This DNS server is configured to obtain and use information from the directory for this zone and is unable to load the zone without it. Check that the Active Directory is functioning properly and reload the zone. The event data is the error code.
Event Xml:
<Event xmlns=»http://schemas.microsoft.com/win/2004/08/events/event»>
<System>
<Provider Name=»Microsoft-Windows-DN
<EventID>4000</EventID>
<Version>0</Version>
<Level>2</Level>
<Task>0</Task>
<Opcode>0</Opcode>
<Keywords>0x80000000000100
<TimeCreated SystemTime=»2014-10-03T14:
<EventRecordID>9619</Event
<Correlation />
<Execution ProcessID=»2888″ ThreadID=»7808″ />
<Channel>DNS Server</Channel>
<Computer>Server1.ourdomai
<Security UserID=»S-1-5-18″ />
</System>
<EventData Name=»DNS_EVENT_DS_OPEN_FA
<Binary>2D230000</Binary>
</EventData>
</Event>
Event Viewer logs for Active Directory list many Event ID 1202 instances
Log Name: Active Directory Web Services
Source: ADWS
Date: 10/3/2014 9:22:49 AM
Event ID: 1202
Task Category: ADWS Instance Events
Level: Error
Keywords: Classic
User: N/A
Computer: Server1.ourdomainsa.local
Description:
This computer is now hosting the specified directory instance, but Active Directory Web Services could not service it. Active Directory Web Services will retry this operation periodically.
Directory instance: NTDS
Directory instance LDAP port: 389
Directory instance SSL port: 636
Event Xml:
<Event xmlns=»http://schemas.microsoft.com/win/2004/08/events/event»>
<System>
<Provider Name=»ADWS» />
<EventID Qualifiers=»49152″>1202</E
<Level>2</Level>
<Task>3</Task>
<Keywords>0x80000000000000
<TimeCreated SystemTime=»2014-10-03T14:
<EventRecordID>1498</Event
<Channel>Active Directory Web Services</Channel>
<Computer>Server1.ourdomai
<Security />
</System>
<EventData>
<Data>NTDS</Data>
<Data>389</Data>
<Data>636</Data>
</EventData>
</Event>
Attempting to open the DNS Role from the Server Manager console results in the error message:
«The server SERVER1 could not be contacted.
The error was:
Access was denied.
Would you like to add it anyway?»
Clicking «Yes» results in the following error:
«The server SERVER1.ourdomain.local could not be contacted.
The error was:
Access was denied.
Would you like to add is anyway?»
Then the DNS Manager will open, but the DNS servers listed have red error signs over them and all that is available form the context menus of each is to stop and start the service.
RESULTING PROBLEMS ON LAN: Users connection to the file server using FQDN ( \\server1\ ) are now queried for user name/password authentication and all credentials FAIL — even the default domain admin’s.
Save results if users connect to the file server by IP ( \\192.168.xxx.xxx\ ) they are asked for domain credentials and are told they do not have permission to access.
Connection to the NAS by FQDN results in a connection, but requests domain credentials all FAIL.
Obviously this is due to the DNS Server service and Active Directory not communicating at all.
Anyone been through this or know the solution to the Event ID 4000 ?
No one on the network can connect to any share on the server or the NAS.
The DNS Server cannot connect to AD. We can not access the DNS Server form the DC it is hosted on.
Anyone? Anyone?
Thanks,
-MP