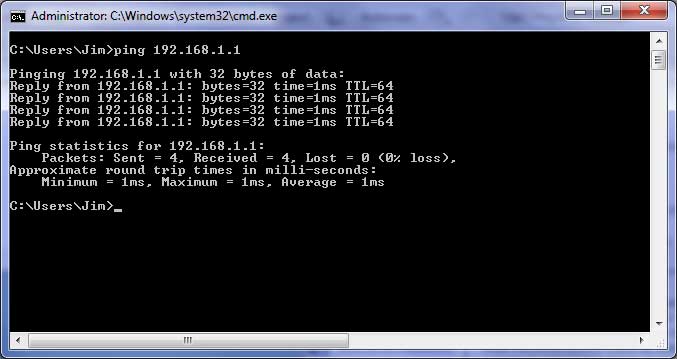
Ping is a network tool mainly used to test whether a host is reachable across an IP network and to measure the round-trip time for packets sent from the source to the destination computer. Ping works by sending Internet Control Message Protocol (ICMP) echo request packets to the destination host and waits for an ICMP response. It also measures the time it takes for the packets to return.
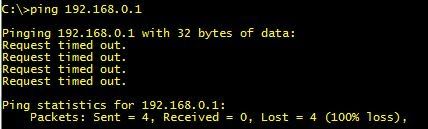
When you are unable to “ping” the destination host either by IP Address or by hostname, you should pay close attention to the results provided by ICMP. Different messages indicate different types of issues. The three most common error messages that you will see are as follows:
- Destination Host Unreachable
- Request Timed Out
- Ping Request Could Not Find Host
Within the ICMP header, you can find more information about the type and code. If you were to examine the ICMP packets containing these messages, more details regarding error message can be discovered. You can refer to this IANA link for more information regarding types and codes for ICMP. http://www.iana.org/assignments/icmp parameters
If the ping command is successful in reaching the destination computer, an examination of the packets sent and received will only show Echo Requests (type 
Destination Host Unreachable
The Destination Host Unreachable error message indicates that a route to the destination node cannot be found. To resolve this problem, you might need to examine the routing information on the local host to confirm that the local host is correctly configured.
Common issues that generate this type of error message is the local host not configured with a default gateway. If the local computer’s TCP/IP configuration is correct, you can still receive this message from your gateway. This would indicate that your gateway does not have information in the routing table to successfully route the packet to the destination host.
Request Timed Out
The Request Timed Out error message is very common when you use the ping command. Essentially, this error message indicates that your host did not receive the ICMP Echo Reply back from the destination node within the designated time period.
Assuming network connectivity is not the source of the problem, this is generally an indication that the destination node is not connected to the network, powered off, or is not configured correctly in regards to its TCP/IP configuration. It is possible to encounter these messages when there is heavy congestion on the network since ICMP packets are commonly treated with the lowest priority on the network.
Ping Request Could Not Find Host…
If you see this error message, PING was unable to determine the IP address from the hostname provided. Either there was a typo in the hostname, or your name resolution process failed in resolving the IP address for the hostname provided. Check to make sure the hostname is correct.
From Wikipedia, the free encyclopedia

Linux version of ping |
|
| Original author(s) | Mike Muuss |
|---|---|
| Developer(s) | Various open-source and commercial developers |
| Initial release | 1983; 40 years ago |
| Platform | Cross-platform |
| Type | Command |
| License | Public-domain, BSD, GPL, MIT |
ping is a computer network administration software utility used to test the reachability of a host on an Internet Protocol (IP) network. It is available for virtually all operating systems that have networking capability, including most embedded network administration software.
Ping measures the round-trip time for messages sent from the originating host to a destination computer that are echoed back to the source. The name comes from active sonar terminology that sends a pulse of sound and listens for the echo to detect objects under water.[1]
Ping operates by means of Internet Control Message Protocol (ICMP) packets. Pinging involves sending an ICMP echo request to the target host and waiting for an ICMP echo reply. The program reports errors, packet loss, and a statistical summary of the results, typically including the minimum, maximum, the mean round-trip times, and standard deviation of the mean.
The command-line options of the ping utility and its output vary between the numerous implementations. Options may include the size of the payload, count of tests, limits for the number of network hops (TTL) that probes traverse, interval between the requests and time to wait for a response. Many systems provide a companion utility ping6, for testing on Internet Protocol version 6 (IPv6) networks, which implement ICMPv6.
History[edit]
The ping utility was written by Mike Muuss in December 1983 during his employment at the Ballistic Research Laboratory, now the US Army Research Laboratory. A remark by David Mills on using ICMP echo packets for IP network diagnosis and measurements prompted Muuss to create the utility to troubleshoot network problems.[1] The author named it after the sound that sonar makes, since its methodology is analogous to sonar’s echolocation.[1][2] The backronym Packet InterNet Groper for PING has been used for over 30 years,[timeframe?] and although Muuss says that from his point of view PING was not intended as an acronym, he has acknowledged Mills’ expansion of the name.[1][3] The first released version was public domain software; all subsequent versions have been licensed under the BSD license. Ping was first included in 4.3BSD.[4] The FreeDOS version was developed by Erick Engelke and is licensed under the GPL.[5] Tim Crawford developed the ReactOS version. It is licensed under the MIT License.[6]
RFC 1122 prescribes that any host must process ICMP echo requests and issue echo replies in return.[7]
Invocation example[edit]
The following is the output of running ping on Linux for sending five probes (1-second interval by default, configurable via -i option) to the target host www.example.com:
$ ping -c 5 www.example.com PING www.example.com (93.184.216.34): 56 data bytes 64 bytes from 93.184.216.34: icmp_seq=0 ttl=56 time=11.632 ms 64 bytes from 93.184.216.34: icmp_seq=1 ttl=56 time=11.726 ms 64 bytes from 93.184.216.34: icmp_seq=2 ttl=56 time=10.683 ms 64 bytes from 93.184.216.34: icmp_seq=3 ttl=56 time=9.674 ms 64 bytes from 93.184.216.34: icmp_seq=4 ttl=56 time=11.127 ms --- www.example.com ping statistics --- 5 packets transmitted, 5 packets received, 0.0% packet loss round-trip min/avg/max/stddev = 9.674/10.968/11.726/0.748 ms
The output lists each probe message and the results obtained. Finally, it lists the statistics of the entire test. In this example, the shortest round trip time was 9.674 ms, the average was 10.968 ms, and the maximum value was 11.726 ms. The measurement had a standard deviation of 0.748 ms.
Error indications[edit]
In cases of no response from the target host, most implementations display either nothing or periodically print notifications about timing out. Possible ping results indicating a problem include the following:
- H, !N or !P – host, network or protocol unreachable
- S – source route failed
- F – fragmentation needed
- U or !W – destination network/host unknown
- I – source host is isolated
- A – communication with destination network administratively prohibited
- Z – communication with destination host administratively prohibited
- Q – for this ToS the destination network is unreachable
- T – for this ToS the destination host is unreachable
- X – communication administratively prohibited
- V – host precedence violation
- C – precedence cutoff in effect
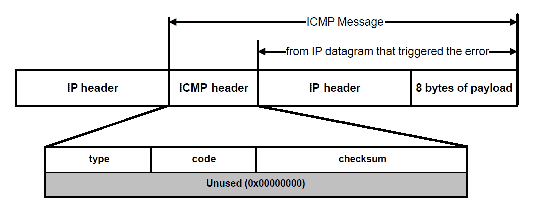
In case of error, the target host or an intermediate router sends back an ICMP error message, for example host unreachable or TTL exceeded in transit. In addition, these messages include the first eight bytes of the original message (in this case header of the ICMP echo request, including the quench value), so the ping utility can match responses to originating queries.[8]
Message format[edit]
ICMP packet[edit]
| Bits 0–7 | Bits 8–15 | Bits 16–23 | Bits 24–31 | |
|---|---|---|---|---|
| Header (20 bytes) |
Version/IHL | Type of service (ToS) | Length | |
| Identification | flags and offset | |||
| Time to live (TTL) | Protocol | Header checksum | ||
| Source IP address | ||||
| Destination IP address | ||||
| ICMP header (8 bytes) |
Type of message | Code | Checksum | |
| Header data | ||||
| ICMP payload (optional) |
Payload data |
| Bits 0–3 | Bits 4–7 | Bits 8–11 | Bits 12–15 | Bits 16–23 | Bits 24–31 | |
|---|---|---|---|---|---|---|
| Header (40 bytes) |
Version | Traffic class | Flow label | |||
| Payload length | Next header | Hop limit | ||||
| Source address (128 bits) | ||||||
| Destination address (128 bits) | ||||||
| ICMP6 header (8 bytes) |
Type of message | Code | Checksum | |||
| Header data | ||||||
| ICMP6 payload (optional) |
Payload data |
Generic composition of an ICMP packet:[9]
- IPv4 Header (in blue): protocol set to 1 (ICMP) and Type of Service set to 0.
- IPv6 Header (in blue): Next Header set to 58 (ICMP6)
- ICMP Header (in red):
- Type of ICMP message (8 bits)
- Code (8 bits)
- Checksum (16 bits), the 16-bit one’s complement of the one’s complement sum of the packet. For IPv4, this is calculated from the ICMP message starting with the Type field[10] (the IP header is not included). For IPv6 this is calculated from the ICMP message, prepended with an IPv6 pseudo-header.[11]
- Header Data (32 bits) field, which in this case (ICMP echo request and replies), will be composed of an identifier (16 bits) and sequence number (16 bits).
- ICMP Payload: payload for the different kind of answers; can be an arbitrary length, left to implementation detail. However, the packet including IP and ICMP headers must be less than the maximum transmission unit of the network or risk being fragmented.
Echo request[edit]
The echo request (ping) is an ICMP/ICMP6 message.
| 00 | 01 | 02 | 03 | 04 | 05 | 06 | 07 | 08 | 09 | 10 | 11 | 12 | 13 | 14 | 15 | 16 | 17 | 18 | 19 | 20 | 21 | 22 | 23 | 24 | 25 | 26 | 27 | 28 | 29 | 30 | 31 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Type = 8(IPv4, ICMP) 128(IPv6,ICMP6) | Code = 0 | Checksum | |||||||||||||||||||||||||||||
| Identifier | Sequence Number | ||||||||||||||||||||||||||||||
| Payload |
The Identifier and Sequence Number can be used by the client to match the reply with the request that caused the reply. In practice, most Linux systems use a unique identifier for every ping process, and sequence number is an increasing number within that process. Windows uses a fixed identifier, which varies between Windows versions, and a sequence number that is only reset at boot time.
Echo reply[edit]
The echo reply is an ICMP message generated in response to an echo request; it is mandatory for all hosts and must include the exact payload received in the request.
| 00 | 01 | 02 | 03 | 04 | 05 | 06 | 07 | 08 | 09 | 10 | 11 | 12 | 13 | 14 | 15 | 16 | 17 | 18 | 19 | 20 | 21 | 22 | 23 | 24 | 25 | 26 | 27 | 28 | 29 | 30 | 31 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Type = 0(IPv4,ICMP) 129(IPv6,ICMP6) | Code = 0 | Checksum | |||||||||||||||||||||||||||||
| Identifier | Sequence Number | ||||||||||||||||||||||||||||||
| Payload |
- The identifier and sequence number can be used by the client to associate each echo request with its reply.
Payload[edit]
The payload of the packet is generally filled with ASCII characters, as the output of the tcpdump utility shows in the last 32 bytes of the following example (after the eight-byte ICMP header starting with 0x0800):
16:24:47.966461 IP (tos 0x0, ttl 128, id 15103, offset 0, flags [none], proto: ICMP (1), length: 60) 192.168.146.22 > 192.168.144.5: ICMP echo request, id 1, seq 38, length 40 0x0000: 4500 003c 3aff 0000 8001 5c55 c0a8 9216 E..<:.....\U.... 0x0010: c0a8 9005 0800 4d35 0001 0026 6162 6364 ......M5...&abcd 0x0020: 6566 6768 696a 6b6c 6d6e 6f70 7172 7374 efghijklmnopqrst 0x0030: 7576 7761 6263 6465 6667 6869 uvwabcdefghi
The payload may include a timestamp indicating the time of transmission and a sequence number, which are not found in this example. This allows ping to compute the round trip time in a stateless manner without needing to record the time of transmission of each packet.
The payload may also include a magic packet for the Wake-on-LAN protocol, but the minimum payload, in that case, is longer than shown. The Echo Request typically does not receive any reply if the host was sleeping in hibernation state, but the host still wakes up from sleep state if its interface is configured to accept wakeup requests. If the host is already active and configured to allow replies to incoming ICMP Echo Request packets, the returned reply should include the same payload. This may be used to detect that the remote host was effectively woken up, by repeating a new request after some delay to allow the host to resume its network services. If the host was just sleeping in low power active state, a single request wakes up that host just enough to allow its Echo Reply service to reply instantly if that service was enabled. The host does not need to wake up all devices completely and may return to low-power mode after a short delay. Such configuration may be used to avoid a host to enter in hibernation state, with much longer wake-up delay, after some time passed in low power active mode.[citation needed]
Security loopholes[edit]
To conduct a denial-of-service attack, an attacker may send ping requests as fast as possible, possibly overwhelming the victim with ICMP echo requests. This technique is called a ping flood.[12]
Ping requests to multiple addresses, ping sweeps, may be used to obtain a list of all hosts on a network.
See also[edit]
- fping
- hping
- Keepalive
- nping
- PathPing
- Ping of death
- Ping-pong scheme
- Smurf attack
- Traceroute
References[edit]
- ^ a b c d Mike Muuss. «The Story of the PING Program». U.S. Army Research Laboratory. Archived from the original on 25 October 2019. Retrieved 8 September 2010.
My original impetus for writing PING for 4.2a BSD UNIX came from an offhand remark in July 1983 by Dr. Dave Mills … I named it after the sound that a sonar makes, inspired by the whole principle of echo-location … From my point of view PING is not an acronym standing for Packet InterNet Grouper, it’s a sonar analogy. However, I’ve heard second-hand that Dave Mills offered this expansion of the name, so perhaps we’re both right.
- ^ Salus, Peter (1994). A Quarter Century of UNIX. Addison-Wesley. ISBN 978-0-201-54777-1.
- ^ Mills, D.L. (December 1983). Internet Delay Experiments. IETF. doi:10.17487/RFC0889. RFC 889. Retrieved 26 November 2019.
- ^ «man page ping section 8». www.manpagez.com.
- ^ «ibiblio.org FreeDOS Package — ping (Networking)». www.ibiblio.org.
- ^ «GitHub — reactos/reactos: A free Windows-compatible Operating System». 8 August 2019 – via GitHub.
- ^ Braden, Robert T. (October 1989). Requirements for Internet Hosts — Communication Layers. p. 42. doi:10.17487/RFC1122. RFC 1122.
Every host MUST implement an ICMP Echo server function that receives Echo Requests and sends corresponding Echo Replies.
- ^ «ICMP: Internet Control Message Protocol». repo.hackerzvoice.net. 13 January 2000. Archived from the original on 4 August 2016. Retrieved 4 December 2014.
- ^ Postel, J. (September 1981). «RFC 792 — Internet Control Message Protocol». Tools.ietf.org. doi:10.17487/RFC0792. Retrieved 2 February 2014.
- ^ «RFC Sourcebook’s page on ICMP». Retrieved 20 December 2010.
- ^ Gupta, Mukesh; Conta, Alex (March 2006). Gupta, M (ed.). «RFC 4443 — Internet Control Message Protocol (ICMPv6) for the Internet Protocol Version 6 (IPv6) Specification». doi:10.17487/RFC4443. Retrieved 10 April 2020.
- ^ «What is a Ping Flood | ICMP Flood | DDoS Attack Glossary | Imperva». Learning Center. Retrieved 26 July 2021.
Further reading[edit]
- Dyson, Peter (1995). Mastering OS/2 Warp. Sybex. ISBN 978-0782116632.
- John Paul Mueller (2007). Windows Administration at the Command Line for Windows Vista, Windows 2003, Windows XP, and Windows 2000. John Wiley & Sons. ISBN 978-0470165799.
- McElhearn, Kirk (2006). The Mac OS X Command Line: Unix Under the Hood. John Wiley & Sons. ISBN 978-0470113851.
External links[edit]
ping(1M)– Solaris 11.4 Reference Manualping(8)– FreeBSD System Manager’s Manualping(8)– Linux Programmer’s Manual – Administration and Privileged Commands- ping | Microsoft Docs
PING (Packet Internet Groper) is a program used to test whether a particular network host is online by sending an ICMP (Internet control message protocol) echo request and waiting for a response. It is used for troubleshooting connectivity between network devices such as servers, routers, workstations and printers. It is one of the most commonly used tools used to troubleshoot network connectivity between devices.
You can ping a host from a command prompt simply by typing ping followed by the IP address. For example type ping 192.168.0.1 to see if the host with the 192.168.0.1 IP address is reachable. It also works with hostnames on the same network so if you have a server called WebServer you can type in ping WebServer to check for connectivity. You can also ping a website by typing ping www.microsoft.com to check its availability. For Windows computers you will need to allow ICMP packets through the firewall in order to be able to ping those computers.
To use the PING utility simply open a command prompt from your Start menu or type in cmd from your run command box or your search box.
When a PING is successful you get a reply back from the host showing its IP address and other information such as the time it took for the reply to go through.
When a ping response is not successful you can get a variety of error replies. Here are the main error messages and what they mean.
TTL Expired in Transit
The TTL value determines the maximum amount of time an IP packet may live in the network without reaching its destination. It is effectively a bound on the number of routers an IP packet may pass through before being discarded. This message indicates that the TTL expired in transit. Number of required hops exceeds TTL. Increase TTL by using the ping -i switch.
Destination Host Unreachable
The host that you are trying to ping is down or is not operating on the network. A local or remote route does not exist for destination host. Modify the local route table or notify the router administrator.
Request Timed Out
The ping command timed out because there was no reply from the host. No Echo Reply messages were received due to network traffic, failure of the ARP request packet filtering, or router error. Increase the wait time using the ping -w switch.
Unknown Host
The IP Address or the Host Name does not exist in the network or the destination host name cannot be resolved. Verify name and availability of DNS servers.
ping(8) BSD System Manager's Manual ping(8)
NAME
ping -- send ICMP ECHO_REQUEST packets to network hosts
SYNOPSIS
ping [-AaCDdfnoQqRrv] [-b boundif] [-c count] [-G sweepmaxsize]
[-g sweepminsize] [-h sweepincrsize] [-i wait] [-l preload]
[-M mask | time] [-m ttl] [-P policy] [-p pattern] [-S src_addr]
[-s packetsize] [-t timeout] [-W waittime] [-z tos] host
ping [-AaDdfLnoQqRrv] [-b boundif] [-c count] [-I iface] [-i wait]
[-l preload] [-M mask | time] [-m ttl] [-P policy] [-p pattern]
[-S src_addr] [-s packetsize] [-T ttl] [-t timeout] [-W waittime]
[-z tos] mcast-group
DESCRIPTION
The ping utility uses the ICMP protocol's mandatory ECHO_REQUEST datagram
to elicit an ICMP ECHO_RESPONSE from a host or gateway. ECHO_REQUEST
datagrams (``pings'') have an IP and ICMP header, followed by a ``struct
timeval'' and then an arbitrary number of ``pad'' bytes used to fill out
the packet. The options are as follows:
-A Audible. Output a bell (ASCII 0x07) character when no packet is
received before the next packet is transmitted. To cater for
round-trip times that are longer than the interval between trans-
missions, further missing packets cause a bell only if the maxi-
mum number of unreceived packets has increased.
-a Audible. Include a bell (ASCII 0x07) character in the output
when any packet is received. This option is ignored if other
format options are present.
-b boundif
Bind the socket to interface boundif for sending.
-C Prohibit the socket from using the cellular network interface.
-c count
Stop after sending (and receiving) count ECHO_RESPONSE packets.
If this option is not specified, ping will operate until inter-
rupted. If this option is specified in conjunction with ping
sweeps, each sweep will consist of count packets.
-D Set the Don't Fragment bit.
-d Set the SO_DEBUG option on the socket being used.
-f Flood ping. Outputs packets as fast as they come back or one
hundred times per second, whichever is more. For every
ECHO_REQUEST sent a period ``.'' is printed, while for every
ECHO_REPLY received a backspace is printed. This provides a
rapid display of how many packets are being dropped. Only the
super-user may use this option. This can be very hard on a net-
work and should be used with caution.
-G sweepmaxsize
Specify the maximum size of ICMP payload when sending sweeping
pings. This option is required for ping sweeps.
-g sweepminsize
Specify the size of ICMP payload to start with when sending
sweeping pings. The default value is 0.
-h sweepincrsize
Specify the number of bytes to increment the size of ICMP payload
after each sweep when sending sweeping pings. The default value
is 1.
-I iface
Source multicast packets with the given interface address. This
flag only applies if the ping destination is a multicast address.
-i wait
Wait wait seconds between sending each packet. The default is to
wait for one second between each packet. The wait time may be
fractional, but only the super-user may specify values less than
0.1 second. This option is incompatible with the -f option.
-L Suppress loopback of multicast packets. This flag only applies
if the ping destination is a multicast address.
-l preload
If preload is specified, ping sends that many packets as fast as
possible before falling into its normal mode of behavior. Only
the super-user may use this option.
-M mask | time
Use ICMP_MASKREQ or ICMP_TSTAMP instead of ICMP_ECHO. For mask,
print the netmask of the remote machine. Set the
net.inet.icmp.maskrepl MIB variable to enable ICMP_MASKREPLY.
For time, print the origination, reception and transmission time-
stamps.
-m ttl Set the IP Time To Live for outgoing packets. If not specified,
the kernel uses the value of the net.inet.ip.ttl MIB variable.
-n Numeric output only. No attempt will be made to lookup symbolic
names for host addresses.
-o Exit successfully after receiving one reply packet.
-P policy
policy specifies IPsec policy for the ping session. For details
please refer to ipsec(4) and ipsec_set_policy(3).
-p pattern
You may specify up to 16 ``pad'' bytes to fill out the packet you
send. This is useful for diagnosing data-dependent problems in a
network. For example, ``-p ff'' will cause the sent packet to be
filled with all ones.
-Q Somewhat quiet output. Don't display ICMP error messages that
are in response to our query messages. Originally, the -v flag
was required to display such errors, but -v displays all ICMP
error messages. On a busy machine, this output can be overbear-
ing. Without the -Q flag, ping prints out any ICMP error mes-
sages caused by its own ECHO_REQUEST messages.
-q Quiet output. Nothing is displayed except the summary lines at
startup time and when finished.
-R Record route. Includes the RECORD_ROUTE option in the
ECHO_REQUEST packet and displays the route buffer on returned
packets. Note that the IP header is only large enough for nine
such routes; the traceroute(8) command is usually better at
determining the route packets take to a particular destination.
If more routes come back than should, such as due to an illegal
spoofed packet, ping will print the route list and then truncate
it at the correct spot. Many hosts ignore or discard the
RECORD_ROUTE option.
-r Bypass the normal routing tables and send directly to a host on
an attached network. If the host is not on a directly-attached
network, an error is returned. This option can be used to ping a
local host through an interface that has no route through it
(e.g., after the interface was dropped by routed(8)).
-S src_addr
Use the following IP address as the source address in outgoing
packets. On hosts with more than one IP address, this option can
be used to force the source address to be something other than
the IP address of the interface the probe packet is sent on. If
the IP address is not one of this machine's interface addresses,
an error is returned and nothing is sent.
-s packetsize
Specify the number of data bytes to be sent. The default is 56,
which translates into 64 ICMP data bytes when combined with the 8
bytes of ICMP header data. This option cannot be used with ping
sweeps.
-T ttl Set the IP Time To Live for multicasted packets. This flag only
applies if the ping destination is a multicast address.
-t timeout
Specify a timeout, in seconds, before ping exits regardless of
how many packets have been received.
-v Verbose output. ICMP packets other than ECHO_RESPONSE that are
received are listed.
-W waittime
Time in milliseconds to wait for a reply for each packet sent.
If a reply arrives later, the packet is not printed as replied,
but considered as replied when calculating statistics.
-z tos Use the specified type of service.
When using ping for fault isolation, it should first be run on the local
host, to verify that the local network interface is up and running.
Then, hosts and gateways further and further away should be ``pinged''.
Round-trip times and packet loss statistics are computed. If duplicate
packets are received, they are not included in the packet loss calcula-
tion, although the round trip time of these packets is used in calculat-
ing the round-trip time statistics. When the specified number of packets
have been sent (and received) or if the program is terminated with a
SIGINT, a brief summary is displayed, showing the number of packets sent
and received, and the minimum, mean, maximum, and standard deviation of
the round-trip times.
If ping receives a SIGINFO (see the status argument for stty(1)) signal,
the current number of packets sent and received, and the minimum, mean,
and maximum of the round-trip times will be written to the standard error
output.
This program is intended for use in network testing, measurement and man-
agement. Because of the load it can impose on the network, it is unwise
to use ping during normal operations or from automated scripts.
ICMP PACKET DETAILS
An IP header without options is 20 bytes. An ICMP ECHO_REQUEST packet
contains an additional 8 bytes worth of ICMP header followed by an arbi-
trary amount of data. When a packetsize is given, this indicated the
size of this extra piece of data (the default is 56). Thus the amount of
data received inside of an IP packet of type ICMP ECHO_REPLY will always
be 8 bytes more than the requested data space (the ICMP header).
If the data space is at least eight bytes large, ping uses the first
eight bytes of this space to include a timestamp which it uses in the
computation of round trip times. If less than eight bytes of pad are
specified, no round trip times are given.
DUPLICATE AND DAMAGED PACKETS
The ping utility will report duplicate and damaged packets. Duplicate
packets should never occur when pinging a unicast address, and seem to be
caused by inappropriate link-level retransmissions. Duplicates may occur
in many situations and are rarely (if ever) a good sign, although the
presence of low levels of duplicates may not always be cause for alarm.
Duplicates are expected when pinging a broadcast or multicast address,
since they are not really duplicates but replies from different hosts to
the same request.
Damaged packets are obviously serious cause for alarm and often indicate
broken hardware somewhere in the ping packet's path (in the network or in
the hosts).
TRYING DIFFERENT DATA PATTERNS
The (inter)network layer should never treat packets differently depending
on the data contained in the data portion. Unfortunately, data-dependent
problems have been known to sneak into networks and remain undetected for
long periods of time. In many cases the particular pattern that will
have problems is something that does not have sufficient ``transitions'',
such as all ones or all zeros, or a pattern right at the edge, such as
almost all zeros. It is not necessarily enough to specify a data pattern
of all zeros (for example) on the command line because the pattern that
is of interest is at the data link level, and the relationship between
what you type and what the controllers transmit can be complicated.
This means that if you have a data-dependent problem you will probably
have to do a lot of testing to find it. If you are lucky, you may manage
to find a file that either cannot be sent across your network or that
takes much longer to transfer than other similar length files. You can
then examine this file for repeated patterns that you can test using the
-p option of ping.
TTL DETAILS
The TTL value of an IP packet represents the maximum number of IP routers
that the packet can go through before being thrown away. In current
practice you can expect each router in the Internet to decrement the TTL
field by exactly one.
The TCP/IP specification recommends setting the TTL field for IP packets
to 64, but many systems use smaller values (4.3BSD uses 30, 4.2BSD used
15).
The maximum possible value of this field is 255, and most UNIX systems
set the TTL field of ICMP ECHO_REQUEST packets to 255. This is why you
will find you can ``ping'' some hosts, but not reach them with telnet(1)
or ftp(1).
In normal operation ping prints the ttl value from the packet it
receives. When a remote system receives a ping packet, it can do one of
three things with the TTL field in its response:
o Not change it; this is what BSD systems did before the 4.3BSD-Tahoe
release. In this case the TTL value in the received packet will be
255 minus the number of routers in the round-trip path.
o Set it to 255; this is what current BSD systems do. In this case the
TTL value in the received packet will be 255 minus the number of
routers in the path from the remote system to the pinging host.
o Set it to some other value. Some machines use the same value for
ICMP packets that they use for TCP packets, for example either 30 or
60. Others may use completely wild values.
EXIT STATUS
The ping utility exits with one of the following values:
0 At least one response was heard from the specified host.
2 The transmission was successful but no responses were received.
any other value
An error occurred. These values are defined in <sysexits.h>.
SEE ALSO
netstat(1), ifconfig(8), routed(8), traceroute(8), ping6(8)
HISTORY
The ping utility appeared in 4.3BSD.
AUTHORS
The original ping utility was written by Mike Muuss while at the US Army
Ballistics Research Laboratory.
BUGS
Many Hosts and Gateways ignore the RECORD_ROUTE option.
The maximum IP header length is too small for options like RECORD_ROUTE
to be completely useful. There's not much that can be done about this,
however.
Flood pinging is not recommended in general, and flood pinging the broad-
cast address should only be done under very controlled conditions.
The -v option is not worth much on busy hosts.
BSD March 29, 2013 BSD
Mac OS X 10.9 — Generated Fri Oct 18 06:31:53 CDT 2013