Check out this guide to know about this credential validation event
by Vladimir Popescu
Being an artist his entire life while also playing handball at a professional level, Vladimir has also developed a passion for all things computer-related. With an innate fascination… read more
Updated on
- Every login attempt on a domain controller is recorded, and the DC logs the event ID 4776 for every successful or unsuccessful attempt.
- This guide will discuss this event ID and how to get rid of the error code if authentication fails.
XINSTALL BY CLICKING THE DOWNLOAD FILE
To fix Windows PC system issues, you will need a dedicated tool
SPONSORED
Fortect is a tool that does not simply clean up your PC, but has a repository with several millions of Windows System files stored in their initial version. When your PC encounters a problem, Fortect will fix it for you, by replacing bad files with fresh versions. To fix your current PC issue, here are the steps you need to take:
- Download Fortect and install it on your PC.
- Start the tool’s scanning process to look for corrupt files that are the source of your problem
- Right-click on Start Repair so the tool could start the fixing algorythm
- Fortect has been downloaded by 0 readers this month, rated 4.4 on TrustPilot
Event ID 4776: the computer attempted to validate the credentials for an account gives you essential information which helps you identify the sources of the login attempts.
Here we will discuss what Event ID 4776 means and how to fix error code 0xc0000064. Let’s get started!
What does the Event ID 4776 computer attempted to validate credentials mean?
Event ID 4776 is a security-related event. It is generated every time a computer tries to validate credentials using NTLM authentication. It occurs only on the computer with authority for the provided credentials.
The event contains detailed information about the user account used for authentication, the destination and the source of the authentication request, along with the status of the attempt.
If Windows Event ID 4776 is successful, there is no need to worry. However, seeing multiple failed instances might indicate the relay, cracking attacks, and reverse brute force attacks. Therefore keeping an eye on this event ID is important.
What causes Event ID 4776 error code 0xc0000064?
A few reasons for the error to occur are mentioned below:
- User name doesn’t exist – This error comes up when the username you typed does not exist or is incorrect.
- Third-party programs cache – If any third-party programs cache the user’s wrong password, this error code may come up.
- Incorrect status by Net Logon service – When the Netlogon.dll manages the returned status incorrectly, the issue occurs.
- Kerberos fails while authenticating RDP – If you connect to the network using a Remote desk protocol, it uses Kerberos to authenticate. But, if it fails, then it has to use NTLM. Hence the error
What can I do to fix Event ID 4776 error code 0xc0000064?
1. Identifying the Logon account and the source workstation when blank or unknown
1.1 Enable Netlogon to find the source
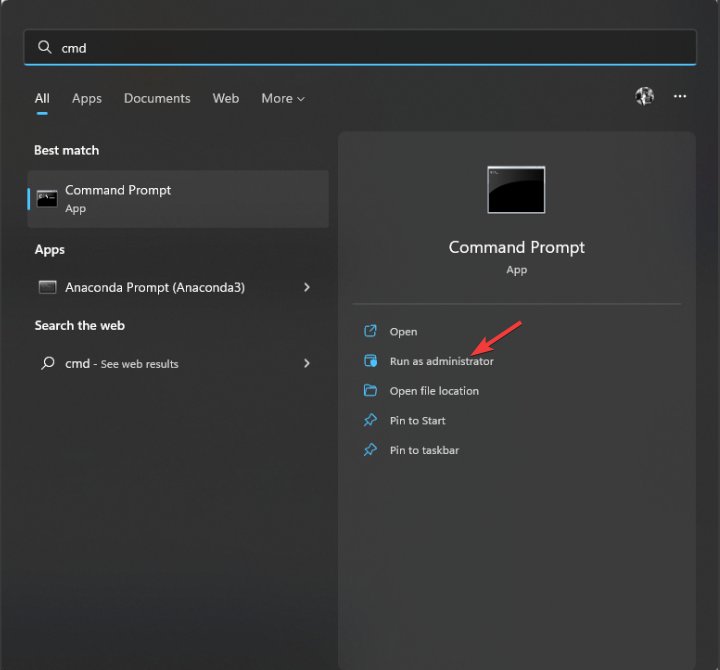
- Press the Windows key, type CMD and click Run as administrator.
- Type the following command and press Enter:
nltest /dbflag:0x2080ffff - Close the CMD window.
- To access your Netlogon files, press Windows + R to open the Run window.
- Type the following command and press Enter:
%SYSTEMROOT%\debug\netlogon.log - Now check the username and other details to identify the login attempt.
1.2 Use a Packet Analyzer
Tools like Wireshark can be used to keep an eye on your network on a microscopic level. It can capture the traffic simultaneously when someone tries to log in and helps you find the source. The tool can identify IP addresses so that you can easily locate the logons.
2. Identifying the Logon account and the source workstation if there is a remote client
2.1 Use firewall
You can use your firewall to protect your server or computer from unknown login attempts. Follow the whitelists approach (block all, allow some) instead of denylists (allow all, block some). This will ensure that only authorized attempts are initiated outside the network.
2.2 Use VPN
Using a reliable VPN can also help you safe-keep your network. It will let remote users connect to the local server and then authenticate normally.
A great VPN option that we recommend is Private Internet Access (PIA) because it is fast and highly customizable and has unbreakable security thanks to its numerous privacy features that will keep your activity always safe.

Private Internet Access
Keep your data protected and secure all the time with the most privacy-focused VPN service.
Well, that’s all from our side on how to fix the event id 4776 error code 0xc0000064, and we hope that our solutions helped you solve this issue.
If you still have any issues, feel free to drop a comment below. We’re eager to hear from you.
Despite what this event says, the computer is not necessarily a domain controller; member servers and workstations also log this event for logon attempts with local SAM accounts.
When a domain controller successfully authenticates a user via NTLM (instead of Kerberos), the DC logs this event. This specifies which user account who logged on (Account Name) as well as the client computer’s name from which the user initiated the logon in the Workstation field.
For Kerberos authentication see event 4768, 4769 and 4771.
This event is also logged on member servers and workstations when someone attempts to logon with a local account.
Authentication Package: Always «MICROSOFT_AUTHENTICATION_PACKAGE_V1_0»
Logon Account: name of the account
Source Workstation: computer name where logon attempt originated
Description Fields in
4776
Error Code:
| C0000064 | user name does not exist |
| C000006A | user name is correct but the password is wrong |
| C0000234 | user is currently locked out |
| C0000072 | account is currently disabled |
| C000006F | user tried to logon outside his day of week or time of day restrictions |
| C0000070 | workstation restriction |
| C0000193 | account expiration |
| C0000071 | expired password |
| C0000224 | user is required to change password at next logon |
| C0000225 | evidently a bug in Windows and not a risk |
Stay up-to-date on the Latest in Cybersecurity
Sign up for the Ultimate IT Security newsletter
to hear about the latest webinars, patches, CVEs, attacks, and more.
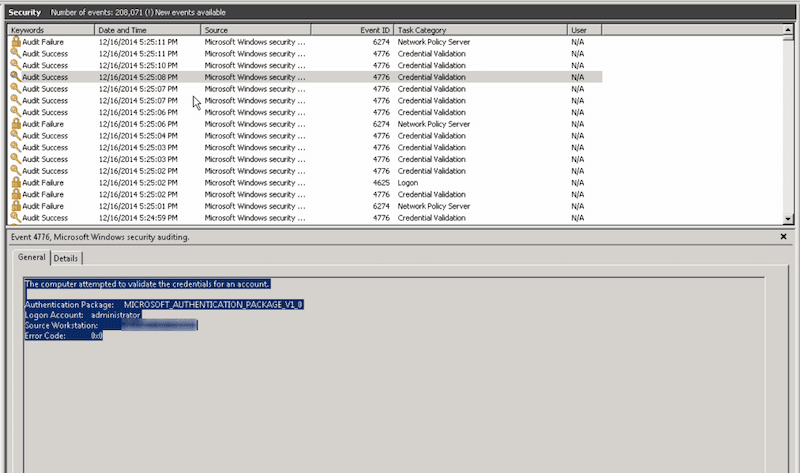
Your Domain Controller’s Windows Event Viewer might be logging tons of security events with strange usernames, misspelled names, attempts with expired or lockout accounts, or strange logon attempts outside business hours— all labeled with the Event ID 4776.
The “Event ID 4776: The computer attempted to validate the credentials for an account” gives you valuable information to help identify the sources of these attempts. Knowing how to troubleshoot and monitor these events can be detrimental to identifying potential brute force dictionary attacks or mal-intentional account uses.
In this post, we’ll go through the technical explanation of what is the Windows Event ID 4776, the details on how to read it, how to troubleshoot or solve the events, and how to monitor and audit using specific software.
Introduction: What is Windows Event ID 4776
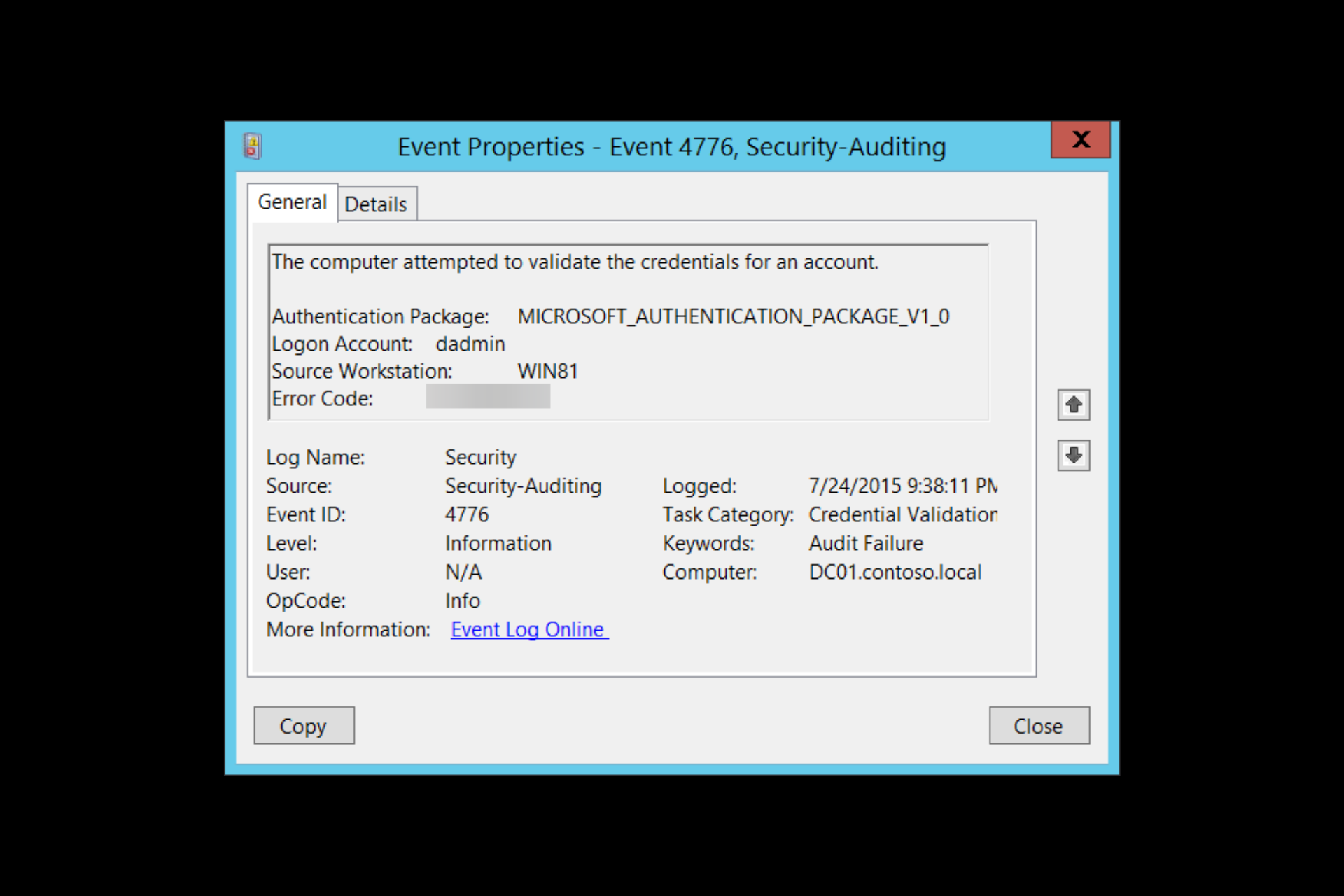
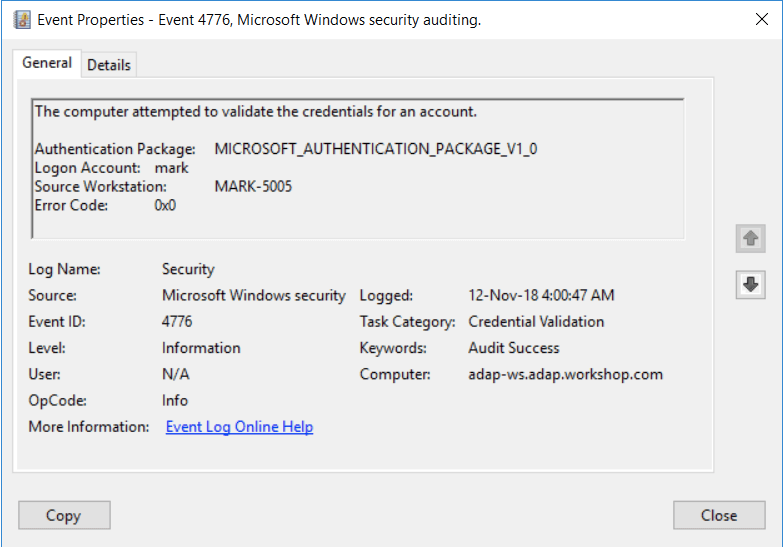
“Event ID 4776: The computer attempted to validate the credentials for an account”
You might have come across the log Event ID 4776 while looking at your event logs in a Domain Controller (DC). This event tells you that this specific DC (but also servers and workstations) was used as a logon server to validate credentials. The event ID 4776 is logged every time the DC tries to validate the credentials of an account using NTLM (NT LAN Manager).
Event ID 4776 is a credential validation event that can either represent success or failure. It is displayed in Windows 2008 R2 and 7, Windows 2012 R2 and 8.1, Windows 2016 and 10, and Windows Server 2019 and 2022.
Note: The Event ID 4776 is not only logged for domain controllers attempting to validate credentials but also for other member Windows servers or workstations used for logon attempts with a local SAM account. This is because the NTLM is the default authentication mechanism for local logon.
Let’s go over the details of the Windows Event ID 4776
The domain controller attempted to validate the credentials for an account.Authentication Package: Always "MICROSOFT_AUTHENTICATION_PACKAGE_V1_0"Logon Account: name of the accountSource Workstation: computer name where logon attempt originatedError Code: 0x0
Every logon attempt on a domain controller is recorded on the DC. The DC logs the event ID 4776 when it validates the credentials and either succeeds or fails to authenticate a user via NTLM (not Kerberos). In addition, if there was a logon attempt via a local SAM account, where a server or a workstation validates credentials, then the event ID 4776 is logged on the local machine.
The event (as described in the details above) specifies:
- The authentication package specifies the package, which is always “MICROSOFT_AUTHENTICATION_PACKAGE_V1_0”.
- The Logon Account is the account name of the user or computer that attempted to log on. A logon account can also be a well-known security principle.
- The Source Workstation is the client’s computer name (source workstation) used to initiate the logon.
- Error Code The Error Code describes whether the authentication succeeded or failed (and the reasons). If you succeed, you’ll see an 0x0 error code, but if it fails, you’d see something other than 0x0—more on error codes in the next section.
Details on Windows Event ID 4776 Error Code
- Error Code equals (0x0) If this field is 0x0, the credentials were successfully validated as “Authentication Success – Event ID 4776 (S)”. No errors.
- Error Code not equal to (0x0) If the field is not equal to 0x0, it means that the credentials were not successfully validated (failed) “Authentication Failure – Event ID 4776 (F)”. Below is a table with more descriptions of the error code- not equal to 0x0.
| Error Code | Description |
|---|---|
| 0xC0000064 | Incorrect username. The username does not exist. |
| 0xC000006A | The username is correct, but not the password. |
| 0xC000006D | A generic logon failure. NTLM authentication-level mismatch. |
| 0xC000006F | Unauthorized account logon. Outside an authorized day or hour. |
| 0xC0000070 | Unauthorized account logon from a restricted workstation. |
| 0xC0000071 | The user tried to log on with an expired password. |
| 0xC0000072 | Unauthorized account logon due to a disabled account. |
| 0xC0000193 | Unauthorized account logon due to an expired account. |
| 0xC0000224 | A flag that the user needs to change the password at the next logon. |
| 0xC0000225 | Known to be a Windows bug. Not a risk. |
| 0xC0000234 | Attempted logon with a locked account. |
| 0xC0000371 | The local account storage does not contain information about the specific account. |
Troubleshooting the Windows Event ID 4776
If the Windows Event ID 4776 (S) is successful, you don’t have a problem. However, the problem starts when you get a few to hundreds or thousands of Windows Event ID 4776 (F) failed attempts. Although this would start to look like a problem, let us not draw quick conclusions just yet.
Although the evidence might indicate that your workstation is being a target of a brute force dictionary or rainbow attack, it could also indicate a relatively inoffensive system (such as a printer) is trying to authenticate with expired credentials.
How to solve the Windows Event ID 4776 failed attempts
- Start by identifying the logon account and the source workstation As you learned from the previous section, Event ID 4776 shows you the account name and the source workstation. Remember authentication happens via NTLM, which can help you identify the user or workstation quickly. But still, the source workstation could be attempting to log from outside, carrying a blank name, and also, the account could be random (made up). So, you’ll have to dig deeper.
- If this source workstation is blank or unknown To find out the source of an unknown workstation, you’ll need to involve other tools.
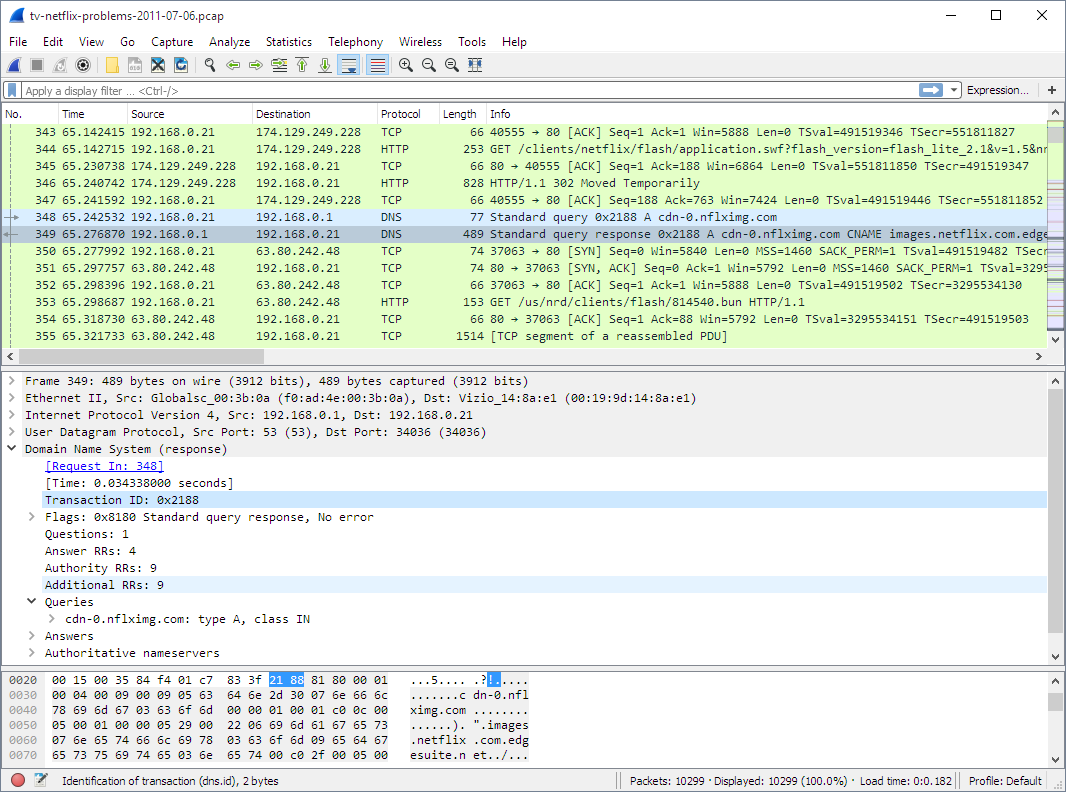
- Packet Sniffer Use third-party tools such as Wireshark deployed on the DC to capture the traffic at the same time as these events. You’ll need to use capture and display filters on Wireshark to be able to find exactly the source of these events. And also be able to correlate the exact time in Windows Event Viewer with Wireshark when this event happens. In addition, with Wireshark, you can quickly identify IP addresses to start drawing a better picture of where these logons are coming from.
- Network debugger Another handy third-party tool is a network debugger. Enable the NetLogon debugging utility on your DC. This tool will generate a log file with all these authentication requests. You can review this log file and find out where they originate.
- DCDiag The DCDiag is a Domain Controller Health Check tool that helps you with troubleshooting. Aside from running different health checks on the DC, the DCdiag also logs additional details like errors, warnings, or informational messages. Use the DCDiag with the verbose output (/v) to expand the output size.
- If a remote client is trying to authenticate using RDP (port 3389) You or the sys admin might have the port 3389 (RDP) open for users that connect remotely to machines inside the domain. When using the RDP, bear in mind that RDP prefers Kerberos to authenticate, but if it fails, it will fall back to using NTLM instead. Thus, this could be a reason you received the Event ID 4776 with an unknown source workstation. Below are a few solutions you can try:
- Use your firewall One of the most simple solutions is to use the firewall. Instead of using the denylists (allow all block some), use the zero-trust (or whitelists) approach (block all allow some) to only allow authorized attempts originating outside the network.
- Use a VPN A more advanced and efficient solution is to set up a VPN that allows remote users to connect to the local server and then authenticate normally.
Why should you monitor the Windows Event ID 4776
Always monitor the Windows Event ID 4776 to discover and list all the NTLM authentication attempts in your domain. Look for the events ID 4776 that were initiated by the accounts that are unauthorized or shouldn’t be using NTLM in the first place. Always remember that NTLM should only be used for local logon attempts (this is why you shouldn’t use RDP, but a VPN instead).
The reasons to monitor Event ID 4776:
- Identify relay and cracking attacks The NTLM authentication mechanism is vulnerable to relay attacks (fraudulent interception of information). First and most importantly, NTLM does not support modern cryptographic algorithms like SHA-256 or AES-256. This lack of encryption also makes it vulnerable to offline cracking attacks.
- Find reverse brute force, brute force, or enumeration attacks Monitor the Windows Event ID 4776 and keep track of multiple logon attempts within a short period, and with particular qualities like using multiple incorrect usernames. This type of behavior is strongly related to reverse brute force and enumeration attacks. In a similar case, you can keep track of this event and look for multiple logon attempts with incorrect (or misspelled password) within short periods. This behavior is related to brute-force attacks.
- Find potential malicious intent Keeping track of the Windows Event ID 4776 can help you find logon attempts outside authorized business hours or from unauthorized workstations. If these logon attempts are coming from a high-value account, then it might relate to malicious intent. In addition, logon attempts from locked expired, or disabled accounts could indicate mal-intentional use of resources.
Although it could be optimal to use more secure protocols such as the Kerberos (v5) and avoid these NTLM vulnerabilities, disabling NTLM authentication requests will ultimately hurt productivity and usability. There are still many NTLM authentication requests that need to be verified.
Kerberos is now the preferred authentication method used in Active Directory environments. As a good practice, before using more secure protocols like Kerberos and forcing Windows to limit NTLM traffic, it is first recommended to audit all security logs and events related to NTLM authentication. For these audits, there are a variety of tools you could use.
How to Monitor the Windows Event ID 4776
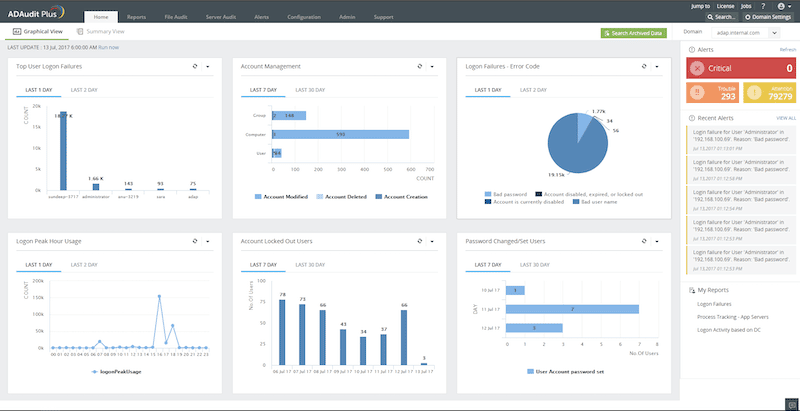
The Windows Event ID 4776 is a type of event log that should be monitored on an ongoing daily basis. You could use different practices and tools. We recommend knowing first how to properly use the Windows Event Viewer (along with its built-in capabilities) and then expanding to more robust audit tools like the ADAudit Plus.
1. Windows Event Viewer
Windows Event Viewer (From Windows Vista 7, Server 2008, and newer versions) allows you to introduce automation by associating a task to a specific event or log. When an event such as the Event ID 4776 is generated, you can associate it with a specific automated task. For instance, you can link it to an email, “Send me an email when Windows Event ID 4776 is generated”.
Windows Event Viewer does have some limitations, especially when it comes to its alerting and reporting engine. For instance, the email won’t give you granular information, such as the type of errors (i.e., attempts from unauthorized workstations, locked accounts, misspelled usernames, or outside business hours). In addition, Event Viewer also does not provide granular filtering capabilities to help you find what you are looking for.
2. ManageEngine ADAudit Plus
ManageEngine ADAudit Plus is an UBA-driven audit solution for full visibility into Active Directory environments. It provides real-time monitoring, behavior analytics, and reporting. This solution is perfect for monitoring the Windows Event ID 4776, as well as other events like ID 4724, 4726, 4769, 4768, 4740, and more.
Key Features
- Apply granular filters to look for specific threats.
- Get notified via email and SMS.
- Detect abnormal behaviors with UEBA (User and Entity Behavior Analytics).
- Out-of-the-box compliance reports for SOX, HIPAA, PCI, FISMA, GLBA, and the GDPR.
ADAudit Plus is a tool designed to monitor logons, analyze lockouts, and spot changes made to users, groups, OUs, or any Active Directory object. In addition, with the ADAudit Plus, you can also monitor local logons (NTLM), including changes made to users, groups, and security policies on Windows Servers. You can also monitor and audit various aspects within Windows workstations, including active time, changes to local users, security policies, USB activity, and more.
Download a 30-day ADAudit Plus trial, and start monitoring the Windows Event ID 4776, today.
Summary
The Windows Event ID 4776 (Audit Failure) – “The domain controller attempted to validate the credentials for an account” is an important event log that alerts you when a failed authentication event happens through the NTLM. This event log gives you valuable information, such as the workstation name, account, and the system or server used to pass the login request.
A way to solve this type of vulnerability is to audit NTLM authentication on this domain, monitor it, and, if possible, restrict it.
To audit and monitor this event successfully, learn how to use the Windows Event Viewer properly and then expand to more robust audit tools like the ADAudit Plus.
Windows Event ID 4776 FAQs
What does Event ID 4776 indicate?
Event ID 4776 indicates an attempted logon to a computer or network resource using a specific user account. This event is generated on the computer where the logon attempt was made.
What information is included in an Event ID 4776 log?
An Event ID 4776 log includes information such as the source network address, the logon type, the authentication package used, and the status of the logon attempt.
How can Event ID 4776 be used for security purposes?
Event ID 4776 can be used for security purposes by monitoring for unusual or unauthorized logon attempts. This can help detect potential security incidents or unauthorized access to sensitive information.
Can Event ID 4776 be used to track logon activity on a network?
Yes, Event ID 4776 can be used to track logon activity on a network by collecting and analyzing the event logs from all relevant computers.
How can I view Event ID 4776 logs in Windows?
To view Event ID 4776 logs in Windows, you can use the Event Viewer tool and filter the security log for Event ID 4776.
Can Event ID 4776 be disabled?
No, Event ID 4776 cannot be disabled. It is an important security event that is generated by the operating system and is critical for monitoring and auditing logon activity on a computer or network.
User501181060 posted
Hi Guys,
We have been getting 4776 Events (status with 0xc0000064)on our IIS server stating that the account does not exists for multiple users.
But AD accounts is actually exists and not issues with AD accounts as well.
In Same server I can see Successful logon events for same users, don’t understand why its happening
Please help me on this…
Successful logon event 4624 for same user account on same server
An account was successfully logged on.
Subject:
Security ID:
NULL SID
Account Name: —
Account Domain: —
Logon ID:
0x0
Logon Type:
3
New Logon:
Security ID:
xxxxxxxxxxx
Account Name: xxxxxxxxxxx
Account Domain: xxxxxxxxxxx
Logon ID:
0x2d7af6a6e
Logon GUID:
{00000000-0000-0000-0000-000000000000}
Process Information:
Process ID:
0x0
Process Name: —
Network Information:
Workstation Name: xxxxxxxxxxxx
Source Network Address: xx.xx.xx.xx
Source Port:
58480
Detailed Authentication Information:
Logon Process: NtLmSsp
Authentication Package: NTLM
Transited Services: —
Package Name (NTLM only): NTLM V2
Key Length:
0
This event is generated when a logon session is created. It is generated on the computer that was accessed.
The subject fields indicate the account on the local system which requested the logon. This is most commonly a service such as the Server service, or a local process such as Winlogon.exe or Services.exe.
The logon type field indicates the kind of logon that occurred. The most common types are 2 (interactive) and 3 (network).
The New Logon fields indicate the account for whom the new logon was created, i.e. the account that was logged on.
The network fields indicate where a remote logon request originated. Workstation name is not always available and may be left blank in some cases.
The authentication information fields provide detailed information about this specific logon request.
— Logon GUID is a unique identifier that can be used to correlate this event with a KDC event.
— Transited services indicate which intermediate services have participated in this logon request.
— Package name indicates which sub-protocol was used among the NTLM protocols.
— Key length indicates the length of the generated session key. This will be 0 if no session key was requested.
4776 Event screenshot
Your Domain Controller’s Windows Event Viewer might be logging tons of security events with strange usernames, misspelled names, attempts with expired or lockout accounts, or strange logon attempts outside business hours— all labeled with the Event ID 4776.
The “Event ID 4776: The computer attempted to validate the credentials for an account” gives you valuable information to help identify the sources of these attempts. Knowing how to troubleshoot and monitor these events can be detrimental to identifying potential brute force dictionary attacks or mal-intentional account uses.
In this post, we’ll go through the technical explanation of what is the Windows Event ID 4776, the details on how to read it, how to troubleshoot or solve the events, and how to monitor and audit using specific software.
Introduction: What is Windows Event ID 4776
“Event ID 4776: The computer attempted to validate the credentials for an account”
You might have come across the log Event ID 4776 while looking at your event logs in a Domain Controller (DC). This event tells you that this specific DC (but also servers and workstations) was used as a logon server to validate credentials. The event ID 4776 is logged every time the DC tries to validate the credentials of an account using NTLM (NT LAN Manager).
Event ID 4776 is a credential validation event that can either represent success or failure. It is displayed in Windows 2008 R2 and 7, Windows 2012 R2 and 8.1, Windows 2016 and 10, and Windows Server 2019 and 2022.
Note: The Event ID 4776 is not only logged for domain controllers attempting to validate credentials but also for other member Windows servers or workstations used for logon attempts with a local SAM account. This is because the NTLM is the default authentication mechanism for local logon.
Let’s go over the details of the Windows Event ID 4776
The domain controller attempted to validate the credentials for an account.Authentication Package: Always "MICROSOFT_AUTHENTICATION_PACKAGE_V1_0"Logon Account: name of the accountSource Workstation: computer name where logon attempt originatedError Code: 0x0
Every logon attempt on a domain controller is recorded on the DC. The DC logs the event ID 4776 when it validates the credentials and either succeeds or fails to authenticate a user via NTLM (not Kerberos). In addition, if there was a logon attempt via a local SAM account, where a server or a workstation validates credentials, then the event ID 4776 is logged on the local machine.
The event (as described in the details above) specifies:
- The authentication package specifies the package, which is always “MICROSOFT_AUTHENTICATION_PACKAGE_V1_0”.
- The Logon Account is the account name of the user or computer that attempted to log on. A logon account can also be a well-known security principle.
- The Source Workstation is the client’s computer name (source workstation) used to initiate the logon.
- Error Code The Error Code describes whether the authentication succeeded or failed (and the reasons). If you succeed, you’ll see an 0x0 error code, but if it fails, you’d see something other than 0x0—more on error codes in the next section.
Details on Windows Event ID 4776 Error Code
- Error Code equals (0x0) If this field is 0x0, the credentials were successfully validated as “Authentication Success – Event ID 4776 (S)”. No errors.
- Error Code not equal to (0x0) If the field is not equal to 0x0, it means that the credentials were not successfully validated (failed) “Authentication Failure – Event ID 4776 (F)”. Below is a table with more descriptions of the error code- not equal to 0x0.
| Error Code | Description |
|---|---|
| 0xC0000064 | Incorrect username. The username does not exist. |
| 0xC000006A | The username is correct, but not the password. |
| 0xC000006D | A generic logon failure. NTLM authentication-level mismatch. |
| 0xC000006F | Unauthorized account logon. Outside an authorized day or hour. |
| 0xC0000070 | Unauthorized account logon from a restricted workstation. |
| 0xC0000071 | The user tried to log on with an expired password. |
| 0xC0000072 | Unauthorized account logon due to a disabled account. |
| 0xC0000193 | Unauthorized account logon due to an expired account. |
| 0xC0000224 | A flag that the user needs to change the password at the next logon. |
| 0xC0000225 | Known to be a Windows bug. Not a risk. |
| 0xC0000234 | Attempted logon with a locked account. |
| 0xC0000371 | The local account storage does not contain information about the specific account. |
Troubleshooting the Windows Event ID 4776
If the Windows Event ID 4776 (S) is successful, you don’t have a problem. However, the problem starts when you get a few to hundreds or thousands of Windows Event ID 4776 (F) failed attempts. Although this would start to look like a problem, let us not draw quick conclusions just yet.
Although the evidence might indicate that your workstation is being a target of a brute force dictionary or rainbow attack, it could also indicate a relatively inoffensive system (such as a printer) is trying to authenticate with expired credentials.
How to solve the Windows Event ID 4776 failed attempts
- Start by identifying the logon account and the source workstation As you learned from the previous section, Event ID 4776 shows you the account name and the source workstation. Remember authentication happens via NTLM, which can help you identify the user or workstation quickly. But still, the source workstation could be attempting to log from outside, carrying a blank name, and also, the account could be random (made up). So, you’ll have to dig deeper.
- If this source workstation is blank or unknown To find out the source of an unknown workstation, you’ll need to involve other tools.
- Packet Sniffer Use third-party tools such as Wireshark deployed on the DC to capture the traffic at the same time as these events. You’ll need to use capture and display filters on Wireshark to be able to find exactly the source of these events. And also be able to correlate the exact time in Windows Event Viewer with Wireshark when this event happens. In addition, with Wireshark, you can quickly identify IP addresses to start drawing a better picture of where these logons are coming from.
- Network debugger Another handy third-party tool is a network debugger. Enable the NetLogon debugging utility on your DC. This tool will generate a log file with all these authentication requests. You can review this log file and find out where they originate.
- DCDiag The DCDiag is a Domain Controller Health Check tool that helps you with troubleshooting. Aside from running different health checks on the DC, the DCdiag also logs additional details like errors, warnings, or informational messages. Use the DCDiag with the verbose output (/v) to expand the output size.
- If a remote client is trying to authenticate using RDP (port 3389) You or the sys admin might have the port 3389 (RDP) open for users that connect remotely to machines inside the domain. When using the RDP, bear in mind that RDP prefers Kerberos to authenticate, but if it fails, it will fall back to using NTLM instead. Thus, this could be a reason you received the Event ID 4776 with an unknown source workstation. Below are a few solutions you can try:
- Use your firewall One of the most simple solutions is to use the firewall. Instead of using the denylists (allow all block some), use the zero-trust (or whitelists) approach (block all allow some) to only allow authorized attempts originating outside the network.
- Use a VPN A more advanced and efficient solution is to set up a VPN that allows remote users to connect to the local server and then authenticate normally.
Why should you monitor the Windows Event ID 4776
Always monitor the Windows Event ID 4776 to discover and list all the NTLM authentication attempts in your domain. Look for the events ID 4776 that were initiated by the accounts that are unauthorized or shouldn’t be using NTLM in the first place. Always remember that NTLM should only be used for local logon attempts (this is why you shouldn’t use RDP, but a VPN instead).
The reasons to monitor Event ID 4776:
- Identify relay and cracking attacks The NTLM authentication mechanism is vulnerable to relay attacks (fraudulent interception of information). First and most importantly, NTLM does not support modern cryptographic algorithms like SHA-256 or AES-256. This lack of encryption also makes it vulnerable to offline cracking attacks.
- Find reverse brute force, brute force, or enumeration attacks Monitor the Windows Event ID 4776 and keep track of multiple logon attempts within a short period, and with particular qualities like using multiple incorrect usernames. This type of behavior is strongly related to reverse brute force and enumeration attacks. In a similar case, you can keep track of this event and look for multiple logon attempts with incorrect (or misspelled password) within short periods. This behavior is related to brute-force attacks.
- Find potential malicious intent Keeping track of the Windows Event ID 4776 can help you find logon attempts outside authorized business hours or from unauthorized workstations. If these logon attempts are coming from a high-value account, then it might relate to malicious intent. In addition, logon attempts from locked expired, or disabled accounts could indicate mal-intentional use of resources.
Although it could be optimal to use more secure protocols such as the Kerberos (v5) and avoid these NTLM vulnerabilities, disabling NTLM authentication requests will ultimately hurt productivity and usability. There are still many NTLM authentication requests that need to be verified.
Kerberos is now the preferred authentication method used in Active Directory environments. As a good practice, before using more secure protocols like Kerberos and forcing Windows to limit NTLM traffic, it is first recommended to audit all security logs and events related to NTLM authentication. For these audits, there are a variety of tools you could use.
How to Monitor the Windows Event ID 4776
The Windows Event ID 4776 is a type of event log that should be monitored on an ongoing daily basis. You could use different practices and tools. We recommend knowing first how to properly use the Windows Event Viewer (along with its built-in capabilities) and then expanding to more robust audit tools like the ADAudit Plus.
1. Windows Event Viewer
Windows Event Viewer (From Windows Vista 7, Server 2008, and newer versions) allows you to introduce automation by associating a task to a specific event or log. When an event such as the Event ID 4776 is generated, you can associate it with a specific automated task. For instance, you can link it to an email, “Send me an email when Windows Event ID 4776 is generated”.
Windows Event Viewer does have some limitations, especially when it comes to its alerting and reporting engine. For instance, the email won’t give you granular information, such as the type of errors (i.e., attempts from unauthorized workstations, locked accounts, misspelled usernames, or outside business hours). In addition, Event Viewer also does not provide granular filtering capabilities to help you find what you are looking for.
2. ManageEngine ADAudit Plus
ManageEngine ADAudit Plus is an UBA-driven audit solution for full visibility into Active Directory environments. It provides real-time monitoring, behavior analytics, and reporting. This solution is perfect for monitoring the Windows Event ID 4776, as well as other events like ID 4724, 4726, 4769, 4768, 4740, and more.
Key Features
- Apply granular filters to look for specific threats.
- Get notified via email and SMS.
- Detect abnormal behaviors with UEBA (User and Entity Behavior Analytics).
- Out-of-the-box compliance reports for SOX, HIPAA, PCI, FISMA, GLBA, and the GDPR.
ADAudit Plus is a tool designed to monitor logons, analyze lockouts, and spot changes made to users, groups, OUs, or any Active Directory object. In addition, with the ADAudit Plus, you can also monitor local logons (NTLM), including changes made to users, groups, and security policies on Windows Servers. You can also monitor and audit various aspects within Windows workstations, including active time, changes to local users, security policies, USB activity, and more.
Download a 30-day ADAudit Plus trial, and start monitoring the Windows Event ID 4776, today.
Summary
The Windows Event ID 4776 (Audit Failure) – “The domain controller attempted to validate the credentials for an account” is an important event log that alerts you when a failed authentication event happens through the NTLM. This event log gives you valuable information, such as the workstation name, account, and the system or server used to pass the login request.
A way to solve this type of vulnerability is to audit NTLM authentication on this domain, monitor it, and, if possible, restrict it.
To audit and monitor this event successfully, learn how to use the Windows Event Viewer properly and then expand to more robust audit tools like the ADAudit Plus.
Windows Event ID 4776 FAQs
What does Event ID 4776 indicate?
Event ID 4776 indicates an attempted logon to a computer or network resource using a specific user account. This event is generated on the computer where the logon attempt was made.
What information is included in an Event ID 4776 log?
An Event ID 4776 log includes information such as the source network address, the logon type, the authentication package used, and the status of the logon attempt.
How can Event ID 4776 be used for security purposes?
Event ID 4776 can be used for security purposes by monitoring for unusual or unauthorized logon attempts. This can help detect potential security incidents or unauthorized access to sensitive information.
Can Event ID 4776 be used to track logon activity on a network?
Yes, Event ID 4776 can be used to track logon activity on a network by collecting and analyzing the event logs from all relevant computers.
How can I view Event ID 4776 logs in Windows?
To view Event ID 4776 logs in Windows, you can use the Event Viewer tool and filter the security log for Event ID 4776.
Can Event ID 4776 be disabled?
No, Event ID 4776 cannot be disabled. It is an important security event that is generated by the operating system and is critical for monitoring and auditing logon activity on a computer or network.
Despite what this event says, the computer is not necessarily a domain controller; member servers and workstations also log this event for logon attempts with local SAM accounts.
When a domain controller successfully authenticates a user via NTLM (instead of Kerberos), the DC logs this event. This specifies which user account who logged on (Account Name) as well as the client computer’s name from which the user initiated the logon in the Workstation field.
For Kerberos authentication see event 4768, 4769 and 4771.
This event is also logged on member servers and workstations when someone attempts to logon with a local account.
Authentication Package: Always «MICROSOFT_AUTHENTICATION_PACKAGE_V1_0»
Logon Account: name of the account
Source Workstation: computer name where logon attempt originated
Description Fields in
4776
Error Code:
| C0000064 | user name does not exist |
| C000006A | user name is correct but the password is wrong |
| C0000234 | user is currently locked out |
| C0000072 | account is currently disabled |
| C000006F | user tried to logon outside his day of week or time of day restrictions |
| C0000070 | workstation restriction |
| C0000193 | account expiration |
| C0000071 | expired password |
| C0000224 | user is required to change password at next logon |
| C0000225 | evidently a bug in Windows and not a risk |
Stay up-to-date on the Latest in Cybersecurity
Sign up for the Ultimate IT Security newsletter
to hear about the latest webinars, patches, CVEs, attacks, and more.
Your Domain Controller’s Windows Event Viewer might be logging tons of security events with strange usernames, misspelled names, attempts with expired or lockout accounts, or strange logon attempts outside business hours— all labeled with the Event ID 4776.
The “Event ID 4776: The computer attempted to validate the credentials for an account” gives you valuable information to help identify the sources of these attempts. Knowing how to troubleshoot and monitor these events can be detrimental to identifying potential brute force dictionary attacks or mal-intentional account uses.
In this post, we’ll go through the technical explanation of what is the Windows Event ID 4776, the details on how to read it, how to troubleshoot or solve the events, and how to monitor and audit using specific software.
Introduction: What is Windows Event ID 4776
“Event ID 4776: The computer attempted to validate the credentials for an account”
You might have come across the log Event ID 4776 while looking at your event logs in a Domain Controller (DC). This event tells you that this specific DC (but also servers and workstations) was used as a logon server to validate credentials. The event ID 4776 is logged every time the DC tries to validate the credentials of an account using NTLM (NT LAN Manager).
Event ID 4776 is a credential validation event that can either represent success or failure. It is displayed in Windows 2008 R2 and 7, Windows 2012 R2 and 8.1, Windows 2016 and 10, and Windows Server 2019 and 2022.
Note: The Event ID 4776 is not only logged for domain controllers attempting to validate credentials but also for other member Windows servers or workstations used for logon attempts with a local SAM account. This is because the NTLM is the default authentication mechanism for local logon.
Let’s go over the details of the Windows Event ID 4776
The domain controller attempted to validate the credentials for an account.Authentication Package: Always "MICROSOFT_AUTHENTICATION_PACKAGE_V1_0"Logon Account: name of the accountSource Workstation: computer name where logon attempt originatedError Code: 0x0
Every logon attempt on a domain controller is recorded on the DC. The DC logs the event ID 4776 when it validates the credentials and either succeeds or fails to authenticate a user via NTLM (not Kerberos). In addition, if there was a logon attempt via a local SAM account, where a server or a workstation validates credentials, then the event ID 4776 is logged on the local machine.
The event (as described in the details above) specifies:
- The authentication package specifies the package, which is always “MICROSOFT_AUTHENTICATION_PACKAGE_V1_0”.
- The Logon Account is the account name of the user or computer that attempted to log on. A logon account can also be a well-known security principle.
- The Source Workstation is the client’s computer name (source workstation) used to initiate the logon.
- Error Code The Error Code describes whether the authentication succeeded or failed (and the reasons). If you succeed, you’ll see an 0x0 error code, but if it fails, you’d see something other than 0x0—more on error codes in the next section.
Details on Windows Event ID 4776 Error Code
- Error Code equals (0x0) If this field is 0x0, the credentials were successfully validated as “Authentication Success – Event ID 4776 (S)”. No errors.
- Error Code not equal to (0x0) If the field is not equal to 0x0, it means that the credentials were not successfully validated (failed) “Authentication Failure – Event ID 4776 (F)”. Below is a table with more descriptions of the error code- not equal to 0x0.
| Error Code | Description |
|---|---|
| 0xC0000064 | Incorrect username. The username does not exist. |
| 0xC000006A | The username is correct, but not the password. |
| 0xC000006D | A generic logon failure. NTLM authentication-level mismatch. |
| 0xC000006F | Unauthorized account logon. Outside an authorized day or hour. |
| 0xC0000070 | Unauthorized account logon from a restricted workstation. |
| 0xC0000071 | The user tried to log on with an expired password. |
| 0xC0000072 | Unauthorized account logon due to a disabled account. |
| 0xC0000193 | Unauthorized account logon due to an expired account. |
| 0xC0000224 | A flag that the user needs to change the password at the next logon. |
| 0xC0000225 | Known to be a Windows bug. Not a risk. |
| 0xC0000234 | Attempted logon with a locked account. |
| 0xC0000371 | The local account storage does not contain information about the specific account. |
Troubleshooting the Windows Event ID 4776
If the Windows Event ID 4776 (S) is successful, you don’t have a problem. However, the problem starts when you get a few to hundreds or thousands of Windows Event ID 4776 (F) failed attempts. Although this would start to look like a problem, let us not draw quick conclusions just yet.
Although the evidence might indicate that your workstation is being a target of a brute force dictionary or rainbow attack, it could also indicate a relatively inoffensive system (such as a printer) is trying to authenticate with expired credentials.
How to solve the Windows Event ID 4776 failed attempts
- Start by identifying the logon account and the source workstation As you learned from the previous section, Event ID 4776 shows you the account name and the source workstation. Remember authentication happens via NTLM, which can help you identify the user or workstation quickly. But still, the source workstation could be attempting to log from outside, carrying a blank name, and also, the account could be random (made up). So, you’ll have to dig deeper.
- If this source workstation is blank or unknown To find out the source of an unknown workstation, you’ll need to involve other tools.
- Packet Sniffer Use third-party tools such as Wireshark deployed on the DC to capture the traffic at the same time as these events. You’ll need to use capture and display filters on Wireshark to be able to find exactly the source of these events. And also be able to correlate the exact time in Windows Event Viewer with Wireshark when this event happens. In addition, with Wireshark, you can quickly identify IP addresses to start drawing a better picture of where these logons are coming from.
- Network debugger Another handy third-party tool is a network debugger. Enable the NetLogon debugging utility on your DC. This tool will generate a log file with all these authentication requests. You can review this log file and find out where they originate.
- DCDiag The DCDiag is a Domain Controller Health Check tool that helps you with troubleshooting. Aside from running different health checks on the DC, the DCdiag also logs additional details like errors, warnings, or informational messages. Use the DCDiag with the verbose output (/v) to expand the output size.
- If a remote client is trying to authenticate using RDP (port 3389) You or the sys admin might have the port 3389 (RDP) open for users that connect remotely to machines inside the domain. When using the RDP, bear in mind that RDP prefers Kerberos to authenticate, but if it fails, it will fall back to using NTLM instead. Thus, this could be a reason you received the Event ID 4776 with an unknown source workstation. Below are a few solutions you can try:
- Use your firewall One of the most simple solutions is to use the firewall. Instead of using the denylists (allow all block some), use the zero-trust (or whitelists) approach (block all allow some) to only allow authorized attempts originating outside the network.
- Use a VPN A more advanced and efficient solution is to set up a VPN that allows remote users to connect to the local server and then authenticate normally.
Why should you monitor the Windows Event ID 4776
Always monitor the Windows Event ID 4776 to discover and list all the NTLM authentication attempts in your domain. Look for the events ID 4776 that were initiated by the accounts that are unauthorized or shouldn’t be using NTLM in the first place. Always remember that NTLM should only be used for local logon attempts (this is why you shouldn’t use RDP, but a VPN instead).
The reasons to monitor Event ID 4776:
- Identify relay and cracking attacks The NTLM authentication mechanism is vulnerable to relay attacks (fraudulent interception of information). First and most importantly, NTLM does not support modern cryptographic algorithms like SHA-256 or AES-256. This lack of encryption also makes it vulnerable to offline cracking attacks.
- Find reverse brute force, brute force, or enumeration attacks Monitor the Windows Event ID 4776 and keep track of multiple logon attempts within a short period, and with particular qualities like using multiple incorrect usernames. This type of behavior is strongly related to reverse brute force and enumeration attacks. In a similar case, you can keep track of this event and look for multiple logon attempts with incorrect (or misspelled password) within short periods. This behavior is related to brute-force attacks.
- Find potential malicious intent Keeping track of the Windows Event ID 4776 can help you find logon attempts outside authorized business hours or from unauthorized workstations. If these logon attempts are coming from a high-value account, then it might relate to malicious intent. In addition, logon attempts from locked expired, or disabled accounts could indicate mal-intentional use of resources.
Although it could be optimal to use more secure protocols such as the Kerberos (v5) and avoid these NTLM vulnerabilities, disabling NTLM authentication requests will ultimately hurt productivity and usability. There are still many NTLM authentication requests that need to be verified.
Kerberos is now the preferred authentication method used in Active Directory environments. As a good practice, before using more secure protocols like Kerberos and forcing Windows to limit NTLM traffic, it is first recommended to audit all security logs and events related to NTLM authentication. For these audits, there are a variety of tools you could use.
How to Monitor the Windows Event ID 4776
The Windows Event ID 4776 is a type of event log that should be monitored on an ongoing daily basis. You could use different practices and tools. We recommend knowing first how to properly use the Windows Event Viewer (along with its built-in capabilities) and then expanding to more robust audit tools like the ADAudit Plus.
1. Windows Event Viewer
Windows Event Viewer (From Windows Vista 7, Server 2008, and newer versions) allows you to introduce automation by associating a task to a specific event or log. When an event such as the Event ID 4776 is generated, you can associate it with a specific automated task. For instance, you can link it to an email, “Send me an email when Windows Event ID 4776 is generated”.
Windows Event Viewer does have some limitations, especially when it comes to its alerting and reporting engine. For instance, the email won’t give you granular information, such as the type of errors (i.e., attempts from unauthorized workstations, locked accounts, misspelled usernames, or outside business hours). In addition, Event Viewer also does not provide granular filtering capabilities to help you find what you are looking for.
2. ManageEngine ADAudit Plus
ManageEngine ADAudit Plus is an UBA-driven audit solution for full visibility into Active Directory environments. It provides real-time monitoring, behavior analytics, and reporting. This solution is perfect for monitoring the Windows Event ID 4776, as well as other events like ID 4724, 4726, 4769, 4768, 4740, and more.
Key Features
- Apply granular filters to look for specific threats.
- Get notified via email and SMS.
- Detect abnormal behaviors with UEBA (User and Entity Behavior Analytics).
- Out-of-the-box compliance reports for SOX, HIPAA, PCI, FISMA, GLBA, and the GDPR.
ADAudit Plus is a tool designed to monitor logons, analyze lockouts, and spot changes made to users, groups, OUs, or any Active Directory object. In addition, with the ADAudit Plus, you can also monitor local logons (NTLM), including changes made to users, groups, and security policies on Windows Servers. You can also monitor and audit various aspects within Windows workstations, including active time, changes to local users, security policies, USB activity, and more.
Download a 30-day ADAudit Plus trial, and start monitoring the Windows Event ID 4776, today.
Summary
The Windows Event ID 4776 (Audit Failure) – “The domain controller attempted to validate the credentials for an account” is an important event log that alerts you when a failed authentication event happens through the NTLM. This event log gives you valuable information, such as the workstation name, account, and the system or server used to pass the login request.
A way to solve this type of vulnerability is to audit NTLM authentication on this domain, monitor it, and, if possible, restrict it.
To audit and monitor this event successfully, learn how to use the Windows Event Viewer properly and then expand to more robust audit tools like the ADAudit Plus.
Windows Event ID 4776 FAQs
What does Event ID 4776 indicate?
Event ID 4776 indicates an attempted logon to a computer or network resource using a specific user account. This event is generated on the computer where the logon attempt was made.
What information is included in an Event ID 4776 log?
An Event ID 4776 log includes information such as the source network address, the logon type, the authentication package used, and the status of the logon attempt.
How can Event ID 4776 be used for security purposes?
Event ID 4776 can be used for security purposes by monitoring for unusual or unauthorized logon attempts. This can help detect potential security incidents or unauthorized access to sensitive information.
Can Event ID 4776 be used to track logon activity on a network?
Yes, Event ID 4776 can be used to track logon activity on a network by collecting and analyzing the event logs from all relevant computers.
How can I view Event ID 4776 logs in Windows?
To view Event ID 4776 logs in Windows, you can use the Event Viewer tool and filter the security log for Event ID 4776.
Can Event ID 4776 be disabled?
No, Event ID 4776 cannot be disabled. It is an important security event that is generated by the operating system and is critical for monitoring and auditing logon activity on a computer or network.
Windows Server 2008
В терминале работает около 100 пользователей
Периодически в журнале появляется множество записей
Компьютер попытался проверить учетные данные учетной записи.
Пакет проверки подлинности: MICROSOFT_AUTHENTICATION_PACKAGE_V1_0
Учетная запись входа: ADMINISTRATOR
Исходная рабочая станция:
Код ошибки: 0xc0000064
Подробно
Имя журнала: Security
Источник: Microsoft-Windows-Security-Auditing
Дата: 24.03.2023 15:18:29
Код события: 4776
Категория задачи:Проверка учетных данных
Уровень: Сведения
Ключевые слова:Аудит отказа
Пользователь: Н/Д
Компьютер: TerminalNew.rforest.local
Описание:
Компьютер попытался проверить учетные данные учетной записи.
Пакет проверки подлинности: MICROSOFT_AUTHENTICATION_PACKAGE_V1_0
Учетная запись входа: ADMINISTRATOR
Исходная рабочая станция:
Код ошибки: 0xc0000064
Xml события:
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="Microsoft-Windows-Security-Auditing" Guid="{54849625-5478-4994-A5BA-3E3B0328C30D}" />
<EventID>4776</EventID>
<Version>0</Version>
<Level>0</Level>
<Task>14336</Task>
<Opcode>0</Opcode>
<Keywords>0x8010000000000000</Keywords>
<TimeCreated SystemTime="2023-03-24T12:18:29.848747700Z" />
<EventRecordID>40204636</EventRecordID>
<Correlation />
<Execution ProcessID="976" ThreadID="122172" />
<Channel>Security</Channel>
<Computer>TerminalNew.rforest.local</Computer>
<Security />
</System>
<EventData>
<Data Name="PackageName">MICROSOFT_AUTHENTICATION_PACKAGE_V1_0</Data>
<Data Name="TargetUserName">ADMINISTRATOR</Data>
<Data Name="Workstation">
</Data>
<Data Name="Status">0xc0000064</Data>
</EventData>
</Event>Варьируется только пользователь
ADMINISTRATOR
ADMIN
АДМИНИСТРАТОР
Как по этой информации можно вычислить программу, которая это делает? Или под каким пользователем?