Event Id 4634 event is generated when a logon session is terminated or is destroyed. The session is no longer exists.
When the user initiated the logoff procedure, you will see both Event Id 4647 and 4634.
The main difference between Event Id 4647 vs 4634 is that event id 4647 is generated when a user-initiated the logoff procedure using the logoff function, and event id 4634 is generated when a logon session is terminated and no longer exists.
Event Id 4634 may be positively correlated with Event Id 4624: An account was successfully logged on”. Event using the Login ID value.
Event Id 4634 logon type 2 means user logon to this computer.
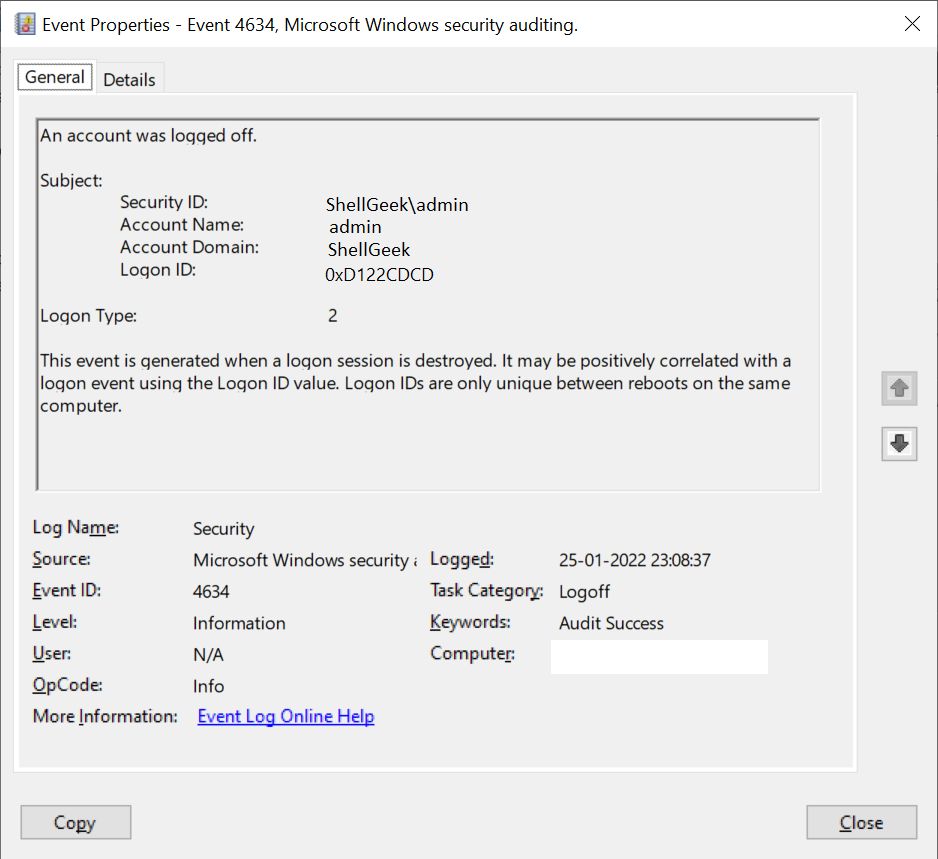
In this article, we will discuss event Id 4634, information about event ID 4634, event id 4634 remote desktop (RDP) session terminated, event id 4634 logon types like 2,3,5,7 and 10.
Event ID 4634 Information
Let’s understand event ID 4634 in detail with its fields.
Event Id 4634 XML format
- <Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
- <System>
<Provider Name="Microsoft-Windows-Security-Auditing" Guid="{62736363-7623-8273-B5CA-2E3C0352D30E}" />
<EventID>4634</EventID>
<Version>0</Version>
<Level>0</Level>
<Task>14339</Task>
<Opcode>0</Opcode>
<Keywords>0x8010000000000000</Keywords>
<TimeCreated SystemTime="2022-01-22T18:10:21.495462300Z" />
<EventRecordID>16708</EventRecordID>
<Correlation />
<Execution ProcessID="520" ThreadID="1084" />
<Channel>Security</Channel>
<Computer>DC01.ShellGeek.local</Computer>
<Security />
</System>
- <EventData>
<Data Name="TargetUserName">admin</Data>
<Data Name="TargetUserSid">S-1-4-21</Data>
<Data Name="TargetDomainName">SHELLGEEK</Data>
<Data Name="TargetLogonId">0xd34ccae7</Data>
<Data Name="LogonType">2</Data>
</EventData>
</Event>Cool Tip: How to convert XML to CSV file in the PowerShell!
Fields Description:
Subject Information
- Security Id: Security ID for an account that was logged off.
- Account Name: The name of the account that was logged off.
- Account Domain: Domain name
- Logon ID: It is of HexInt64 type. It contains the hexadecimal value which you can use to correlate event id 4634 with a recent event that may contain the same Logon ID. For example, event Id 4624 – “An account was succssfully logged on.”
- LogonType: It contains value of type UInt32 to represent the type of logon which was used.
Cool Tip: Event Id 4771 – Kerberos pre-authentication failed!
The Logon Type table shows all possible values for this field.
| Logon Type | Logon Title | Description |
|---|---|---|
| 2 | Interactive | A user logged on to this computer. |
| 3 | Network | A user or computer logged on to this computer from the network. |
| 4 | Batch | Batch logon type is used by batch servers, where processes may be executing on behalf of a user without their direct intervention. |
| 5 | Service | A service was started by the Service Control Manager. |
| 7 | Unlock | This workstation was unlocked. |
| 8 | NetworkCleartext | A user logged on to this computer from the network. The user’s password was passed to the authentication package in its unhashed form. The built-in authentication packages all hash credentials before sending them across the network. The credentials do not traverse the network in plaintext (also called cleartext). |
| 9 | NewCredentials | A caller cloned its current token and specified new credentials for outbound connections. The new logon session has the same local identity but uses different credentials for other network connections. |
| 10 | RemoteInteractive | A user logged on to this computer remotely using Terminal Services or Remote Desktop. |
| 11 | CachedInteractive | A user logged on to this computer with network credentials that were stored locally on the computer. The domain controller was not contacted to verify the credentials. |
Cool Tip: Event Id 4776 Code 0xc0000234 – Fix to find the source of attempt!
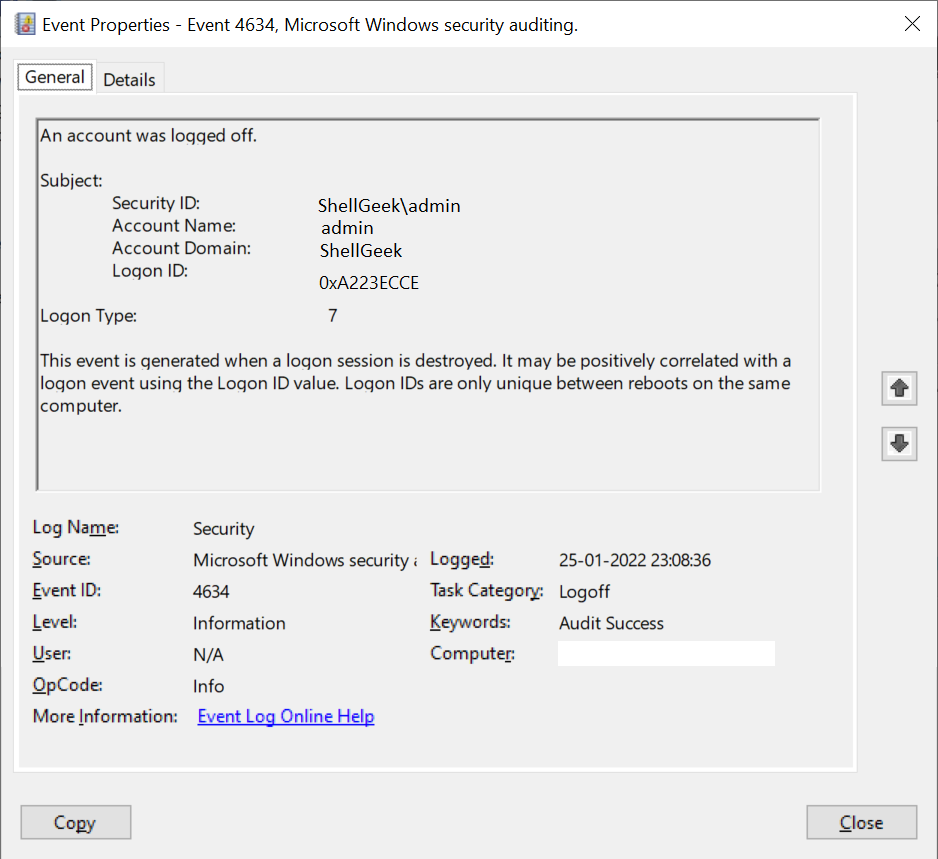
Event Id 4634 logon type 7
When the user unlocks the previously locked workstation, it logs the event id 4634 logon type 7 event.
When the user unlocks the previously locked workstation, it logs the event id 4634 logon type 7 event.
Cool Tip: How to manipulate Active Directory UserAccountControl flags in PowerShell!
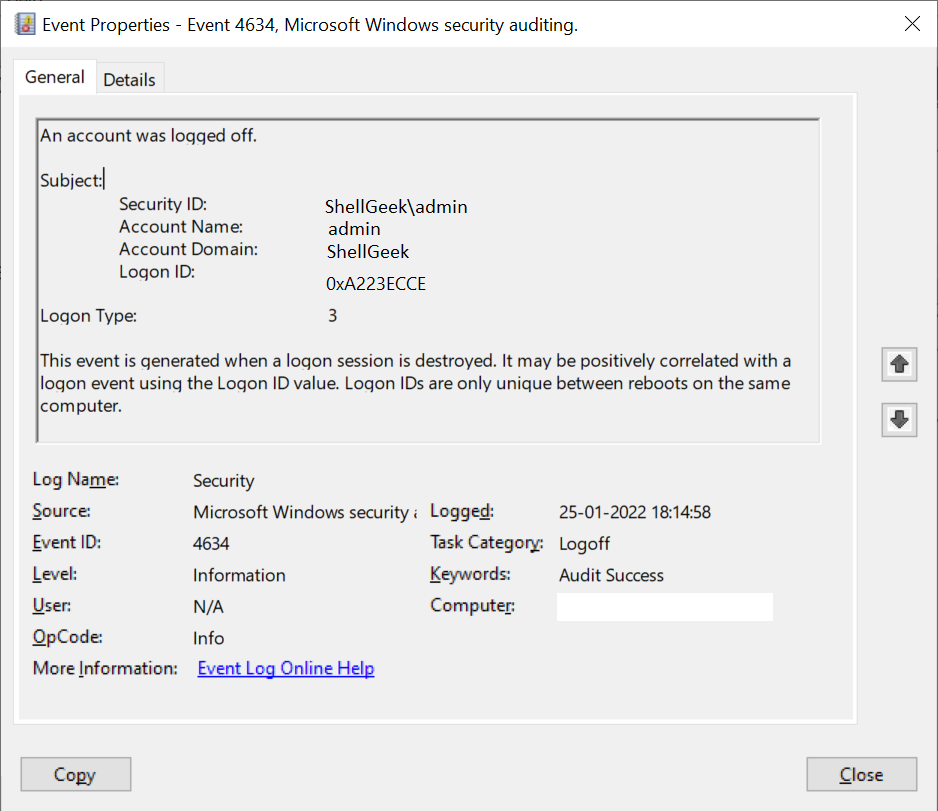
Event Id 4634 logon type 3
Event Id 4634 logon type 3 means that the user or computer logged on to this computer from the network.
The user or computer accesses the computer from the network or tries to access shared resources on the computer, it logs the event id 4634 logon type 3 event.
Cool Tip: Event Id 4625 Status Code 0xc000006a – Fix to find the source of attempt!
Conclusion
I hope the above article on Event Id 4634: “An account was logged off” is helpful to you.
Event Id 4634 helps you to monitor the events related to logon attempts, logged off, remote desktop activities from the network.
Cool Tip: Event Id 4670 – Permissions on an object were changed!
Different types of Event Id 4634 logon type like logon type 2, logon type 3, logon type 7, logon type 10 provides detailed description about the event.
This article is using logon types as per the official Microsoft KB article. Refer for more details on these logon types.
You can find more topics about PowerShell Active Directory commands and PowerShell basics on the ShellGeek home page.
You can read more on other windows security and system event logs as given:
- Event Id 4670 – System restart or shutdown
- Event Id 4624 – An account was successfully logged on.
In this article I am going to explain about the Active Directory user’s Logoff Event ID 4634, how to enable this event via group policy, how to enable this event via auditpol, and how to track user’s logon duration from logon 4624 and logoff 4634 events.
Refer this article Tracking User Logon Activity using Logon and Logoff Events to know about how to track user’s logon duration from logon 4624 and logoff 4634 events.
Summary:
- Event ID 4634 Log Source
- How to enable Logoff event 4634 through Group Policy
- How to enable Logoff event 4634 using Auditpol
- How to stop/disable logoff event 4634
Event ID 4634 Log Source
Log Name: Security Source: Microsoft-Windows-Security-Auditing Date: 11/5/2013 2:28:53 PM Event ID: 4634 Task Category: Logoff Level: Information Keywords: Audit Success User: N/A Computer: myPC.myDomain.com Description: An account was logged off. Subject: Security ID: SYSTEM Account Name: myPC$ Account Domain: myDomain Logon ID: 0x1F759B Logon Type: 3 This event is generated when a logon session is destroyed. It may be positively correlated with a logon event using the Logon ID value. Logon IDs are only unique between reboots on the same computer.
How to enable Logoff event 4634 through Group Policy
1. Open Group Policy Management Console by running the command gpmc.msc
2. Expand the domain node, then right-click on the Default Domain Policy, and click Edit option
3. Expand the Computer Configuration node, go to the node Audit Policy(Computer Configuration->Policies->Windows Settings->Security Settings->Local Policies->Audit Policy).
4. Navigate to the right side pane, select the policy Audit logon events, and set the success audit value.
5. In Windows 7/Server 2008 R2 and later versions, you can enable Event ID 4634 also through Advanced Audit Policy Configuration. Expand the Computer Configuration, and go to the node Advanced Audit Policy Configuration (Computer Configuration->Polices->Windows Settings->Security Settings->Advanced Audit Policy Configuration)
6. Expand this node, go to Logon/Logoff (Audit Polices-> Logon/Logoff ), then select the Setting
Audit Logoff, and set its value as Success
8. Run the command GPUpdate /force to apply this setting in all the all the Computers
How to enable Logoff Event ID 4634 using Auditpol
Auditpol.exe is the command line utility tool to change Audit Security settings as category and sub-category level. It is available by default Windows 2008 R2 and later versions/Windows 7 and later versions. By using Auditpol, we can get/set Audit Security settings per user level and computer level.
Note: You should run Auditpol command with elevated privilege (Run As Administrator);
You can enable audit Event ID 4634 by using the following command
Auditpol /set /subcategory:"Logoff" /success:enable
How to stop/disable Event ID 4634
You can disable success audit Event ID 4634 by using the following command
Auditpol /set /subcategory:"Logoff" /success:disable
You can also stop this event by removing the success setting from the GPO in the setting path Computer Configuration->Polices->Windows Settings->Security Settings->Advanced Audit Policy Configuration->Audit Polices->Logon/Logoff->Audit Logoff.
Note: You need to refresh/update GPO for every change by running the command GPUpdate/force.
Note : This article is applies to Windows Server 2008,Windows Server 2008 R2, Windows Server 2012, Windows 7 and Windows 8.
Thanks,
Morgan
Software Developer
Also see event ID 4647 which Windows logs instead of this event in the case of interactive logons when the user logs out.
This event signals the end of a logon session and can be correlated back to the logon event 4624 using the Logon ID.
For network connections (such as to a file server), it will appear that users log on and off many times a day. This phenomenon is caused by the way the Server service terminates idle connections.
If a user turns off his/her computer, Windows does not have an opportunity to log the logoff event until the system restarts. Therefore, some logoff events are logged much later than the time at which they actually occur.
ANONYMOUS LOGONs are routine events on Windows networks.
Microsoft’s comments:
This event does not necessarily indicate the time that a user has stopped using a system. For example, if the computer is shut down or loses network connectivity it may not record a logoff event at all.
Logon Type: indicates how the user was logged on. See 4624 for explanation of these codes.
Description Fields in
4634
Subject:
- Security ID: %1
- Account Name: %2
- Account Domain: %3
- Logon ID: %4
- Logon Type: %5
Stay up-to-date on the Latest in Cybersecurity
Sign up for the Ultimate IT Security newsletter
to hear about the latest webinars, patches, CVEs, attacks, and more.
Hello All,
Hope this post finds you in good health and spirit.
This event shows that logon session was terminated and no longer exists.Event Id 4634 event is generated when a logon session is terminated or is destroyed. The session is no longer exists.

The key distinction between “4647: User initiated logoff.” and “4634: Session ended and no longer exists.” is that 4647 event is issued when logoff procedure is started by a specific account using the logoff function.
When a user logs off using standard methods, the logon type 4647 is more usual for Interactive and RemoteInteractive login types. When the user began the logoff procedure, both 4647 and 4634 events are normally shown.
Using the Logon ID value, it may be positively associated with a “4624: An account was successfully logged on.” event. Only between reboots on the same machine are logon IDs distinct.
Recommendations for Security Monitoring
For 4634:- A user account was logoff.
- To prevent specific login types from being used by accounts that lack the necessary rights.
- Keep track of high-value account activity.
- Recognize irregularities and malevolent behavior.
- To prevent the usage of inactive, external, and restricted accounts
- To guarantee that only accounts on the white list carry out certain precise tasks
to impose rules and requirements.
So, that’s all in this blog. I will meet you soon with some other stuff. Have a nice day !!!
Recommended contents
RODC Installation Guide- Step by step guide to install read only domain controller
RODC Filtered Attribute Set
Installing and configuring a RODC in Windows Server-2012
How to find the GUID of Domain Controller
Group Policy Understanding Group Policy Preferences
Group Policy Verification Tool GPOTool Exe
Group Policy Health Check on Specific Domain Controller
What is Netlogon Folder in Active Directory
How to Create Custom Attributes in Active Directory
How Can I Check the Tombstone Lifetime of My Active Directory Forest
How to Determine a Computers AD Site From the Command Line
How to Check the Active Directory Database Integrity
How to Check the Active Directory Database Integrity
Disabling and Enabling the Outbound Replication
DFS Replication Service Stopped Replication
What is Strict Replication Consistency
How to export replication information in txt file
Repadmin Replsummary
Enabling the outbound replication
Guys please don’t forget to like and share the post.Also join our WindowsTechno Community and where you can post your queries/doubts and our experts will address them .
You can also share the feedback on below windows techno email id.
If you have any questions feel free to contact us on [email protected] also follow us on facebook@windowstechno to get updates about new blog posts.

He is an Active Directory Consultant. He has been working in IT industry for more than 10 years. He is dedicated and enthusiastic information technology expert who always ready to resolve any technical problem. If you guys need any further help on subject matters, feel free to contact us on [email protected] Please subscribe our Facebook page as well website for latest article. https://www.facebook.com/windowstechno
- Remove From My Forums
-
Вопрос
-
Установлен RD GW на Win2k8R2 Std SP1
— введен в домен
— проНАТен 443 наружу, сертификатом подписан Domain CA
используется исключительно для Шлюза RDP
ВНИМАНИЕ вопрос: каждый час логофает юзеров, независимо от их прав в Логах > «Рис. 1»
ЗЫ: дословно происходит следующее, сессия пользователя зависает на 3-4 минуты(ровно в ЧЧ:00 минут), т.е. пользователь ничего не может делать, по истечении этого времени сессия авто-реконектится и можно работать дальше. Либо можно вручную реконектнуться и
работать. В логах ни Error’ов ни Warning’ов, только Microsoft Windows security auditing. Event ID: 4634ЗЫЗЫ: Пробовал переустановить сервер TS GW, результата «0». И мне кажется собака порылась где-то в GroupPolicy, НО ничего подозрительного я в них не нашел …
-
Изменен тип
17 апреля 2012 г. 21:10
-
Изменено
Fedor Сумкин
18 апреля 2012 г. 7:11
-
Изменен тип
Ответы
-
Решили проблумму, разковырял Linux FW и нашел что он обновляет таблицу правил Брандмауера каждый час, что и приводило к данному интересному эффекту. Поставил обновление раз в сутки и все норм.
Что интересное, RDP ни как не реагирует, т.е. напрямую RDP не отпадает, а через Gateway рвет соединение.
-
Помечено в качестве ответа
Fedor Сумкин
10 мая 2012 г. 14:39
-
Помечено в качестве ответа




