BNAME.RU » Код ошибки HTTP 526 Invalid SSL Certificate Cloudflare
Ошибка 526: недействительный сертификат SSL
Ошибка 526 возникает, когда выполняются эти два условия:
Cloudflare не может проверить сертификат SSL на вашем исходном веб-сервере, и
Полный SSL (строгий) SSL устанавливается на вкладке «Обзор» вашего приложения Cloudflare SSL / TLS.
Как устранить ошибку 526 Invalid SSL Certificate?
Для потенциального быстрого исправления установите для SSL значение «Полный» вместо «Полный (строгий)» на вкладке «Обзор» приложения Cloudflare SSL / TLS для домена.
Попросите администратора сервера или поставщика услуг хостинга проверить сертификаты SSL исходного веб-сервера и убедиться, что:
- Сертификат не просрочен
- Сертификат не отозван
- Сертификат подписан центром сертификации (не самоподписанный)
- Запрошенное или целевое доменное имя и имя хоста указаны в общем имени сертификата или альтернативном имени субъекта.
- Ваш исходный веб-сервер принимает соединения через порт SSL порт 443
- Временно приостановите Cloudflare и посетите https://www.sslshopper.com/ssl-checker.html#hostname=www.example.com (замените www.example.com своим именем хоста и доменом), чтобы убедиться, что с исходным SSL нет проблем. сертификат:
Если исходный сервер использует самозаверяющий сертификат, настройте домен на использование полного SSL вместо полного SSL (строгого). См. Рекомендуемые настройки SSL для вашего происхождения.
BNAME.RU » Код ошибки HTTP 526 Invalid SSL Certificate Cloudflare
Ошибка 526: недействительный сертификат SSL
Ошибка 526 возникает, когда выполняются эти два условия:
Cloudflare не может проверить сертификат SSL на вашем исходном веб-сервере, и
Полный SSL (строгий) SSL устанавливается на вкладке «Обзор» вашего приложения Cloudflare SSL / TLS.
Как устранить ошибку 526 Invalid SSL Certificate?
Для потенциального быстрого исправления установите для SSL значение «Полный» вместо «Полный (строгий)» на вкладке «Обзор» приложения Cloudflare SSL / TLS для домена.
Попросите администратора сервера или поставщика услуг хостинга проверить сертификаты SSL исходного веб-сервера и убедиться, что:
- Сертификат не просрочен
- Сертификат не отозван
- Сертификат подписан центром сертификации (не самоподписанный)
- Запрошенное или целевое доменное имя и имя хоста указаны в общем имени сертификата или альтернативном имени субъекта.
- Ваш исходный веб-сервер принимает соединения через порт SSL порт 443
- Временно приостановите Cloudflare и посетите https://www.sslshopper.com/ssl-checker.html#hostname=www.example.com (замените www.example.com своим именем хоста и доменом), чтобы убедиться, что с исходным SSL нет проблем. сертификат:
Если исходный сервер использует самозаверяющий сертификат, настройте домен на использование полного SSL вместо полного SSL (строгого). См. Рекомендуемые настройки SSL для вашего происхождения.
Поставить оценку ( рейтинг )
Категория: Технологии
Просмотров: 1515
Обновлено: 17.12.2021 04:03
Продолжаем обсуждать и правильно настраивать HTTPS (SSL). На некоторых хостингах, например на FirstVDS бесплатные SSL сертификаты Let’s Encrypt могут внезапно перестать работать вообще или каждые 3 месяца автоматически не продлеваются … и т.д. Как вариант решения проблем с плохим хостингом ➡ это воспользоваться бесплатными SSL сертификатами на проекте CloudFlare.
Но и здесь нужно быть внимательным ⇨ не всё всегда идёт хорошо. Заходим в панель управления CloudFlare, в раздел SSL/TLS, чтобы включить HTTPS на сайте (на вашем домене). (Предполагается, что домен вы уже перенесли и настроили.) И выбираем один из чекбоксов:
Off (not secure) ☑ No encryption applied ➡ SSL отключен и не работает
Flexible ☑ Encrypts traffic between the browser and Cloudflare ➡ SSL между пользователем и CloudFlare. Иногда только такой вариант и работает.
Full ☑ Encrypts end-to-end, using a self signed certificate on the server ➡ SSL между пользователем и CloudFlare + до сервера. Это Наиболее распространённый вариант настройки.
Full (strict) ☑ Encrypts end-to-end, but requires a trusted CA or Cloudflare Origin CA certificate on the server ➡ SSL между пользователем и CloudFlare + до сервера, на котором должен быть установлен действующий сертификат, например CA CloudFlare Origin
И ниже ещё одна настройка SSL/TLS Recommender
Каждая из указанных настроек может создавать те или иные проблемы на сайте.
Почему на сайте перестал работать https (SSL) ?
Решение
Ошибка Error 526 Invalid SSL certificate появляется, если у вас включены:
SSL/TLS Recommender
или
Full (strict)
1 Что делать?
Просто берём и отключаем эти опции и смотрим результат. Он обычно сразу проявляется, без задержки.
И в завершение ⇔ письмо от CloudFlar с рекомендациями по включению SSL/TLS Recommender
О нашем проекте
Проект Joom-la-la предназначен для начинающих пользователей Системы управления сайтами Joomla; программистов, администраторов. Мы хотим поделиться с вами своими наработками и примерами.
Это один из сотен сайтов, сделанных нами в рамках бренда Petrovich Group. Надеемся быть вам полезными и ждём ваших комментариев
Петрович
Контактная информация
Владивосток, Россия
+ 7 423 2 *** ***
888 (@) jom-la-la.ru
petrovichgroup.ru
****
Новые публикации
Обнаружена ошибка. U…
При попытке сохранить файл configuration появляется сообщение: 0 — Обнаружена ошибка. Unable to load…
После обновления до…
После обновления Joomla до 3.6 в разделе Менеджер расширений — установить появляется Предупреж…
Серия Fatal ошибок в…
В достаточно хороших шаблонах Vina Bonnie, Vina Fashion, IncomeUp, Vina Bagshop есть проблема — они…
[Решено] Ошибка при…
Иногда, при сохранении различного контента ( материала, портфолио), в админке, возникает ошибк…
© Joom-la-la.ru . При любом использовании материалов ссылка на Joom-la-la.ru обязательна.
Все права защищены.
Дима
- Регистрация
- 9 Янв 2019
- Сообщения
- 8
Ошибка 526 .. Что делать при этой ошибке,или как правильно её исправить??
Вложения
-
69.9 KB
Просмотры: 6
Alisa
- Регистрация
- 15 Дек 2017
- Сообщения
- 5,067
Ошибка 526 .. Что делать при этой ошибке,или как правильно её исправить??
Ошибка сертификата. Заходите в панель CloudFlare и там смотрите информацию об ошибке SSL. Активен он или нет и стоит ли Flexible.
Дима
- Регистрация
- 9 Янв 2019
- Сообщения
- 8
Да с полного перешёл на гибкий (Flexible) и всё сразу заработало..Спасибо!
Cloudflare error 526 triggers when Cloudflare is unable to validate server’s SSL/TLS certificate. It normally happens with Full SSL(Strict) mode in the Cloudflare.
As a part of our Server Management Services, we help our customers to fix similar Cloudflare related errors regularly.
Let us today discuss the possible causes and fixes for this error.
What is Cloudflare error 526?
While we use Cloudflare, it involves two SSL/TLS certificates. One is provided by Cloudflare and the other by the origin server. The First certificate shown in the browser while visiting the website is the Cloudflare one. Origin server’s certificate protects data exchanges between the server and Cloudflare.
The Full (strict) mode SSL option ensures a secure connection between both the visitor – Cloudflare domain and Cloudflare – origin web server connections.
Thus if any of it fail to establish a secure connection, it triggers the 526 error as shown below.
Let us now look at the possible reasons for this error.
What are the causes of Cloudflare error 526?
As we discussed earlier, the error 526 triggers when either the certificate provided by Cloudflare or by the origin server fails to establish a secure connection. This generally happens when:
* Cloudflare cannot validate the SSL certificate at your origin web server
* Full SSL (Strict) SSL is set in the Cloudflare SSL/TLS app.
Let us now look at the steps to fix this error.
How to fix Cloudflare error 526?
Full (strict) mode is the most common reason for the 526 error. A quick fix to solve it would be to change the SSL mode to Full instead of Full (strict) from the Overview tab of Cloudflare SSL/TLS section for the particular domain.
If the issue persists even after changing the SSL mode to Full, then it would be more likely related to the origin web server’s SSL certificates. We need to verify that:
1. The certificate is not expired
2. The certificate is not revoked
3. The certificate is signed by a Certificate Authority such as GlobalSign, Verisign, GeoTrust, Comodo, etc, and is not a self-signed SSL certificate.
4. The requested domain name and hostname are in the certificate’s Common Name or Subject Alternative Name.
5. Origin web server accepts connections over port SSL port 443
6. Temporarily pause Cloudflare and cross-check the certificate with any SSL verification sites like https://www.sslshopper.com to verify that no issues exist with the origin SSL certificate.
If the origin server is using an expired, revoked or self -signed certificate, the next step to fix this error would be to install a proper SSL certificate signed by a Certificate Authority.
Likewise, it is important to have the requested domain name and hostname in the certificate’s Common Name or Subject Alternative Name. If we have added a CNAME for the hostname on Cloudflare, the Common Name or SAN may also match the CNAME target.
Cloudflare can also issue origin certificates to you on request if you don’t want to pay for or acquire one from a third-party. The 526 error should disappear after the installation of a valid certificate on the origin server and the server it accept secure (HTTPS) connections.
[Need any further assistance in fixing Cloudflare errors? – We’re available 24*7]
Conclusion
In short, Cloudflare error 526 occurs when Cloudflare is unable to validate the server’s SSL/TLS certificate. Today, we saw how our Support Engineers fix this error.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.
GET STARTED
var google_conversion_label = «owonCMyG5nEQ0aD71QM»;
#web #dns #ssl-certificate #cloudflare
#web #dns #ssl-сертификат #cloudflare
Вопрос:
Я перенес хостинг своего веб-сайта на Inmotion с Bluehost, но домен в настоящее время находится на Bluehost (на нем был Cloudflare на Bluehost). Теперь я переместил его на хостинг Inmotion и создаю учетную запись Cloudflare, чтобы настроить ее на своем веб-сайте. Я настроил Cloudflare и изменил DNS домена на Cloudflare DNS, но теперь, когда я запускаю Cloudflare с моей панели Cloudflare, на моем веб-сайте отображается ОШИБКА 526. Я много раз обращался в службу поддержки Inmotion и Bluehost, и они сказали мне, что я должен связаться с командой Cloudflare, потому что проблема связана с Cloudflare, и мне там никто не ответил.
Для получения дополнительной информации я использовал все способы, которые были найдены в сообществе Cloudflare или в Google, но не смог решить эту проблему. Пожалуйста, помогите мне.
Комментарии:
1. Вот хороший источник информации для диагностики основной причины этой ошибки: Совет сообщества — исправление ошибки 526: недействительные сертификаты SSL
Ответ №1:
Ошибка Cloudflare 526 срабатывает, когда Cloudflare не может проверить сертификат SSL / TLS сервера. Обычно это происходит в режиме полного SSL (строгого) в Cloudflare.
Какой режим вы используете в cloudflare? Полный (строгий) режим? Если да, посмотрите его:
Full (strict) mode is the most common reason for the 526 error. A quick fix to solve it would be to change the SSL mode to Full instead of Full (strict) from the Overview tab of Cloudflare SSL/TLS section for the particular domain.
If the issue persists even after changing the SSL mode to Full, then it would be more likely related to the origin web server’s SSL certificates. We need to verify that:
1. The certificate is not expired
2. The certificate is not revoked
3. The certificate is signed by a Certificate Authority such as GlobalSign, Verisign, GeoTrust, Comodo, etc, and is not a self-signed SSL certificate.
4. The requested domain name and hostname are in the certificate’s Common Name or Subject Alternative Name.
5. Origin web server accepts connections over port SSL port 443
6. Temporarily pause Cloudflare and cross-check the certificate with any SSL verification sites like https://www.sslshopper.com to verify that no issues exist with the origin SSL certificate.
If the origin server is using an expired, revoked or self -signed certificate, the next step to fix this error would be to install a proper SSL certificate signed by a Certificate Authority.
Likewise, it is important to have the requested domain name and hostname in the certificate’s Common Name or Subject Alternative Name. If we have added a CNAME for the hostname on Cloudflare, the Common Name or SAN may also match the CNAME target.
Cloudflare can also issue origin certificates to you on request if you don’t want to pay for or acquire one from a third-party. The 526 error should disappear after the installation of a valid certificate on the origin server and the server it accept secure (HTTPS) connections.
Если вы хотите изменить другой режим:
На панели CloudFlare Domain -> SSL/TLS -> Overview -> Pick the mode ). Когда вы выбираете режим, отображается, как будет работать шифрование.
Если вы используете порт 80 / tcp в конечной точке, вам необходимо использовать гибкий режим (шифрует трафик между браузером и Cloudflare).
Но если вы используете порт 443 / tcp в конечной точке, вам необходимо использовать полный режим (шифрует сквозной, используя самозаверяющий сертификат на сервере). Для полного режима доступно использование самозаверяющих SSL-сертификатов на вашем виртуальном хосте.
| pcx_content_type | title | source |
|---|---|---|
|
troubleshooting |
Troubleshooting Cloudflare 5XX errors |
Troubleshooting Cloudflare 5XX errors – Cloudflare Help Center
Error analytics
Error Analytics per domain are available within the support portal for your account. Error Analytics allows insight into overall errors by HTTP error code and provides the URLs, responses, origin server IP addresses, and Cloudflare data centers needed to diagnose and resolve the issue. Error Analytics are based on a 1% traffic sample.
To view Error Analytics:
- Navigate to the Cloudflare support portal. Refer to instructions about filing a support ticket for information on how to reach the support portal.
- Scroll down to the Error Analytics section.
- Click Visit Error Analytics.
- Enter the domain to investigate.
- A graph of Errors over time is displayed.
- Click on a status code in the table beneath the graph to expand traffic error details.
Error 500: internal server error
Error 500 generally indicates an issue with your origin web server. Error establishing database connection is a common HTTP 500 error message generated by your origin web server. Contact your hosting provider to resolve.
Resolution
Provide details to your hosting provider to assist troubleshooting the issue.
However, if the 500 error contains “cloudflare” or “cloudflare-nginx” in the HTML response body, provide Cloudflare support with the following information:
- Your domain name
- The time and timezone of the 500 error occurrence
- The output of www.example.com/cdn-cgi/trace from the browser where the 500 error was observed (replace www.example.com with your actual domain and host name)
{{
}}
If you observe blank or white pages when visiting your website, confirm
whether the issue occurs when temporarily pausing
Cloudflare
and contact your hosting provider for assistance.
{{}}
Error 502 bad gateway or error 504 gateway timeout
An HTTP 502 or 504 error occurs when Cloudflare is unable to establish contact with your origin web server.
There are two possible causes:
- (Most common cause) 502/504 from your origin web server
- 502/504 from Cloudflare
502/504 from your origin web server
Cloudflare returns an Cloudflare-branded HTTP 502 or 504 error when your origin web server responds with a standard HTTP 502 bad gateway or 504 gateway timeout error:
Resolution
Contact your hosting provider to troubleshoot these common causes at your origin web server:
- Ensure the origin server responds to requests for the hostname and domain within the visitor’s URL that generated the 502 or 504 error.
- Investigate excessive server loads, crashes, or network failures.
- Identify applications or services that timed out or were blocked.
502/504 from Cloudflare
A 502 or 504 error originating from Cloudflare appears as follows:
If the error does not mention “cloudflare,” contact your hosting provider for assistance on 502/504 errors from your origin.
Resolution
To avoid delays processing your inquiry, provide these required details to Cloudflare Support:
- Time and timezone the issue occurred.
- URL that resulted in the HTTP 502 or 504 response (for example: https://www.example.com/images/icons/image1.png)
- Output from browsing to _www.example.com/cdn-cgi/trace_ (replace _www.example.com_ with the domain and host name that caused the HTTP 502 or 504 error)
Error 503: service temporarily unavailable
HTTP error 503 occurs when your origin web server is overloaded. There are two possible causes discernible by error message:
- Error doesn’t contain “cloudflare” or “cloudflare-nginx” in the HTML response body.
Resolution: Contact your hosting provider to verify if they rate limit requests to your origin web server.
- Error contains “cloudflare” or “cloudflare-nginx” in the HTML response body.
Resolution: A connectivity issue occured in a Cloudflare data center. Provide Cloudflare support with the following information:
- Your domain name
- The time and timezone of the 503 error occurrence
- The output of _www.example.com/cdn-cgi/trace_ from the browser where the 503 error was observed (replace www.example.com with your actual domain and host name)
Error 520: web server returns an unknown error
Error 520 occurs when the origin server returns an empty, unknown, or unexpected response to Cloudflare.
Resolution
{{
}}
A quick workaround while further investigating 520 errors is to either
make the record
DNS-only
in the Cloudflare DNS app or temporarily pause
Cloudflare.
{{}}
Contact your hosting provider or site administrator and request a review of your origin web server error logs for crashes and to check for these common causes:
- Origin web server application crashes
- Cloudflare IPs not allowed at your origin
- Headers exceeding 16 KB (typically due to too many cookies)
- An empty response from the origin web server that lacks an HTTP status code or response body
- Missing response headers or origin web server not returning proper HTTP error responses.
upstream prematurely closed connection while reading response header from upstreamis a common error we may notice in our logs. This indicates the origin web server was having issues which caused Cloudflare to generate 520 errors.
{{
}}
520 errors are prevalent with certain PHP applications that crash the
origin web server.
{{}}
If 520 errors continue after contacting your hosting provider or site administrator, provide the following information to Cloudflare Support:
- Full URL(s) of the resource requested when the error occurred
- Cloudflare cf-ray from the 520 error message
- Output from _http://www.example.com/cdn-cgi/trace_ (replace _www.example.com_ with your hostname and domain where the 520 error occurred)
- Two HAR files:
- one with Cloudflare enabled on your website, and
- the other with Cloudflare temporarily disabled.
Error 521: web server is down
Error 521 occurs when the origin web server refuses connections from Cloudflare. Security solutions at your origin may block legitimate connections from certain Cloudflare IP addresses.
The two most common causes of 521 errors are:
- Offlined origin web server application
- Blocked Cloudflare requests
Resolution
Contact your site administrator or hosting provider to eliminate these common causes:
- Ensure your origin web server is responsive
- Review origin web server error logs to identify web server application crashes or outages.
- Confirm Cloudflare IP addresses are not blocked or rate limited
- Allow all Cloudflare IP ranges in your origin web server’s firewall or other security software
- Confirm that — if you have your SSL/TLS mode set to Full or Full (Strict) — you have installed a Cloudflare Origin Certificate
- Find additional troubleshooting information on the Cloudflare Community.
Error 522: connection timed out
Error 522 occurs when Cloudflare times out contacting the origin web server. Two different timeouts cause HTTP error 522 depending on when they occur between Cloudflare and the origin web server:
- Before a connection is established, the origin web server does not return a SYN+ACK to Cloudflare within 15 seconds of Cloudflare sending a SYN.
- After a connection is established, the origin web server doesn’t acknowledge (ACK) Cloudflare’s resource request within 90 seconds.
Resolution
Contact your hosting provider to check the following common causes at your origin web server:
- (Most common cause) Cloudflare IP addresses are rate limited or blocked in .htaccess, iptables, or firewalls. Confirm your hosting provider allows Cloudflare IP addresses.
- An overloaded or offline origin web server drops incoming requests.
- Keepalives are disabled at the origin web server.
- The origin IP address in your Cloudflare DNS app does not match the IP address currently provisioned to your origin web server by your hosting provider.
- Packets were dropped at your origin web server.
If you are using Cloudflare Pages, verify that you have a custom domain set up and that your CNAME record is pointed to your custom Pages domain. Instructions on how to set up a custom Pages domain can be found here.
If none of the above leads to a resolution, request the following information from your hosting provider or site administrator before contacting Cloudflare support:
- An MTR or traceroute from your origin web server to a Cloudflare IP address that most commonly connected to your origin web server before the issue occurred. Identify a connecting Cloudflare IP recorded in the origin web server logs.
- Details from the hosting provider’s investigation such as pertinent logs or conversations with the hosting provider.
Error 523: origin is unreachable
Error 523 occurs when Cloudflare cannot contact your origin web server. This typically occurs when a network device between Cloudflare and the origin web server doesn’t have a route to the origin’s IP address.
Resolution Contact your hosting provider to exclude the following common causes at your origin web server:
- Confirm the correct origin IP address is listed for A or AAAA records within your Cloudflare DNS app.
- Troubleshoot Internet routing issues between your origin and Cloudflare, or with the origin itself.
If none of the above leads to a resolution, request the following information from your hosting provider or site administrator:
- An MTR or traceroute from your origin web server to a Cloudflare IP address that most commonly connected to your origin web server before the issue occurred. Identify a connecting Cloudflare IP from the logs of the origin web server.
- If you use Railgun via a Cloudflare Hosting Partner, contact your hosting provider to troubleshoot the 523 errors.
- If you manage your Railgun installation, provide the following to:
- A traceroute to your origin web server from your Railgun server.
- The most recent syslog file from your Railgun server.
Error 524: a timeout occurred
Error 524 indicates that Cloudflare successfully connected to the origin web server, but the origin did not provide an HTTP response before the default 100 second connection timed out. This can happen if the origin server is simply taking too long because it has too much work to do — e.g. a large data query, or because the server is struggling for resources and cannot return any data in time.
{{
}}
A 522 occurs if the origin web server
acknowledges (ACK) the resource request after the connection has been
established, but does not send a timely response.
{{}}
Resolution
Here are the options we’d suggest to work around this issue:
- Implement status polling of large HTTP processes to avoid hitting this error.
- Contact your hosting provider to exclude the following common causes at your origin web server:
- A long-running process on the origin web server.
- An overloaded origin web server.
{{
}}
Logging request response time at your origin web server helps identify
the cause of resource slowness. Contact your hosting provider or site
administrator for assistance in adjusting log formats or search for
related logging documentation for your brand of web server such as
Apache
or
Nginx.
{{}}
- Enterprise customers can increase the 524 timeout up to 6000 seconds using the proxy_read_timeout API endpoint.
- If you regularly run HTTP requests that take over 100 seconds to complete (for example large data exports), move those processes behind a subdomain not proxied (grey clouded) in the Cloudflare DNS app.
- If error 524 occurs for a domain using Cloudflare Railgun, ensure the lan.timeout is set higher than the default of 30 seconds and restart the railgun service.
Error 525: SSL handshake failed
525 errors indicate that the SSL handshake between Cloudflare and the origin web server failed. Error 525 occurs when these two conditions are true:
- The SSL handshake fails between Cloudflare and the origin web server, and
- Full or Full (Strict) SSL is set in the Overview tab of your Cloudflare SSL/TLS app.
{{
}}
If your hosting provider frequently changes your origin web server’s IP
address, refer to Cloudflare’s documentation on dynamic DNS
updates.
{{}}
Resolution
Contact your hosting provider to exclude the following common causes at your origin web server:
- No valid SSL certificate installed
- Port 443 (or other custom secure port) is not open
- No SNI support
- The cipher suites accepted by Cloudflare does not match the cipher suites supported by the origin web server
{{
}}
If 525 errors occur intermittently, review the origin web server error
logs to determine the cause. Configure Apache to log mod_ssl
errors.
Also, nginx includes SSL errors in its standard error log, but may
possibly require an increased log
level.
{{}}
Additional checks
- Check if you have a certificate installed on your origin server. You can check this article for more details on how to run some tests. In case you don’t have any certificate, you can create and install our free Cloudflare origin CA certificate. Using Origin CA certificates allows you to encrypt traffic between Cloudflare and your origin web server.
- Review the cipher suites your server is using to ensure they match what is supported by Cloudflare.
- Check your server’s error logs from the timestamps you see 525s to ensure there are errors that could be causing the connection to be reset during the SSL handshake.
Error 526: invalid SSL certificate
Error 526 occurs when these two conditions are true:
- Cloudflare cannot validate the SSL certificate at your origin web server, and
- Full SSL (Strict) SSL is set in the Overview tab of your Cloudflare SSL/TLS app.
Resolution
{{
}}
For a potential quick fix, set SSL to Full instead of Full
(strict) in the Overview tab of your Cloudflare SSL/TLS app for
the domain.
{{}}
Request your server administrator or hosting provider to review the origin web server’s SSL certificates and verify that:
- Certificate is not expired
- Certificate is not revoked
- Certificate is signed by a Certificate Authority (not self-signed)
- The requested or target domain name and hostname are in the certificate’s Common Name or Subject Alternative Name
- Your origin web server accepts connections over port SSL port 443
- Temporarily pause Cloudflare and visit https://www.sslshopper.com/ssl-checker.html#hostname=www.example.com (replace www.example.com with your hostname and domain) to verify no issues exists with the origin SSL certificate:
If the origin server uses a self-signed certificate, configure the domain to use Full SSL instead of Full SSL (Strict). Refer to recommended SSL settings for your origin.
527 Error: Railgun Listener to origin error
A 527 error indicates an interrupted connection between Cloudflare and your origin’s Railgun server (rg-listener). Common causes include:
- Firewall interference
- Network incidents or packet loss between the Railgun server and Cloudflare
{{
}}
For additional details to aid troubleshooting, increase Railgun
logging.
{{}}
Common causes of 527 errors include:
- Connection timeouts
- LAN timeout exceeded
- Connection refusals
- TLS/SSL related errors
If contacting Cloudflare support, provide the following information from the Railgun Listener:
- The full content of the railgun.conf file
- The full content of the railgun-nat.conf file
- Railgun log files that detail the observed errors
Connection timeouts
The following Railgun log errors indicate a connection failure between the Railgun Listener and your origin web server:
connection failed 0.0.0.0:443/example.com: dial tcp 0.0.0.0:443: i/o timeout
no response from origin (timeout) 0.0.0.0:80/example.com
Resolution
Contact your hosting provider for assistance to test for connectivity issues between your origin web server and your Railgun Listener. For example, a netcat command tests connectivity when run from the Railgun Listener to the origin web server’s SERVERIP and PORT (80 for HTTP or 443 for HTTPS):
LAN timeout exceeded
The following Railgun Listener log error is generated if the origin web server does not send an HTTP response to the Railgun Listener within the 30 second default timeout:
connection failed 0.0.0.0:443/example.com: dial tcp 0.0.0.0:443: i/o timeout
The time is adjusted by the lan.timeout parameter of the railgun.conf file.
Resolution
Either increase the lan.timeout limit in railgun.conf, or review the web server configuration. Contact your hosting provider to confirm if the origin web server is overloaded.
Connection refusals
The following errors appear in the Railgun logs when requests from the Railgun Listener are refused:
Error getting page: dial tcp 0.0.0.0:80:connection refused
Resolution
Allow the IP of your Railgun Listener at your origin web server’s firewall.
TLS/SSL related errors
The following errors appear in the Railgun logs if TLS connections fail:
connection failed 0.0.0.0:443/example.com: remote error: handshake failure
connection failed 0.0.0.0:443/example.com: dial tcp 0.0.0.0:443:connection refused
connection failed 127.0.0.1:443/www.example.com: x509: certificate is valid for
example.com, not www.example.com
Resolution
If TLS/SSL errors occur, check the following on the origin web server and ensure that:
- Port 443 is open
- An SSL certificate is presented by the origin web server
- the SAN or Common Name of the origin web server’s SSL certificate contains the requested or target hostname
- SSL is set to Full or Full (Strict) in the Overview tab of the Cloudflare SSL/TLS app
{{
}}
If your origin web server SSL certificate is self-signed, set
validate.cert=0 in
railgun.conf.
{{}}
Error 530
HTTP error 530 is returned with an accompanying 1XXX error displayed. Search for the specific 1XXX error within the Cloudflare Help Center for troubleshooting information.
Related resources
- Gathering information to troubleshoot site issues
- Contacting Cloudflare Support
- Customizing Cloudflare error pages
- MTR/Traceroute Diagnosis and Usage
- Cloudflare Community Tips
В этой статье речь пойдёт о том, что представляет из себя Ошибка 526 Invalid SSL certificate. Но прежде важно сказать, что для контроля онлайн статуса сайта, оценки доступности сайта существуют специальные сервисы. Одним из таких сервисов является сервис BAILRY – бесплатная регулярная (периодическая) проверка сайта на доступность. Есть в этом сервисе и платная подписка – для постоянного контроля доступности сайта.
Ошибка 526 возникает, когда выполняются эти два условия:
- Cloudflare не может проверить сертификат SSL на веб-сервере
- Полный SSL (Строгий) SSL установлен на вкладке Обзор вашего приложения Cloudflare SSL / TLS
Рекомендации по исправлению ошибки 526 Invalid SSL certificate
Для возможного быстрого исправления установите SSL на Full вместо Full (strict) на вкладке Overview вашего приложения Cloudflare SSL / TLS для домена.
Попросите вашего администратора сервера или хостинг-провайдера проверить SSL-сертификаты веб-сервера и убедиться, что:
- Сертификат не истек
- Сертификат не отозван
- Сертификат подписывается Certificate Authority (not self-signed)
- Запрашиваемое или целевое доменное имя и имя хоста находятся в общем имени сертификата или альтернативном имени субъекта
- Ваш веб-сервер принимает подключения через порт SSL порт 443
- Временно приостановите Cloudflare и перейдите на страницу https://www.sslshopper.com/ssl-checker.html#hostname=www.example.com (замените www.example.com на ваше имя хоста и домен), чтобы убедиться, что с исходным SSL не существует проблем
Если сервер использует самозаверяющий сертификат, настройте домен для использования Full SSL вместо Full SSL (Strict).
Напоследок важно отметить то, что доверие клиентов и пользователей к вашему сайту, а также позиция в поисковых системах напрямую зависят от доступности вашего ресурса (сайта) в любой момент времени. А контролировать эту доступность вы сможете при помощи сервиса BAILRY – уникального программного продукта не имеющего аналогов на рынке. Чтобы быть в курсе подключите бесплатную регулярную (периодическую) проверку сайта на доступность уже сегодня!
Cloudflare error 526 triggers when Cloudflare is unable to validate server’s SSL/TLS certificate. It normally happens with Full SSL(Strict) mode in the Cloudflare.
As a part of our Server Management Services, we help our customers to fix similar Cloudflare related errors regularly.
Let us today discuss the possible causes and fixes for this error.
What is Cloudflare error 526?
While we use Cloudflare, it involves two SSL/TLS certificates. One is provided by Cloudflare and the other by the origin server. The First certificate shown in the browser while visiting the website is the Cloudflare one. Origin server’s certificate protects data exchanges between the server and Cloudflare.
The Full (strict) mode SSL option ensures a secure connection between both the visitor – Cloudflare domain and Cloudflare – origin web server connections.
Thus if any of it fail to establish a secure connection, it triggers the 526 error as shown below.
Let us now look at the possible reasons for this error.
What are the causes of Cloudflare error 526?
As we discussed earlier, the error 526 triggers when either the certificate provided by Cloudflare or by the origin server fails to establish a secure connection. This generally happens when:
* Cloudflare cannot validate the SSL certificate at your origin web server
* Full SSL (Strict) SSL is set in the Cloudflare SSL/TLS app.
Let us now look at the steps to fix this error.
How to fix Cloudflare error 526?
Full (strict) mode is the most common reason for the 526 error. A quick fix to solve it would be to change the SSL mode to Full instead of Full (strict) from the Overview tab of Cloudflare SSL/TLS section for the particular domain.
If the issue persists even after changing the SSL mode to Full, then it would be more likely related to the origin web server’s SSL certificates. We need to verify that:
1. The certificate is not expired
2. The certificate is not revoked
3. The certificate is signed by a Certificate Authority such as GlobalSign, Verisign, GeoTrust, Comodo, etc, and is not a self-signed SSL certificate.
4. The requested domain name and hostname are in the certificate’s Common Name or Subject Alternative Name.
5. Origin web server accepts connections over port SSL port 443
6. Temporarily pause Cloudflare and cross-check the certificate with any SSL verification sites like https://www.sslshopper.com to verify that no issues exist with the origin SSL certificate.
If the origin server is using an expired, revoked or self -signed certificate, the next step to fix this error would be to install a proper SSL certificate signed by a Certificate Authority.
Likewise, it is important to have the requested domain name and hostname in the certificate’s Common Name or Subject Alternative Name. If we have added a CNAME for the hostname on Cloudflare, the Common Name or SAN may also match the CNAME target.
Cloudflare can also issue origin certificates to you on request if you don’t want to pay for or acquire one from a third-party. The 526 error should disappear after the installation of a valid certificate on the origin server and the server it accept secure (HTTPS) connections.
[Need any further assistance in fixing Cloudflare errors? – We’re available 24*7]
Conclusion
In short, Cloudflare error 526 occurs when Cloudflare is unable to validate the server’s SSL/TLS certificate. Today, we saw how our Support Engineers fix this error.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.
GET STARTED
var google_conversion_label = «owonCMyG5nEQ0aD71QM»;
Introduction
Error 526 is an HTTPS error that happens when the website cannot establish a secure connection, indicating a failed or incomplete SSL handshake. It shows that the SSL certificate on the origin server is invalid, expired, self-signed, not configured correctly, or the certificate was issued by an untrusted Certificate Authority (CA).
In this article, you will learn how to fix the 526 Invalid SSL certificate error.

What Is Error 526?
Error 526 is an SSL certificate error that occurs when Cloudflare cannot verify the SSL certificate presented by the origin server. In case the SSL certificate is invalid, web browsers display a warning message that the website is vulnerable to attacks.
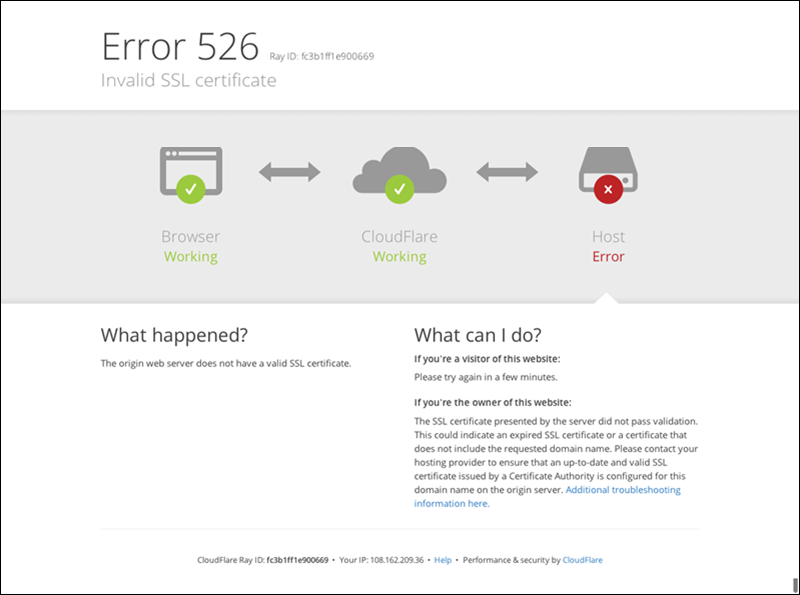
The 526 HTTP response status code is an unofficial server error specific to Cloudflare.
What Causes Error 526 Invalid SSL Certificate?
Error 526 occurs when the origin server’s SSL certificate fails to establish a secure connection. Common causes of the 526 Cloudflare error are:
- Full (strict) SSL mode on Cloudflare. The Full (strict) mode of Cloudflare’s SSL/TLS encryption may cause the 526 error. Moreover, the Full (Strict) mode does not allow unsecured data exchange between Cloudflare servers and the origin server.
- Incorrect SSL certificate installation. If the SSL certificate is not installed correctly, the visitor’s browser fails to recognize it, resulting in error 526.
- SSL certificate not issued by a trusted CA. If the SSL certificate is not issued by a trusted CA, the visitor’s browser does not recognize it as a valid certificate.
- Expired SSL certificate. SSL certificates have a validity period. Once it expires, the certificate becomes invalid.
- Self-signed SSL certificate. Self-signed SSL certificates are not issued by a trusted CA and are not trusted by browsers by default.
- Domain name mismatch. If the SSL certificate domain name does not match the website’s domain name, the visitor’s browser does not recognize it as valid.
- SSL/TLS protocol mismatch. If the SSL/TLS protocol used by the website does not match the protocol supported by the visitor’s browser, the site visitor gets the 526 invalid certificate error.
Depending on the root cause of the issue, there are half a dozen ways to fix Cloudflare’s error 526. The following sections outline how to identify what’s causing the issue and how to fix it.
Method 1: Switch SSL Mode from Full (strict) to Full
Cloudflare offers four SSL modes: Off, Flexible, Full, and Full (Strict). In Full (strict) mode, Cloudflare requires a valid SSL certificate on the origin server. It also verifies the certificate’s hostname against the hostname the browser connects to. In case of any mismatch, Cloudflare returns HTTP status 526 to the browser.
The first thing to do is change the SSL mode from Full (strict) to Full. The Full mode requires an SSL certificate on the origin server, but it does not perform hostname verification.
Follow the steps below to change Cloudflare’s SSL mode from Full (strict) to Full:
1. Log in to your Cloudflare account.
2. Select the domain to change the SSL mode.
3. Navigate to the SSL/TLS tab.
4. Under the Overview tab, look for the Encryption settings.
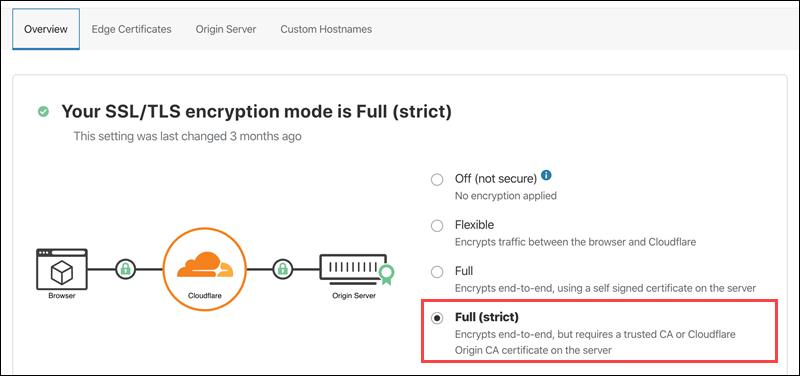
5. If the Full (strict) mode is selected, change it to Full.
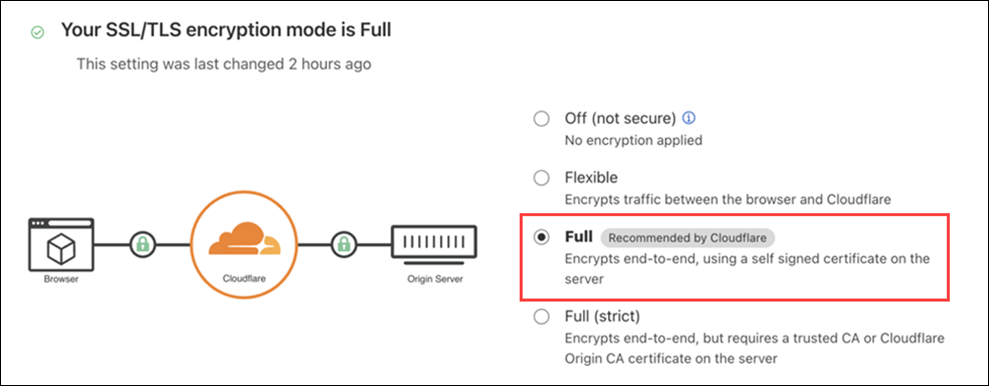
After switching the SSL mode to Full, wait a few minutes and try accessing the website again. If the error persists, try the other methods listed below.
Method 2: Check the SSL Certificate
When an SSL certificate is not installed correctly, it results in a 526 error. Check the SSL certificate installation status by logging into your web hosting account or server. Depending on the hosting provider and the type of hosting plan, access the account following one of these methods:
- Access the account using a web-based control panel like cPanel, DirectAdmin, Webmin, or Plesk.
- Use a remote desktop application like PuTTY, Remote Desktop Connection (for Windows), or VNC Viewer to connect to the server if you have a VPS or dedicated server.
Once logged in, take the following steps to verify the SSL certificate:
1. Locate the SSL/TLS settings in the web hosting control panel or server configuration settings. Look for an option that says SSL/TLS or Security. For instance, cPanel SSL/TLS settings look like this:
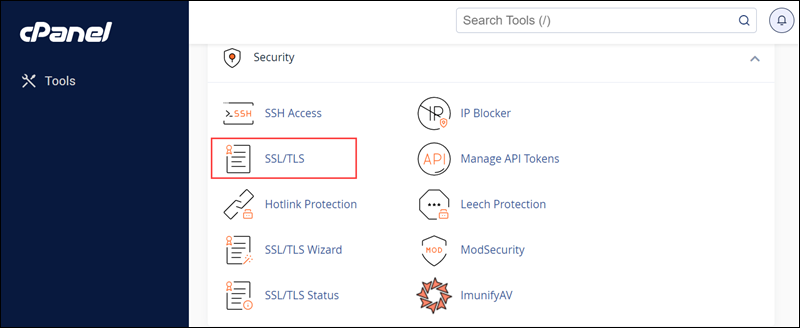
2. If the installation status is incomplete or shows errors, reinstall the certificate. The steps vary depending on the provider, but the certificate installation options are often in the same SSL/TLS panel.
Method 3: Check for a Domain Name Mismatch
A possible cause of the Cloudflare 526 error is an SSL certificate that was issued for the wrong or misspelled domain name. Log into your web hosting account or server and check the domain name associated with the SSL certificate.
1. Locate the SSL/TLS settings.
2. Check the domain name on the SSL certificate by looking for an option that displays the SSL certificate’s information.
3. Verify that the domain name on the certificate matches the website’s domain name.
Note: Steps vary depending on the hosting provider.
4. If the domain name is incorrect, contact the SSL certificate provider to fix it.
Method 4: Use a Trusted SSL Certificate
Purchase SSL certificates issued by a trusted Certificate Authority (CA) to ensure most visitors’ browsers recognize the origin server’s certificate.
Note: Using an SSL certificate from a trusted CA prevents errors and assures users that the website is authentic and safe. On the other hand, SSL certificates from untrusted CAs cause issues and are a warning sign to site visitors to leave the page immediately.
Check the list of trusted Certificate Authorities in your local browser’s settings or preferences. For example, in Chrome:
1. Open the Customize and Control Google Chrome drop-down and select Settings > Privacy and security.
2. Click Security.
3. Scroll down and click Manage device certificates under the Advanced section:
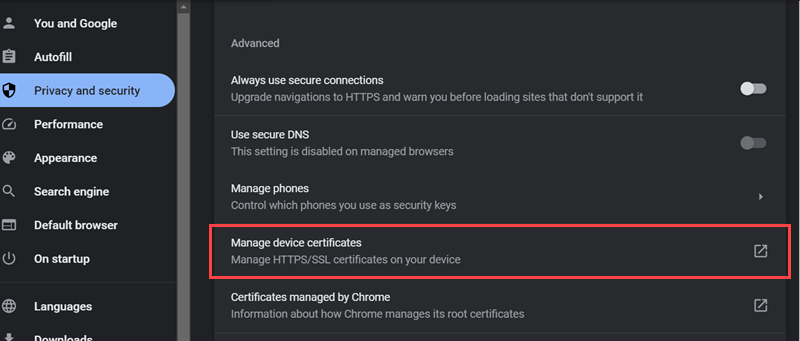
If the certificate is on the list, it is trusted by the CA. The process is similar for other browsers.
Another way to check whether the origin server has a certificate from a trusted CA is by using the curl command. For instance, run curl -v on phoenixnap.com:
curl -v https://www.phoenixnap.com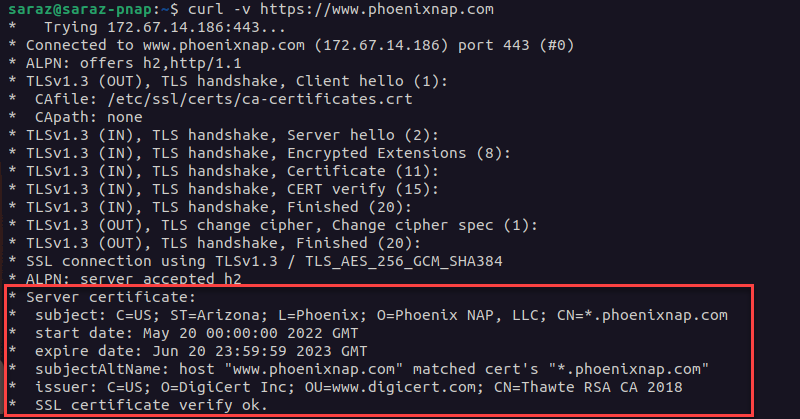
This command prints SSL certificate details at the bottom, such as the expiration date, domain name, and issuer. The output ends with the note: SSL certificate verify ok.
Alternatively, use curl -I:
curl -I https://www.phoenixnap.com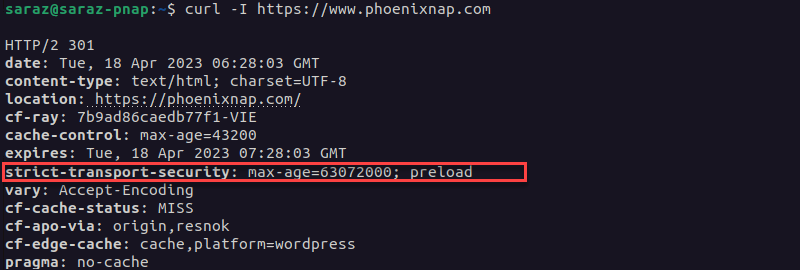
The output is extensive, and no error warnings indicate that it is a self-signed certificate. Moreover, the Strict-Transport-Security header indicates that the website uses HTTPS with HSTS (HTTP Strict Transport Security). This header only works on a server that uses a valid SSL certificate issued by a trusted CA.
However, when curl -v is used to check a domain with an untrusted certificate, the commands print error messages. For example:
curl -v https://untrusted-cert-example.com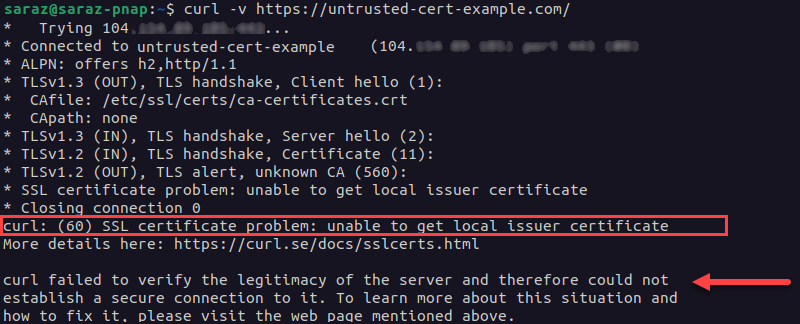
When the origins server’s certificate is not trusted, curl -v prints a warning message along with other data. The output states the specific reason the certificate is not trusted. In this example, the error message states that the SSL certificate problem exists because curl is unable to get the local issuer certificate. The certificate is considered invalid and leads to error 526.
The curl -I command gives a similar output for the same domain:
curl -I https://untrusted-cert-example.com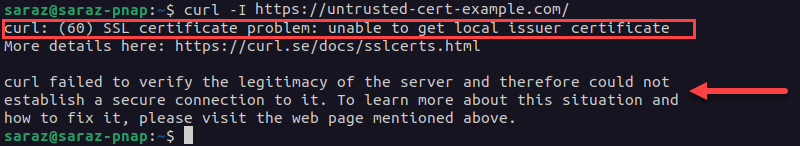
Note: Both curl -v and curl -I print the SSL certificate details useful for dealing with a 526 error. The difference is that curl -v provides more verbose output explaining the error, while curl -I only displays the error code without additional details.
If your domain’s SSL certificate was no issued by a trusted CA, follow the steps below to fix the issue:
1. Purchase an SSL certificate from a trusted CA, via a reputable web hosting provider or third-party vendor. While more expensive, these certificates provide greater security and are recognized by all major browsers.
2. Install the certificate on the website.
3. Reuse the curl -v command to verify the certificate is trusted.
Method 5: Renew SSL Certificate if Expired
A 526 error on the website sometimes indicates that the SSL certificate has expired. To check whether that is the case, run curl. For instance, verify whether the following website has an expired certificate with curl -I (curl -v also works):
curl -I https://expired-cert-example.com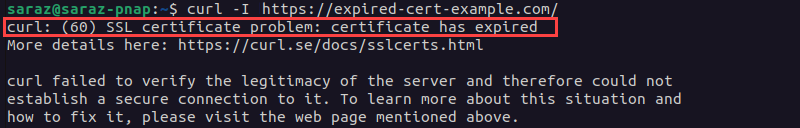
If the output shows that the certificate has expired:
1. Renew the SSL certificate based on the instructions on the certificate provider’s website.
2. Install the certificate on the website. The specific steps to do this vary depending on the hosting provider and server setup.
3. Run curl -I or curl -v to verify the renewed SSL certificate is installed correctly.
Note: Some hosting providers offer automatic renewal and installation of SSL certificates.
Method 6: Avoid Self-Signed SSL Certificates
Most web browsers do not trust self-signed SSL certificates. A self-signed SSL certificate is signed by the same entity that issued it instead of being signed by a trusted third-party Certificate Authority (CA).
When a visitor tries to access a website with a self-signed certificate, the browser shows a warning message indicating that the website is not secure.
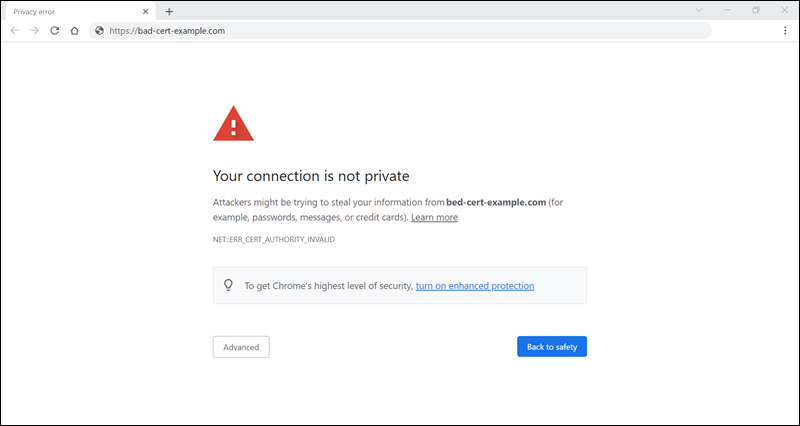
Certain browsers even prevent visitors from accessing the website altogether. In certain cases, self-signed certificates cause SSL handshake errors and other SSL-related issues, which leads to Cloudflare’s error 526.
To check whether the origin server uses a self-signed certificate, run curl with the -v argument:
curl -v https://www.bad-cert-example.com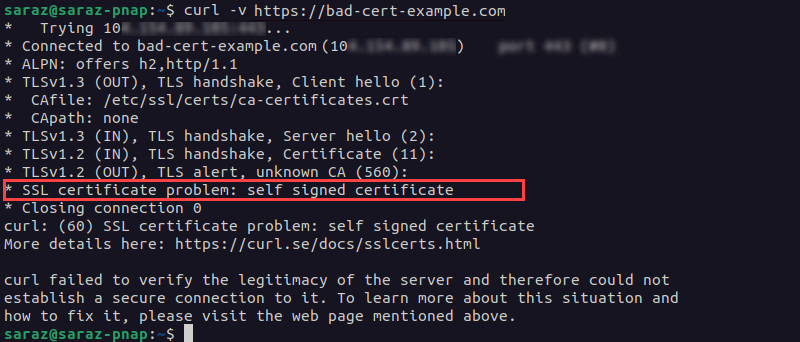
The output prints a message indicating that the certificate is self-signed. Alternatively, run curl -I to get the error message without the details:
curl -I https://www.bad-cert-example.com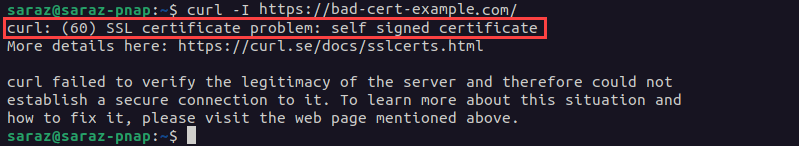
To resolve the issue, the site owner must obtain and install an SSL certificate from a trusted CA.
3. Use curl -v to verify the certificate is trusted.
Method 7: Check SSL/TLS Protocol
When a visitor tries to access a website, the browser and the website’s server communicate using a specific SSL/TLS protocol. However, if the SSL/TLS protocol used by the website does not match the protocol supported by the visitor’s browser, error 526 occurs.
To check the SSL/TLS protocol used by the website and ensure it matches the protocol supported by the visitor’s browser, follow these steps:
1. Log in to your web hosting account or server.
2. Navigate to the SSL/TLS settings section. The location of this section depends on the hosting provider and the type of hosting plan.
3. Check the SSL/TLS protocol used by the website.
4. Check the protocol supported by the visitor’s browser. For example, look up the protocol supported by a particular browser online or by review the browser documentation.
5. If the protocols do not match, update the SSL/TLS protocol to one supported by the visitor’s browser.
Save the changes and verify if error 526 has been resolved by recessing the website.
Conclusion
After reading this article, you now know how to fix Cloudflare’s error 526. If you are experiencing other issues with Cloudflare, check our articles on how to fix various Cloudflare errors.
Поставить оценку ( рейтинг )
Категория: Технологии
Просмотров: 2333
Обновлено: 17.12.2021 04:03
Продолжаем обсуждать и правильно настраивать HTTPS (SSL). На некоторых хостингах, например на FirstVDS бесплатные SSL сертификаты Let’s Encrypt могут внезапно перестать работать вообще или каждые 3 месяца автоматически не продлеваются … и т.д. Как вариант решения проблем с плохим хостингом ➡ это воспользоваться бесплатными SSL сертификатами на проекте CloudFlare.
Но и здесь нужно быть внимательным ⇨ не всё всегда идёт хорошо. Заходим в панель управления CloudFlare, в раздел SSL/TLS, чтобы включить HTTPS на сайте (на вашем домене). (Предполагается, что домен вы уже перенесли и настроили.) И выбираем один из чекбоксов:
Off (not secure) ☑ No encryption applied ➡ SSL отключен и не работает
Flexible ☑ Encrypts traffic between the browser and Cloudflare ➡ SSL между пользователем и CloudFlare. Иногда только такой вариант и работает.
Full ☑ Encrypts end-to-end, using a self signed certificate on the server ➡ SSL между пользователем и CloudFlare + до сервера. Это Наиболее распространённый вариант настройки.
Full (strict) ☑ Encrypts end-to-end, but requires a trusted CA or Cloudflare Origin CA certificate on the server ➡ SSL между пользователем и CloudFlare + до сервера, на котором должен быть установлен действующий сертификат, например CA CloudFlare Origin
И ниже ещё одна настройка SSL/TLS Recommender
Каждая из указанных настроек может создавать те или иные проблемы на сайте.
Почему на сайте перестал работать https (SSL) ?
Решение
Ошибка Error 526 Invalid SSL certificate появляется, если у вас включены:
SSL/TLS Recommender
или
Full (strict)
1 Что делать?
Просто берём и отключаем эти опции и смотрим результат. Он обычно сразу проявляется, без задержки.
И в завершение ⇔ письмо от CloudFlar с рекомендациями по включению SSL/TLS Recommender
О нашем проекте
Проект Joom-la-la предназначен для начинающих пользователей Системы управления сайтами Joomla; программистов, администраторов. Мы хотим поделиться с вами своими наработками и примерами.
Это один из сотен сайтов, сделанных нами в рамках бренда Petrovich Group. Надеемся быть вам полезными и ждём ваших комментариев
Петрович
Контактная информация
Владивосток, Россия
+ 7 423 2 *** ***
888 (@) jom-la-la.ru
petrovichgroup.ru
****
Новые публикации
Обнаружена ошибка. U…
При попытке сохранить файл configuration появляется сообщение: 0 — Обнаружена ошибка. Unable to load…
После обновления до…
После обновления Joomla до 3.6 в разделе Менеджер расширений — установить появляется Предупреж…
Серия Fatal ошибок в…
В достаточно хороших шаблонах Vina Bonnie, Vina Fashion, IncomeUp, Vina Bagshop есть проблема — они…
[Решено] Ошибка при…
Иногда, при сохранении различного контента ( материала, портфолио), в админке, возникает ошибк…
© Joom-la-la.ru . При любом использовании материалов ссылка на Joom-la-la.ru обязательна.
Все права защищены.
Cloudflare error 526 triggers when Cloudflare is unable to validate server’s SSL/TLS certificate. It normally happens with Full SSL(Strict) mode in the Cloudflare.
As a part of our Server Management Services, we help our customers to fix similar Cloudflare related errors regularly.
Let us today discuss the possible causes and fixes for this error.
What is Cloudflare error 526?
While we use Cloudflare, it involves two SSL/TLS certificates. One is provided by Cloudflare and the other by the origin server. The First certificate shown in the browser while visiting the website is the Cloudflare one. Origin server’s certificate protects data exchanges between the server and Cloudflare.
The Full (strict) mode SSL option ensures a secure connection between both the visitor – Cloudflare domain and Cloudflare – origin web server connections.
Thus if any of it fail to establish a secure connection, it triggers the 526 error as shown below.
Let us now look at the possible reasons for this error.
What are the causes of Cloudflare error 526?
As we discussed earlier, the error 526 triggers when either the certificate provided by Cloudflare or by the origin server fails to establish a secure connection. This generally happens when:
* Cloudflare cannot validate the SSL certificate at your origin web server
* Full SSL (Strict) SSL is set in the Cloudflare SSL/TLS app.
Let us now look at the steps to fix this error.
How to fix Cloudflare error 526?
Full (strict) mode is the most common reason for the 526 error. A quick fix to solve it would be to change the SSL mode to Full instead of Full (strict) from the Overview tab of Cloudflare SSL/TLS section for the particular domain.
If the issue persists even after changing the SSL mode to Full, then it would be more likely related to the origin web server’s SSL certificates. We need to verify that:
1. The certificate is not expired
2. The certificate is not revoked
3. The certificate is signed by a Certificate Authority such as GlobalSign, Verisign, GeoTrust, Comodo, etc, and is not a self-signed SSL certificate.
4. The requested domain name and hostname are in the certificate’s Common Name or Subject Alternative Name.
5. Origin web server accepts connections over port SSL port 443
6. Temporarily pause Cloudflare and cross-check the certificate with any SSL verification sites like https://www.sslshopper.com to verify that no issues exist with the origin SSL certificate.
If the origin server is using an expired, revoked or self -signed certificate, the next step to fix this error would be to install a proper SSL certificate signed by a Certificate Authority.
Likewise, it is important to have the requested domain name and hostname in the certificate’s Common Name or Subject Alternative Name. If we have added a CNAME for the hostname on Cloudflare, the Common Name or SAN may also match the CNAME target.
Cloudflare can also issue origin certificates to you on request if you don’t want to pay for or acquire one from a third-party. The 526 error should disappear after the installation of a valid certificate on the origin server and the server it accept secure (HTTPS) connections.
[Need any further assistance in fixing Cloudflare errors? – We’re available 24*7]
Conclusion
In short, Cloudflare error 526 occurs when Cloudflare is unable to validate the server’s SSL/TLS certificate. Today, we saw how our Support Engineers fix this error.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.
GET STARTED
var google_conversion_label = «owonCMyG5nEQ0aD71QM»;