IIS has a limit for the size of the files users can upload to an application. If the file size exceeds the limit, the application will throw “Error in HTTP request, received HTTP status 413 (Request Entity Too Large)” error.
The default file upload size is 49 KB (49152 bytes). The application records the log below if user tries to upload a file that is bigger than this size.
Why this issue occurs for SSL sites? The reason is that the request body must be preloaded during the SSL handshake process.
Solution
The quickest solution is to increase the upload size limit. IIS uses uploadReadAheadSize parameter in applicationHost.config and web.config files to control this limit.
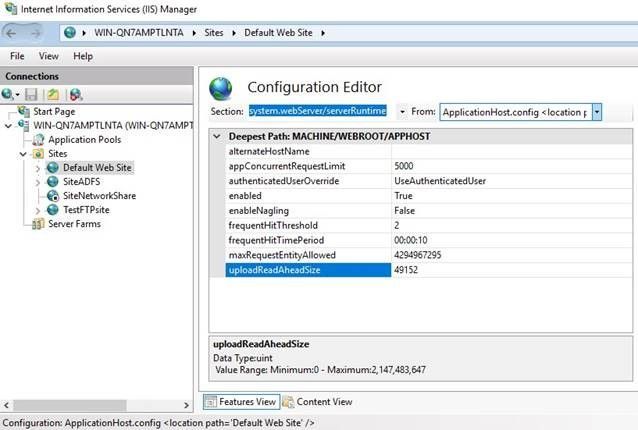
uploadReadAheadSize
Optional uint attribute.
Specifies the number of bytes that a Web server will read into a buffer and pass to an ISAPI extension or module. This occurs once per client request. The ISAPI extension or module receives any additional data directly from the client. The value must be between 0 and 2147483647.
The default value is49152.Server Runtime
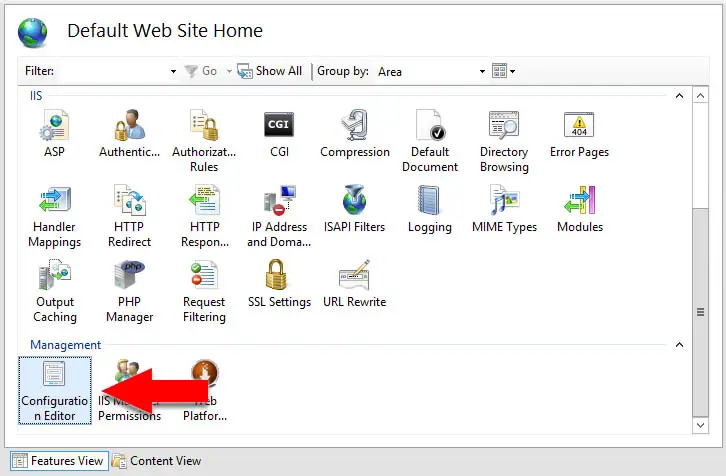
Steps to change the value of this parameter:
- Open IIS Manager
- Select the site
- Double click “Configuration Editor”
- Select
system.webServerand thenserverRuntime - Modify the
uploadReadAheadSizevalue - Click “Apply”
You may also want to change maxRequestEntityAllowed parameter. It specifies the maximum number of bytes allowed in the request body.
Note: In another case, the recommendations above didn’t work to solve 413 error. Please check this post for more information
If you have come across this article it is likely that you are trying to configure your ASP.NET application (Core, MVC, Web API, Windows Forms, WCF or other) on an IIS web server which, unlike the development web server , refuses to accept the upload of a file larger than 16kb, returning one of the following errors:
HTTP Error 413.1 — Request Entity Too Large
(413) Request Entity Too Large
Maximum request length exceeded
All these errors are related to exceeding the maximum size of an attachment — or rather, the HTTP Request sent to the server — provided by our ASP.NET application by default. These limitations have been inserted for a valid reason: receiving a file is a rather heavy operation for the server, as it engages a working thread indefinitely. For this reason, the default settings of most ASP.NET applications provide a size generally between 16k and 64k, sufficient for sending / receiving text forms but logically completely inadequate when you need to manage the upload of one or more files.
Luckily enough, solving this problem is quite simple: all we have to do is modify some sections in the application’s Web.config file to extend the limits in bytes normally provided for this type of operation. Since these settings vary according to the versions of IIS, we have entered all the versions for which it is necessary to add (or change) the indicated values.
MaxRequestLength
This value sets the maximum length limit of each Request to a maximum of 1073741824 bytes.
IIS (all versions)
|
<configuration> <system.web> <httpRuntime maxRequestLength=«1048576» /> </system.web> </configuration> |
IIS (version 7.x and higher)
In addition to the above:
|
<system.webServer> <security> <requestFiltering> <requestLimits maxAllowedContentLength=«1073741824» /> </requestFiltering> </security> </system.webServer> |
HttpBindings
If your application is a web service built with ASP.NET WFC (SOAP) or Web API / MVC (REST), you also need to add the following attributes to the bindings you intend to use. The best way to proceed is to open the Web.config for the application and, under each of them, add the following highlighted parameters:
|
<system.serviceModel> <bindings> <basicHttpBinding> <binding maxBufferPoolSize=«2147483647» maxReceivedMessageSize=«2147483647» maxBufferSize=«2147483647» > <!— binding config: security, httpTransport and more —> </binding> </basicHttpBinding> </bindings> </system.serviceModel> |
The above example has the purpose of increasing the maximum size of any upload up to 2147483647 bytes for all basicHttpBinding connections: depending on the characteristics of your web service and the protocols used, it may be necessary to add the above attributes also to the other bindings present, expected and / or supported: webHttpBinding, wsHttpBinding, customBinding and so on.
In case such addition is not enough to solve the problem, it may be necessary to also change the transferMode attribute, setting it to Streamed (the default is Buffered), and also revise the settings related to the readerQuotas, i.e. the limitations that the server gives to the SOAP clients when initiating their connection:
|
<binding maxBufferPoolSize=«2147483647» maxReceivedMessageSize=«2147483647» maxBufferSize=«2147483647» transferMode=«Streamed»> <readerQuotas maxDepth=«2000000» maxStringContentLength=«2147483647» maxArrayLength=«2147483647» maxBytesPerRead=«2147483647» maxNameTableCharCount=«2147483647»/> |
uploadReadAheadSize
In the event that all the operations described above are not sufficient to solve the problem, all that remains is to try to intervene by changing the value of the uploadReadAheadSize property: unfortunately, this setting cannot be changed at the Web.config level but must be defined directly on the machine hosting the publishing IIS Web Server.
The need to modify this setting is particularly frequent when working with the Windows Communication Foundation (WFC), the (not so much) «modern» method of managing SOAP Web Services that we have already had occasion to talk about in this article: in those scenarios, the problem generally occurs in consequence of any upload larger than 42-49kb.
Let’s get to work: access the server using Remote Desktop or physical access, then open a Command Prompt with administrator privileges and type the following command, taking care to replace YOUR_WEBSITE_NAME with the name of the website as you defined it on IIS Manager at the time of creation:
|
C:\Windows\System32\inetsrv\appcmd set config «YOUR_WEBSITE_NAME» —section:system.webServer/serverRuntime /uploadReadAheadSize:«2147483647» /commit:apphost |
In case you want to operate in a more general way, you can set this new value as a default setting for all websites with the following PowerShell command:
|
Set-WebConfigurationProperty -pspath ‘MACHINE/WEBROOT/APPHOST’ -filter «system.webserver/serverruntime» -name «uploadreadaheadsize» -value 1048576 |
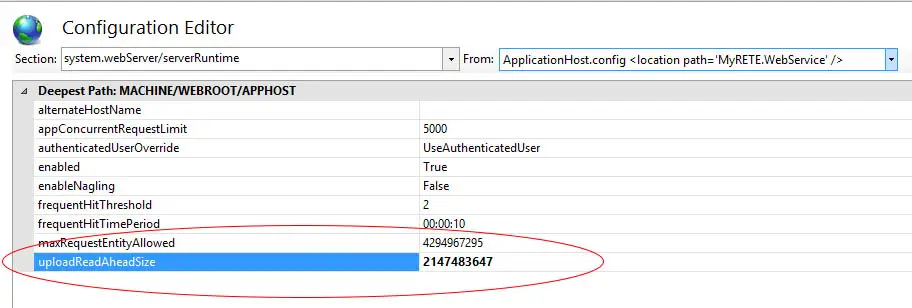
If you prefer to use the GUI, you can also configure these settings via the Configuration Editor within the Internet Information Services Manager (IISManager) tool:
Once there, select the system.webServer/serverRuntime within the top-left dropdown list, the change the uploadReadAheadSize value to your new desired standard (2147483647 in our example):
IMPORTANT: Make sure the enabled attribute is correctly set to True, otherwise the whole section will not be taken into account and IIS will use the default limitations, blocking uploads larger than 42-49kb.
That’s it for now: happy upload!
I’ve written a WCF service with .NET 4.0, which is hosted on my Windows 7 x64 Ultimate system with IIS 7.5.
One of the service methods has an ‘object’ as argument and I’m trying to send a byte[] which contains a picture.
As long as the file size of this picture is less then approx. 48KB, all goes well. But if I’m trying to upload a larger picture, the WCF service returns an error: (413) Request Entity Too Large.
So ofcourse I’ve spent 3 hours Googling the error message and every topic I’ve seen about this subject suggests raising the ‘uploadReadAheadSize’ property.
So what I’ve done is using the following commands (10485760 = 10MB):
"appcmd.exe set config -section:system.webserver/serverruntime/uploadreadaheadsize: 10485760 /commit:apphost"
"cscript adsutil.vbs set w3svc/<APP_ID>/uploadreadaheadsize 10485760"
I’ve also used IIS Manager to set the value by opening the site and going to «Configuration Editor» under Management.
Unfortunately I’m still getting the Request Entity Too Large error and it’s getting really frustrating!
So does anybody know what else I can try to fix this error?
Uwe Keim
39.6k57 gold badges175 silver badges291 bronze badges
asked Apr 12, 2012 at 11:49
1
That is not problem of IIS but the problem of WCF. WCF by default limits messages to 65KB to avoid denial of service attack with large messages. Also if you don’t use MTOM it sends byte[] to base64 encoded string (33% increase in size) => 48KB * 1,33 = 64KB
To solve this issue you must reconfigure your service to accept larger messages. This issue previously fired 400 Bad Request error but in newer version WCF started to use 413 which is correct status code for this type of error.
You need to set maxReceivedMessageSize in your binding. You can also need to set readerQuotas.
<system.serviceModel>
<bindings>
<basicHttpBinding>
<binding maxReceivedMessageSize="10485760">
<readerQuotas ... />
</binding>
</basicHttpBinding>
</bindings>
</system.serviceModel>
answered Apr 12, 2012 at 12:39
Ladislav MrnkaLadislav Mrnka
361k59 gold badges660 silver badges670 bronze badges
10
I was having the same issue with IIS 7.5 with a WCF REST Service. Trying to upload via POST any file above 65k and it would return Error 413 «Request Entity too large».
The first thing you need to understand is what kind of binding you’ve configured in the web.config. Here’s a great article…
BasicHttpBinding vs WsHttpBinding vs WebHttpBinding
If you have a REST service then you need to configure it as «webHttpBinding». Here’s the fix:
<system.serviceModel>
<bindings>
<webHttpBinding>
<binding
maxBufferPoolSize="2147483647"
maxReceivedMessageSize="2147483647"
maxBufferSize="2147483647" transferMode="Streamed">
</binding>
</webHttpBinding>
</bindings>
answered Jun 7, 2013 at 18:30
5
I had the same problem and setting the uploadReadAheadSize solved it:
http://www.iis.net/configreference/system.webserver/serverruntime
«The value must be between 0 and 2147483647.»
It is easily set it in the applicationHost.config-fle if you don’t want to do a cmd-thing.
Its located in WindowsFOLDER\System32\inetsrv\config (2008 server).
You must open it with notepad. Do a Backup of the file first.
According to the comments in config the recommended way to unlock sections is by using a location tag:
<location path="Default Web Site" overrideMode="Allow">
<system.webServer>
<asp />
</system.webServer>
</location>"
So you can write in the bottom (since it doesn’t exist before). I write maxvalue here — write your own value if you want.
<location path="THENAMEOFTHESITEYOUHAVE" overrideMode="Allow">
<system.webServer>
<asp />
<serverRuntime uploadReadAheadSize="2147483647" />
</system.webServer>
</location>
If you put it last before </configuration> for example, you know where you have it.
Hope that solves your problems. It was an SSL overhead issue for me, where too much post freezed the application, raising a (413) Request Entity Too Large error.
abatishchev
98.4k88 gold badges297 silver badges433 bronze badges
answered Mar 29, 2013 at 8:15
Tom PTom P
3093 silver badges2 bronze badges
3
I was receiving this error message, even though I had the max settings set within the binding of my WCF service config file:
<basicHttpBinding>
<binding name="NewBinding1"
receiveTimeout="01:00:00"
sendTimeout="01:00:00"
maxBufferSize="2000000000"
maxReceivedMessageSize="2000000000">
<readerQuotas maxDepth="2000000000"
maxStringContentLength="2000000000"
maxArrayLength="2000000000"
maxBytesPerRead="2000000000"
maxNameTableCharCount="2000000000" />
</binding>
</basicHttpBinding>
It seemed as though these binding settings weren’t being applied, thus the following error message:
IIS7 — (413) Request Entity Too Large when connecting to the service.
The Problem
I realised that the name="" attribute within the <service> tag of the web.config is not a free text field, as I thought it was. It is the fully qualified name of an implementation of a service contract as mentioned within this documentation page.
If that doesn’t match, then the binding settings won’t be applied!
<services>
<!-- The namespace appears in the 'name' attribute -->
<service name="Your.Namespace.ConcreteClassName">
<endpoint address="http://localhost/YourService.svc"
binding="basicHttpBinding" bindingConfiguration="NewBinding1"
contract="Your.Namespace.IConcreteClassName" />
</service>
</services>
I hope that saves someone some pain…
answered Mar 22, 2016 at 16:19
LukeLuke
22.9k31 gold badges110 silver badges194 bronze badges
3
If you’re running into this issue despite trying all of the solutions in this thread, and you’re connecting to the service via SSL (e.g. https), this might help:
http://forums.newatlanta.com/messages.cfm?threadid=554611A2-E03F-43DB-92F996F4B6222BC0&#top
To summarize (in case the link dies in the future), if your requests are large enough the certificate negotiation between the client and the service will fail randomly. To keep this from happening, you’ll need to enable a certain setting on your SSL bindings. From your IIS server, here are the steps you’ll need to take:
- Via cmd or powershell, run
netsh http show sslcert. This will give you your current configuration. You’ll want to save this somehow so you can reference it again later. - You should notice that «Negotiate Client Certificate» is disabled. This is the problem setting; the following steps will demonstrate how to enable it.
- Unfortunately there is no way to change existing bindings; you’ll have to delete it and re-add it. Run
netsh http delete sslcert <ipaddress>:<port>where<ipaddress>:<port>is the IP:port shown in the configuration you saved earlier. - Now you can re-add the binding. You can view the valid parameters for
netsh http add sslcerthere (MSDN) but in most cases your command will look like this:
netsh http add sslcert ipport=<ipaddress>:<port> appid=<application ID from saved config including the {}> certhash=<certificate hash from saved config> certstorename=<certificate store name from saved config> clientcertnegotiation=enable
If you have multiple SSL bindings, you’ll repeat the process for each of them. Hopefully this helps save someone else the hours and hours of headache this issue caused me.
EDIT: In my experience, you can’t actually run the netsh http add sslcert command from the command line directly. You’ll need to enter the netsh prompt first by typing netsh and then issue your command like http add sslcert ipport=... in order for it to work.
answered Mar 29, 2016 at 19:04
oconnerjoconnerj
3261 gold badge3 silver badges7 bronze badges
1
This helped me to resolve the problem (one line — split for readability / copy-ability):
C:\Windows\System32\inetsrv\appcmd set config "YOUR_WEBSITE_NAME"
-section:system.webServer/serverRuntime /uploadReadAheadSize:"2147483647"
/commit:apphost
answered Apr 3, 2014 at 17:51
AnasAnas
5,6225 gold badges39 silver badges71 bronze badges
1
For me, setting the uploadReadAheadSize to int.MaxValue also fixed the problem, after also increasing the limits on the WCF binding.
It seems that, when using SSL, the entire request entity body is preloaded, for which this metabase property is used.
For more info, see:
The page was not displayed because the request entity is too large. iis7
answered Oct 24, 2017 at 13:32
1
In my case, I was getting this error message because I was changed the service’s namespace and services tag was pointed to the older namespace. I refreshed the namespace and the error disapear:
<services>
<service name="My.Namespace.ServiceName"> <!-- Updated name -->
<endpoint address=""
binding="wsHttpBinding"
bindingConfiguration="MyBindingConfiguratioName"
contract="My.Namespace.Interface" <!-- Updated contract -->
/>
</service>
</services>
answered Jul 12, 2018 at 20:49
Vladimir VenegasVladimir Venegas
3,9145 gold badges25 silver badges46 bronze badges
For anyone else ever looking for an IIS WCF error 413 : Request entity to large and using a WCF service in Sharepoint, this is the information for you. The settings in the application host and web.config suggested in other sites/posts don’t work in SharePoint if using the MultipleBaseAddressBasicHttpBindingServiceHostFactory. You can use SP Powershell to get the SPWebService.Content service, create a new SPWcvSettings object and update the settings as above for your service (they won’t exist). Remember to just use the name of the service (e.g. [yourservice.svc]) when creating and adding the settings. See this site for more info https://robertsep.wordpress.com/2010/12/21/set-maximum-upload-filesize-sharepoint-wcf-service
answered Apr 7, 2015 at 21:16
In my case I had to increase the «Maximum received message size» of the Receive Location in BizTalk. That also has a default value of 64K and so every message was bounced by BizTAlk regardless of what I configured in my web.config
answered May 21, 2015 at 11:45
I’ve been able to solve this by executing a dummy call ( e.g. IsAlive returning true ) just before the request with large content on the same wcf channel/client. Apparently ssl negotation is done on the first call. So no need to increase Uploadreadaheadsize.
answered Sep 18, 2017 at 5:14
reknarekna
5,3137 gold badges45 silver badges54 bronze badges
Got a similar error on IIS Express with Visual Studio 2017.
HTTP Error 413.0 — Request Entity Too Large
The page was not displayed because the request entity is too large.
Most likely causes:
The Web server is refusing to service the request because the request
entity is too large.The Web server cannot service the request because it is trying to
negotiate a client certificate but the request entity is too large.The request URL or the physical mapping to the URL (i.e., the physical
file system path to the URL’s content) is too long.Things you can try:
Verify that the request is valid.
If using client certificates, try:
Increasing system.webServer/serverRuntime@uploadReadAheadSize
Configure your SSL endpoint to negotiate client certificates as part
of the initial SSL handshake. (netsh http add sslcert …
clientcertnegotiation=enable) .vs\config\applicationhost.config
Solve this by editing \.vs\config\applicationhost.config. Switch serverRuntime from Deny to Allow like this:
<section name="serverRuntime" overrideModeDefault="Allow" />
If this value is not edited, you will get an error like this when setting uploadReadAheadSize:
HTTP Error 500.19 — Internal Server Error
The requested page cannot be accessed because the related
configuration data for the page is invalid.This configuration section cannot be used at this path. This happens
when the section is locked at a parent level. Locking is either by
default (overrideModeDefault=»Deny»), or set explicitly by a location
tag with overrideMode=»Deny» or the legacy allowOverride=»false».
Then edit Web.config with the following values:
<system.webServer>
<serverRuntime uploadReadAheadSize="10485760" />
...
answered Feb 25, 2019 at 18:49
OgglasOgglas
62.5k37 gold badges334 silver badges420 bronze badges
1
My problem has gone after I added this:
<system.webServer>
<security>
<requestFiltering>
<requestLimits
maxAllowedContentLength="104857600"
/>
</requestFiltering>
</security>
</system.webServer>
answered Feb 16, 2021 at 23:04
Liam KernighanLiam Kernighan
2,3451 gold badge21 silver badges24 bronze badges
for issue the remote server returned an unexpected response: (413) Request Entity Too Large on WCF with Resful
please see my explain configuration
</client>
<serviceHostingEnvironment multipleSiteBindingsEnabled="false" aspNetCompatibilityEnabled="true"/>
<bindings>
<!-- this for restfull service -->
<webHttpBinding>
<binding name="RestfullwebHttpBinding"
maxBufferPoolSize="2147483647"
maxReceivedMessageSize="2147483647"
maxBufferSize="2147483647" transferMode="Streamed">
<readerQuotas
maxDepth="2147483647"
maxStringContentLength="2147483647"
maxArrayLength="2147483647"
maxBytesPerRead="2147483647" />
</binding>
</webHttpBinding>
<!-- end -->
<!-- this for Soap v.2 -->
<wsHttpBinding>
<binding name="wsBinding1" maxReceivedMessageSize="2147483647" closeTimeout="00:10:00" openTimeout="00:10:00" receiveTimeout="00:10:00" sendTimeout="00:10:00" bypassProxyOnLocal="false" transactionFlow="false" hostNameComparisonMode="StrongWildcard" maxBufferPoolSize="2147483647" messageEncoding="Text" textEncoding="utf-8" useDefaultWebProxy="true" allowCookies="false">
<readerQuotas maxDepth="2147483647" maxStringContentLength="2147483647" maxArrayLength="2147483647" maxBytesPerRead="2147483647" maxNameTableCharCount="2147483647"/>
<reliableSession ordered="true" inactivityTimeout="00:10:00" enabled="false"/>
<!--UsernameToken over Transport Security-->
<security mode="TransportWithMessageCredential">
<message clientCredentialType="UserName" establishSecurityContext="true"/>
</security>
</binding>
</wsHttpBinding>
<!-- this for restfull service -->
<!-- this for Soap v.1 -->
<basicHttpBinding>
<binding name="basicBinding1" maxReceivedMessageSize="2147483647" closeTimeout="00:10:00" openTimeout="00:10:00" receiveTimeout="00:10:00" sendTimeout="00:10:00" bypassProxyOnLocal="false" hostNameComparisonMode="StrongWildcard" maxBufferPoolSize="2147483647" messageEncoding="Text" textEncoding="utf-8" useDefaultWebProxy="true" allowCookies="false" transferMode="Streamed">
<readerQuotas maxDepth="2147483647" maxStringContentLength="2147483647" maxArrayLength="2147483647" maxBytesPerRead="2147483647" maxNameTableCharCount="2147483647"/>
<security mode="None"/>
</binding>
</basicHttpBinding>
</bindings>
<!-- end -->
<services>
<clear/>
<service name="ING.IWCFService.CitisecHashTransfer" >
<endpoint address="http://localhost:8099/CitisecHashTransfer.svc"
behaviorConfiguration="RestfullEndpointBehavior"
binding="webHttpBinding"
bindingConfiguration="RestfullwebHttpBinding"
name="ICitisecHashTransferBasicHttpBinding"
contract="ING.IWCFService.ICitisecHashTransfer" />
</service>
</services>
<behaviors>
<serviceBehaviors>
<behavior name="ServiceBehavior">
<serviceMetadata httpsGetEnabled="true"/>
<serviceDebug includeExceptionDetailInFaults="true"/>
<dataContractSerializer maxItemsInObjectGraph="2147483647"/>
<serviceCredentials>
<userNameAuthentication userNamePasswordValidationMode="Custom" customUserNamePasswordValidatorType="ING.IWCFService.IWCFServiceValidator, ING.IWCFService"/>
</serviceCredentials>
<serviceSecurityAudit auditLogLocation="Application" serviceAuthorizationAuditLevel="SuccessOrFailure" messageAuthenticationAuditLevel="SuccessOrFailure"/>
<serviceThrottling maxConcurrentCalls="1000" maxConcurrentSessions="100" maxConcurrentInstances="1000"/>
</behavior>
<behavior>
<serviceMetadata httpGetEnabled="true" httpsGetEnabled="true"/>
<serviceDebug includeExceptionDetailInFaults="true"/>
<dataContractSerializer maxItemsInObjectGraph="2147483647"/>
</behavior>
</serviceBehaviors>
<endpointBehaviors>
<behavior name="EndpointBehavior">
<dataContractSerializer maxItemsInObjectGraph="2147483647" />
</behavior>
<behavior name="RestfullEndpointBehavior">
<dataContractSerializer maxItemsInObjectGraph="2147483647" />
<webHttp/>
</behavior>
</endpointBehaviors>
</behaviors>
answered Jun 20, 2018 at 9:21
Glued a lot of responses together will ALL info I needed:
IIS Config: C:\Windows\System32\inetsrv\config\applicationHost.config (very bottom)
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
...
<location path="Default Web Site">
<system.webServer>
<security>
<access sslFlags="SslNegotiateCert" />
<!-- Max upload size in bytes -->
<requestFiltering>
<requestLimits maxAllowedContentLength="104857600" />
</requestFiltering>
</security>
</system.webServer>
</location>
</configuration>
answered Jan 10, 2022 at 15:58
KevinKevin
2,29621 silver badges22 bronze badges
Is your website showing a 413 request entity too large error? We are here to help you.
The 413 error simply means that the browser request was too large for the webserver to process.
Again, the fix for 413 request entity too large error involves modifying the size of the request body that the server accepts.
At Bobcares, we manage web servers for our customers as part of our Server Management Services.
Today, we’ll see how our Expert Engineers fix 413 errors in popular webservers like Apache, Nginx, and IIS.
Common scenarios of 413 request entity too large error
Let’s first have a quick look at the common scenarios that show the 413 error.
In general, most users experience the error while trying to upload files to the server.
For instance, in WordPress, it can happen during a theme or a plugin file upload using the WordPress dashboard. Or when a visitor tries to upload a large file, the error shows up as:
Similarly, the same error can appear while trying to restore a large WordPress backup too.
In a recent Helpdesk request, the customer reported the error as:
The upload page on my website shows the request entity is too large error. A reload will always fix it. Any clue how to prevent that issue?
What exactly causes a 413 error?
Now that we know the various scenarios of the error, we’ll see the reason for the error.
The 413 request entity too large error happens when the browser requests a very large file that the webserver cannot process. In other words, it means that the client’s HTTP request is too large for the server to handle.
For security reasons, every web server limits the size of the client request. This helps to avoid any resource abuse on the server.
For example, when any visitor tries to request a big file, it can even slow down the entire server. In many attacks, overloading the server with huge sized requests is a common method. When the request body is larger than the server allowed limit, it ends up in the 413 error.
How we fix 413 request entity too large error
The fix for 413 request entity too large error is to increase the maximum request size that a web server can process. This again varies depending on the type of web server that the website uses.
Having a decade of experience in managing various servers, let’s see how our Dedicated Engineers fix this error in different web servers.
In IIS web server
To resolve the 413 error in IIS, we increase the value of the “uploadReadAheadSize” parameter. This value determines the number of bytes that IIS will read to run the respective IIS module.
The steps for modifying applicationHost.config on an IIS7 web server are:
- In IIS7, select the website.
- Then go to the “Configuration Editor“, in the drop-down menu, select “system.webServer“
- Select “serverRuntime“.
- Find “uploadReadAheadSize” and increase its value.
- Finally, click Apply.
Solution for 413 request entity too large error in Apache
Similarly, when the website runs on an Apache webserver, we edit the value of LimitRequestBody in the configuration.
Based on the setting, we modify it in either the httpd.conf file or in a local .htaccess file inside the website.
To restrict the Apache requests beyond 50MB, we set the value as:
LimitRequestBody 52428800Then we do a config test, followed by a server reload.
service apache2 reload
Now the new value will be effective and the upload works fine.
Setting a value of 0 will allow any client request. But for security reasons, we never recommend it.
For Nginx webserver
Similarly, one of our customers came with a similar request on his Nginx server.
I have done a silly thing on my WordPress site and I need to reinstall my backup. However, I am getting an error message when I try to restore the site. The server responded with a “413 Request Entity Too Large”, please make sure that the server is not blocking our requests.
Here, we modified the value of the client_body_max_size directive in the Nginx configuration.
We opened the file at /usr/local/nginx/conf/nginx.conf and then modify the value as
# set client body size to 50M # client_max_body_size 50M;
Then we restarted the Nginx server. This fixed the 413 Request Entity Too Large error.
Cross-checking PHP limits
In some cases, even if the webserver allows the client request size, often PHP limits on the website can throw up errors. Therefore, our Dedicated Engineers always cross verify the server limits for
- upload_max_filesize
- post_max_size
- max_execution_time
And, we modify the values either using .htaccess file or php.ini file depending on the website settings.
[Looking for a fix for a 413 error on your website. We are here to help you.]
Conclusion
To sum up, the 413 Request Entity Too Large error occurs when the client browser request is too large for the webserver to handle. Today, we saw how our Support Engineers modify the value of HTTP request size limit in IIS, Apache, and Nginx.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.
GET STARTED
var google_conversion_label = «owonCMyG5nEQ0aD71QM»;
- Remove From My Forums
-
Question
-
User84152574 posted
Hi,
I have developed my web application in ASP.Net and hosted on IIS 7 running on windows 2008 and we are using SSL to make secure connection.
On few pages, I am receiving error number 413: Request entity is too large. The error happens if user opens a page and wait for few minutes before pressing any button on webpage.
When user press a button on a page after few minutes once page is loaded- the error 413 appears-though error does not appear if I do not wait and works frequently on page.
On press of button page makes asynchronous call to server using update panel.The page contains 5 tabs and each tab having a gridview control which is loaded on load event of page and gridview page size is 10 for each grid.
Each grid is having its own update panel to refresh content. No other grid content is refreshing on click of button of a grid except its own.
I am not uploading any file on this page.
The same pages works fine on HTTP but not on HTTPS.
Please help me out, its very urgent to solve this issue .
Thanks
Suresh Thakur
Answers
-
User84152574 posted
Hi Arie,
Thanks for quick reply.
When I was searching , I also come across such links saying to Reset UploadReadAheadSize value in host config file. But all of the post was giving this solution only if user is uploading a large file.
But your mentioned link http://www.developmentnow.com/g/59_2005_1_0_0_49331/IIS6-0-SSL-Breaks-down.htm has
helped me to understand that the same issue could also come when the page size itself is very large.Because the request entity body will become large in both cases.
Anyway, setting uploadReadAheadSize in applicationHost.config file on IIS7.5 has resolved my issue.
Why this is happing on SSL? : Because during client renegotiation process,the request entity body must be preloaded using
SSL preload. SSL preload will use the value of the
UploadReadAheadSize metabase property, which is used for ISAPI extensions.For more details
Thanks
Suresh Thakur
-
Marked as answer by
Tuesday, September 28, 2021 12:00 AM
-
Marked as answer by