- Remove From My Forums
-
Question
-
Win 2008R2, стоит Exchange 2010 sp3, OWA на 443 порту.
Проверил адрес OWA — куча ошибок и дырявых протоколов:
Воспользовался IISCrypto.exe для решения, там выбрал Best Practice:
Стало лучше:
Но теперь перестал работать работать RDP на сервере:
Имя журнала: System Источник: Schannel Дата: 17.07.2019 14:58:22 Код события: 36871 Категория задачи:Отсутствует Уровень: Ошибка Ключевые слова: Пользователь: система Описание: Произошла неустранимая ошибка при создании учетных данных SSL server. Внутреннее состояние ошибки: 10011. Xml события: <Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event"> <System> <Provider Name="Schannel" Guid="{1F678132-5938-4686-9FDC-C8FF68F15C85}" /> <EventID>36871</EventID> <Version>0</Version> <Level>2</Level> <Task>0</Task> <Opcode>0</Opcode> <Keywords>0x8000000000000000</Keywords> <TimeCreated SystemTime="2019-07-17T11:58:22.086063700Z" /> <EventRecordID>761100</EventRecordID> <Correlation /> <Execution ProcessID="748" ThreadID="7436" /> <Channel>System</Channel> <Security UserID="S-1-5-18" /> </System> <EventData> <Data Name="Type">server</Data> <Data Name="ErrorState">10011</Data> </EventData> </Event>В описании к программе сказано поставить для 2008 поддержку TLC 1.1 и 1.2, поставил https://support.nartac.com/article/7-will-remote-desktop-rdp-continue-to-work-after-using-iis-crypto
и на сервере и на клиенте, не помогло.Где-то советуют ещё это https://forums.iis.net/t/1233122.aspx
Это все не помогло.
С Windows 10 тоже не подключается.
Внимание вопрос, как мне отключить уязвимые протоколы и при этом оставить RDP на этом сервере?
Настройки RDP стандартные:
-
Edited by
Wednesday, July 17, 2019 12:38 PM
-
Edited by
Answers
-
Как всегда — сам спросил — сам ответил.
Оказывается все дело было в FIPS — совместимом уровне шифрования.
Программа отключила некоторые небезопасные шифры, которые требуются для FIPS и RDP отвалился.
Для возобновления работы нужно:
1. Отключить в настройках безопасности использовать FIPS совместимые алгоритмы
2. Выбрать совместимый с клиентским в уровне шифрования RDP
-
Marked as answer by
q2ker1
Thursday, July 18, 2019 2:51 PM
-
Marked as answer by
Event id 36871 error state 10013 is a system error that can occur while starting or shutting down a computer. It can also occur while installing, running or uninstalling software. This error can be caused by various factors such as improper configuration of system files, missing or corrupt system files, or a faulty hardware.
If you are experiencing this error, you can try to correct it by following the steps given below:
1. Check the system files for errors and correct them if necessary.
2. Run a virus scan to check for any corrupt or damaged files.
3. Check the hardware for any faults and replace if necessary.
4. Use the System File Checker tool to check and repair the system files.
5. Clean up the disk space to free up some disk space.
6. Disable any unnecessary startup programs and services.
7. Update the BIOS and drivers to the latest version.
8. Uninstall and reinstall the software.
9. Perform a clean install of Windows.
If none of the steps above help to solve the problem, you can try to restore the system to a previous point.
Contents
- 1 What is internal error State 10013?
- 2 How do I resolve event ID 36871?
- 3 How to fix a fatal error occurred while creating a TLS client credential?
- 4 What is Event id 36871?
- 5 How do I check my TLS settings?
- 6 How do I enable SSL and TLS?
- 7 How do I enable TLS 1.2 on Windows 10?
What is internal error State 10013?
State 10013 is an internal error that can occur in the Microsoft Windows operating system. This error can be caused by a variety of issues, including hardware failure, software conflict, or corruption of system files.
If you encounter this error, there are several steps you can take to troubleshoot it. First, make sure that your computer meets the minimum system requirements for Windows. Also, check for available updates and install any that are missing.
If the issue persists, try running a system scan to check for corrupt files or malware. If you still cannot resolve the issue, you may need to reinstall Windows.
How do I resolve event ID 36871?
Event 36871 is caused by a problem with the Virtual Machine Management Service (VMMS). To resolve this problem, you need to restart the VMMS service.
To restart the VMMS service, follow these steps:
1. Open the Services console.
2. In the Services console, locate the VMMS service.
3. Right-click the VMMS service, and then click Restart.
4. Click OK.
5. After the VMMS service restarts, try to start the virtual machine again.
How to fix a fatal error occurred while creating a TLS client credential?
A fatal error occurred while creating a TLS client credential. This can happen if the system clock is not set correctly.
To fix this, set the system clock to the correct time and try again.
What is Event id 36871?
What is Event id 36871?
Event id 36871 is a Windows event that is logged when a user signs in to a Windows 10 computer. This event is logged whenever a user signs in, whether it’s the first time they’ve signed in to the computer or not.
How do I check my TLS settings?
When you connect to a website, your web browser encrypts your communications with the site using Transport Layer Security (TLS). This helps to protect your privacy and ensure that your communications are not intercepted by third parties.
If you are having problems connecting to a website, or if you are not sure whether your web browser is using TLS encryption, you can check your TLS settings.
In most web browsers, you can check your TLS settings by opening the “Settings” or “Preferences” window and looking for the “TLS/SSL” section. This section will list the TLS/SSL ciphers and protocols that are currently enabled in your browser.
If you see any ciphers or protocols that you do not recognize, you can disable them by clicking the “Disable” button. You can also try disabling all of the ciphers and protocols and then re-enabling them one at a time to see which ones work best for you.
If you are having problems connecting to a website, you can also check the website’s SSL/TLS certificate. To do this, open the website in your web browser and look for the padlock icon in the address bar.
If the padlock icon is closed, the website is using TLS encryption. If the padlock icon is open, the website is not using TLS encryption.
If you are not sure whether a website is using TLS encryption, you can check the website’s SSL/TLS certificate by clicking on the padlock icon. This will open a window that will show the website’s SSL/TLS certificate.
The website’s SSL/TLS certificate will show the name of the website, the name of the company that issued the certificate, and the expiration date of the certificate.
How do I enable SSL and TLS?
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are both protocols that provide a secure connection between a client and server. They are often used together to provide a more secure connection.
SSL is the predecessor to TLS, and is less secure. TLS is more secure than SSL, and is now the most commonly used protocol.
To enable SSL or TLS, you must first install a certificate on your server. You can purchase a certificate from a certificate authority, or you can create your own certificate.
Once you have a certificate installed, you need to enable SSL or TLS on your server. This can be done in a number of ways, depending on the server software you are using.
If you are using Apache, you can enable SSL or TLS by editing the Apache configuration file and adding the following line:
SSLProtocol all -SSLv2 -SSLv3
If you are using Nginx, you can enable SSL or TLS by adding the following line to the Nginx configuration file:
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
If you are using IIS, you can enable SSL or TLS by editing the IIS configuration file and adding the following line:
SSLProtocols TLSv1.2
If you are using Tomcat, you can enable SSL or TLS by editing the Tomcat configuration file and adding the following line:
SSLProtocols TLSv1.2
Once you have enabled SSL or TLS, you will need to restart your server.
How do I enable TLS 1.2 on Windows 10?
The Transport Layer Security (TLS) protocol provides a secure channel between two communicating applications. It is the most widely deployed security protocol used today, and is used in all major web browsers.
TLS 1.2 is a more recent version of the TLS protocol, and offers several security benefits over earlier versions. Windows 10 includes support for TLS 1.2, but by default it is not enabled.
If you need to enable TLS 1.2 on Windows 10, you can do so by following these steps:
1. Open the Windows 10 Settings app.
2. Navigate to the System section.
3. Click on the Advanced system settings link.
4. In the Advanced tab, click on the Settings button next to the TLS 1.2 heading.
5. Select the Enabled option, and then click on the OK button.
6. Close the Advanced system settings window.
7. Restart your computer.
Now that TLS 1.2 is enabled, you will be able to use it when connecting to websites that support it.
Posted by AlanFromIT 2020-11-05T14:44:47Z
Can anybody shed any light on this repetitive error in the Windows system event viewer logs of a growing number of our machines?
Event ID 36871
Source Schannel
«A fatal error occurred while creating a TLS client credential. The internal error state is 10013.»
It’s hitting the logs several times every 20-30 seconds it seems. I can’t say I noticed until building some new W10 2004 machines, not sure if a Windows update is to blame?
Thanks in advance!
10 Replies
-
I’m getting a heck of a lot of those errors in our environment as well and have been wondering why. I do have specific schannel registry settings in place, namely SSL2 and SSL3 disabled, TLS 1.0 thru 1.3 enabled (enabled and on by default). Otherwise, no changes to cipher suites and other default schannel registry settings.
Was this post helpful?
thumb_up
thumb_down
-
Glad it’s not only me then! Let me know if you find anything
1 found this helpful
thumb_up
thumb_down
-
This is normal and can be ignored.
Event ID 36871: A Fatal Error Occurred While Creating An SSL (client or server) Credential Opens a new window
-
This is an erroneous Event log entry. You can safely ignore this message. To prevent this Event log entry, you must assign a certificate to the SMTP site.
Was this post helpful?
thumb_up
thumb_down
-
-
Thanks for the info, though in my case we don’t (or shouldn’t!) have any SMTP traffic so I’m puzzled by that. I will do some digging. That article is also W2012 server.
Was this post helpful?
thumb_up
thumb_down
-
It still applies but isn’t totally inclusive. The point is that SChannel errors are very common but meaningless unless you are having a technical problem with connections. Schannel errors show up simply because the browsers or other network connections like SQL are negotiating SSL/TLS protocols.
2 found this helpful
thumb_up
thumb_down
-
It still applies but isn’t totally inclusive. The point is that SChannel errors are very common but meaningless unless you are having a technical problem with connections. Schannel errors show up simply because the browsers or other network connections like SQL are negotiating SSL/TLS protocols.
Thanks for the info! Still doesn’t explain the sudden explosion in volume of these, but I will do some more digging next week. Thanks again.
1 found this helpful
thumb_up
thumb_down
-
The explanation is that a lot more negotiating occurs as obsolete lesser protocols are discontinued on endpoints. If you totally disabled everything lower than TLS 1.3 on your clients, then there wouldn’t be any negotiation at all. But then a lot of your connections will no longer work because the server may not support that version.
4 found this helpful
thumb_up
thumb_down
-
I’m starting to get a ton of these on multiple workstations. Users are connected to WiFi with good bandwidth, but receiving low bandwidth notifications in apps like Zoom. Checking the logs, I noticed these errors. Could this be the reason for bandwidth issues?
Was this post helpful?
thumb_up
thumb_down
-
@user350675 I don’t think this would be the cause for low bandwidth, no. Granted there will be overhead from several failed ciphersuite negotiation attempts, that would be a bigger issue up front compared to later when several sessions have negotiated and settled down on initial payloads.
I’d start with more testing on the wireless AP’s, then move to testing on laptops, such as internet speed tests at various positions.
Was this post helpful?
thumb_up
thumb_down
-
Sorry to reply to a old thread, but it’s one of the first on goggle for that error.
I had the same error on one of my server, they started appearing after I disable old crypto like SSL 2 and TLS 1.1.
The fix for me was enabling strong crypto for .net Framework. The error was coming from SQL connector, but any application that use .net framework 3.5 or 4.x can have the issue.
You need to add some registry key to enable Frameworks to use strong crypto and the OS version of TLS. If you still got the error after, that probably mean the app has hardcoded the tls version it’s using.
But the reg key are :
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v2.0.50727]
«SystemDefaultTlsVersions» = dword:00000001
«SchUseStrongCrypto» = dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319]
«SystemDefaultTlsVersions» = dword:00000001
«SchUseStrongCrypto» = dword:00000001[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v2.0.50727]
«SystemDefaultTlsVersions» = dword:00000001
«SchUseStrongCrypto» = dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319]
«SystemDefaultTlsVersions» = dword:00000001
«SchUseStrongCrypto» = dword:00000001
3 found this helpful
thumb_up
thumb_down
Windows 10: Event 36871,Schannel
Discus and support Event 36871,Schannel in Windows 10 BSOD Crashes and Debugging to solve the problem; Recently, Ive been getting these errors in the log files, regarding Schannel, Event 36871 while creating a TLS client credential, Microsoft event…
Discussion in ‘Windows 10 BSOD Crashes and Debugging’ started by JohnSalzano, Jan 26, 2020.
-
Event 36871,Schannel
Recently, Ive been getting these errors in the log files, regarding Schannel, Event 36871 while creating a TLS client credential, Microsoft event 10013. I do not have a server connected to my home network, only use Microsoft Office Outlook for mail. I have followed post regarding changing the registry settings and modifing /adding keys to the HKLM\System\CurrentcontrolSet\Control\SecurityProviders\Schannel\Protocols\SSL2.0 and dword for Client.
Flushed DNS, reset primary DNS to default of ISP. Does anyone have a clear explaination of these errors?
-
EVENT 36871, SCHANNEL
Hello,
my event viewer have been popping out and showing me this error multiples times throughout the day.
Event 36871, Schannel
A fatal error occurred while creating a TLS client credential. The internal error state is 10013.
i have no idea why the error keeps happening and getting logged.
i am a windows 10 user and i only uses the following programs, steam, google chrome and itunes.
i had used nartac software IIS Crypto and implemented best practice before (i read this solution? somewhere) and the error still keeps happening.
pls help to solve this issue, thanks
-
Windows 10 Home receiving Errors Event 36874 and 36871
I stared receiving event if 36874 and 36871 message in my event log few days ago and now I can’t run windows update
36874 An TLS 1.2 connection request was received from a remote client application, but none of the cipher suites supported by the client application are supported by the server. The TLS connection request
has failed.36871 A fatal error occurred while creating a TLS client credential. The internal error state is 10013.
I have already added TLS 1.2 in registry as given below
1. HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client\
i) DisabledByDefault set to 0
ii) Enabled Set 1
2. HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server
i) DisabledByDefault set to 0
ii) Enabled Set 1
What else I need to do resolve this issue.
-
Event 36871,Schannel
Event ID 36871 — Repeating TLS Error 10013
Each day shortly after logon, my windows 10 log fills with numerous copies of SChannel Error 36871:
«A fatal error occurred while creating a TLS client credential. The internal error state is 10013.»
I do not see any symptoms of this error that I recognize as such — failed secure connections etc.
The error occurs both before and after domain connectivity is established — as indicated by NtpClient.
Despite the error being «fatal», it repeats 2-4 times, followed by an increasing pause before repeating again.
My question is, first and foremost, what does internal error state 10013 indicate?
Event 36871,Schannel
-
Event 36871,Schannel — Similar Threads — Event 36871 Schannel
-
Schannel Event ID 36871 TLS Error
in Windows 10 Gaming
Schannel Event ID 36871 TLS Error: Hello all,I have a Windows Server 2016 that host MDT, and its been getting flooded with Schannel Error every few seconds. Error description: «A fatal error occurred while creating a TLS client credential. The internal error state is 10011.»Currently I only have TLS 1.2… -
Schannel Event ID 36871 TLS Error
in Windows 10 Software and Apps
Schannel Event ID 36871 TLS Error: Hello all,I have a Windows Server 2016 that host MDT, and its been getting flooded with Schannel Error every few seconds. Error description: «A fatal error occurred while creating a TLS client credential. The internal error state is 10011.»Currently I only have TLS 1.2… -
Error Schannel 36871
in Windows 10 BSOD Crashes and Debugging
Error Schannel 36871: I have Win 10 Pro, I have an issue when browsing Facebook. After a few minutes my PC locks up. I’ve looked at Event Viewer and it seems that the predominant Error is the 36871. Also the error shows up immediately in Event Viewer after a reboot, before logging on to Facebook…. -
Error Schannel 36871
in Windows 10 Gaming
Error Schannel 36871: I have Win 10 Pro, I have an issue when browsing Facebook. After a few minutes my PC locks up. I’ve looked at Event Viewer and it seems that the predominant Error is the 36871. Also the error shows up immediately in Event Viewer after a reboot, before logging on to Facebook…. -
Error Schannel 36871
in Windows 10 Software and Apps
Error Schannel 36871: I have Win 10 Pro, I have an issue when browsing Facebook. After a few minutes my PC locks up. I’ve looked at Event Viewer and it seems that the predominant Error is the 36871. Also the error shows up immediately in Event Viewer after a reboot, before logging on to Facebook…. -
Schannel
in Windows 10 Installation and Upgrade
Schannel: After some update on February 24, 2021 I have been getting some errors regarding TLS client credential. The event viewer states «A fatal error occurred while creating a TLS client credential. The internal error state is 10013.» The last time I ever received this according to… -
Schannel event id 36871
in Windows 10 Support
Schannel event id 36871: I hope this is the right place to ask this question. This Schannel event id 36871 started happening yesterday. It only happens when I turn my computer on after being off all night. It recorded another event this morning when I turned on my computer. What I need to know is my… -
Error: source:Schannel Event ID:36871
in Windows 10 BSOD Crashes and Debugging
Error: source:Schannel Event ID:36871: A fatal error occurred while creating a TLS client credential. The internal error state is 10013.Log Name: System
Source: Schannel
Date: 7/27/2020 3:34:14 PM
Event ID: 36871
Task Category: None
Level: Error
Keywords:
User:…
-
Schannel Event ID 36884 and 36888
in Windows 10 Support
Schannel Event ID 36884 and 36888: Okay so I’m travelling right now and decided to stop at Hilton, I decided to take my Asus ROG laptop with me. It was kinda of a pain trying to connect to their HHonor Wifi but I did however I noticed 25 errors each for event ID 36884 and 36888.Here are the logs
The…
Users found this page by searching for:
-
event id 36871
,
-
schannel 36871 windows 10
,
-
36871 schannel
,
- schannel 36871,
- windows 10 schannel error event id 36871,
- event id 36871 error state 10013,
- 36871 A Fatal error occurred when creating a TLS client credential. The internal error state is 10013,
- schannel event id 36871,
- id event 36871 windows,
- where are schannel events logged?,
- iis 10 event id 36871 source schannel,
- windows event 36871,
- event viewer 36871,
- event 36871,
- 36871

Содержание
- Windows 10 schannel ошибка 36871
- Описание ошибки Schannel 3688
- Что такое Secure Channel
- Как избавиться от ошибки Schannel 36887
- Правильный метод
- Более грубый метод
- question
- SCOM 2019: Event ID 36871 Schannel
- 3 Answers
- Как исправить ошибку SChannel 36887?
- Причины ошибки
- Создание параметра EventLogging в системном реестре
- Удаление пакета KB3161606
- Удаление антивируса ESET
- Отключение параметров использования TLS
- Schannel Events
- How to enable Schannel event logging
- Event ID 36864: The Schannel Security Package has Loaded Successfully
- Details
- Event ID 36865: A Fatal Error Occurred While Opening the Subsystem Cryptographic Module
- Details
- Event ID 36866: The Schannel Security Package Has Failed to Load
- Details
- Event ID 36867: Creating an SSL (client or server) Credential
- Details
- Event ID 36868: The SSL (client or server) Credential’s Private Key Has the Following Properties
- Details
- Event ID 36869: The SSL (client or server) Credential’s Certificate Does Not Have a Private Key Information Property Attached to it
- Details
- Event ID 36870: A Fatal Error Occurred When Attempting to Access the SSL (client or server) Credential Private Key
- Details
- Event ID 36871: A Fatal Error Occurred While Creating An SSL (client or server) Credential
- Details
- Event ID 36872: No Suitable Default Server Credential Exists on this System
- Details
- Event ID 36873: No Supported Cipher Suites Were Found When Initiating an SSL Connection
- Details
- Event ID 36874: An SSL Connection Request Was Received From a Remote Client Application, But None of the Cipher Suites Supported by the Client Application Are Supported by the Server
- Details
- Event ID 36875: The Remote Server Has Requested SSL Client Authentication, But No Suitable Client Certificate Could Be Found
- Details
- Event ID 36876: The Certificate Received From the Remote Server Has Not Validated Correctly
- Details
- Event ID 36877: The Certificate Received From the Remote Client Application Has Not Validated Correctly
- Details
- Event ID 36878: The Certificate Received From the Remote Client Application Is Not Suitable for Direct Mapping to a Client System Account, Possibly Because the Authority that is Issuing the Certificate Is Not Sufficiently Trusted
- Details
- Event ID 36879: The Certificate Received From the Remote Client Application Was Not Successfully Mapped to a Client System Account
- Details
- Event ID 36880: An SSL (client or server) Handshake Completed Successfully
- Details
- Event ID 36881: The Certificate Received From the Remote Server Has Expired
- Details
- Event ID 36882: The Certificate Received From the Remote Server Was Issued By an Untrusted Certificate Authority
- Details
- Event ID 36883: The Certificate Received From the Remote Server Has Been Revoked
- Details
- Event ID 36884: The Certificate Received From the Remote Server Does Not Contain the Expected Name
- Details
- Event ID 36885: When Asking for Client Authentication, This Server Sends a List of Trusted Certificate Authorities to the Client.
- Details
- Event ID 36886: No Suitable Default Server Credential Exists on This System
- Details
- Event ID 36887: A Fatal Alert Was Received
- Event Details
- Event ID 36888: A Fatal Alert Was Generated
Windows 10 schannel ошибка 36871
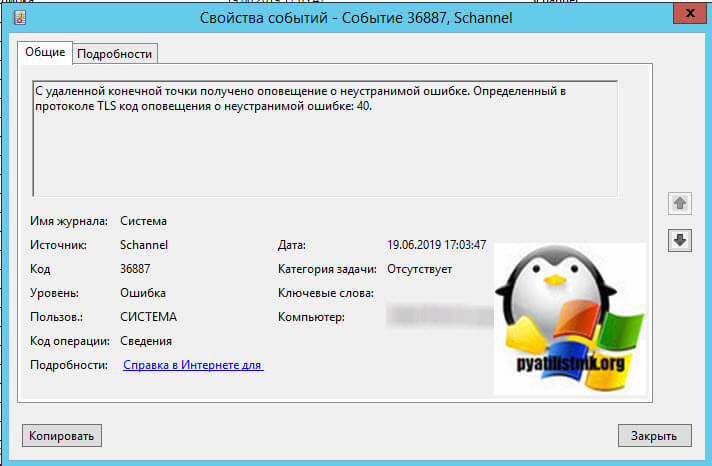
Добрый день! Уважаемые читатели и гости крупного IT блога Pyatilistnik.org. В прошлый раз мы с вами научились ремонтировать ваше оборудование в операционных системах Windows, у которых был статус ошибки «Запуск этого устройства невозможен. (код 10)». Двигаемся дальше и мы рассмотрим ситуацию, когда у вас на компьютере или сервере в журналах событий, фиксируется ошибка «Schannel ID 36887: С удаленной конечной точки получено оповещение о неустранимой ошибке. Определенный в протоколе TLS код оповещения о неустранимой ошибке: 40«. Мы рассмотрим на сколько критичны данные события и стоит ли на них обращать внимание.
Описание ошибки Schannel 3688
И так я проводил оптимизацию своей RDS фермы, кто не помнит, то в последнем посте я производил удаление неактивных портов TS. После после выполненной оптимизации я перезагрузил RDSH сервер и стал мониторить наличие новых и старых ошибок. Мое внимание привлекла ошибка из системного журнала логов Windows.
Что такое Secure Channel
Как избавиться от ошибки Schannel 36887
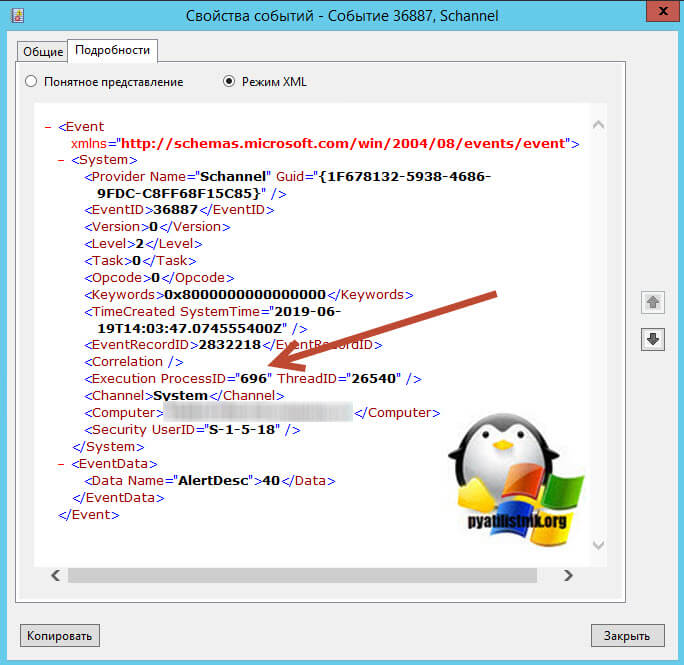
Для начала вам необходимо понять, что за процесс или приложение вызывает данную ошибку. Что мы делаем, открываем самое свежее оповещение и переходим на вкладку подробности, режим XML. Находим тут строку » Execution ProcessID =» 696 » ThreadID =» 26540 »/> «, как видим ошибку вызывает процесс с ID 696
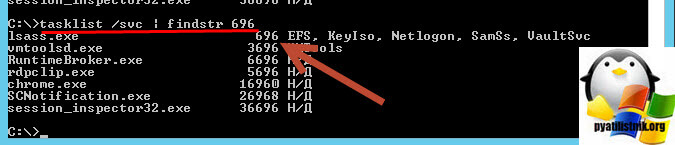
Далее нам необходимо понять, что это за процесс, для этого откройте командную строку или окно PowerShell и введите команду:
В результате мы видим отфильтрованный вывод всех процессов у которых в ID встречается 696. Оказывается, что 696 ID имеет процесс lsass.exe, системный процесс Windows, но тут может быть и другой процесс, например, geforce experience, удалив который или обновив, вы избавитесь от ошибки 36887. Но в моем случае, это lsass.exe.
Я стал искать закономерности в работе данного сервера и мне удалось ее обнаружить. Теперь я точно определил, когда происходят эти события в Schannel. Они возникают только тогда, когда я пытаюсь получить безопасное подключение к интернет-банкингу службы одного конкретного банка. Они не возникают, когда я пытаюсь получить безопасное соединение с любым другим онлайн-сервисом. Похоже, что-то пошло не так во время обмена рукопожатиями SSL/TLS. В таком случае вы можете поступить двумя путями:
Правильный метод
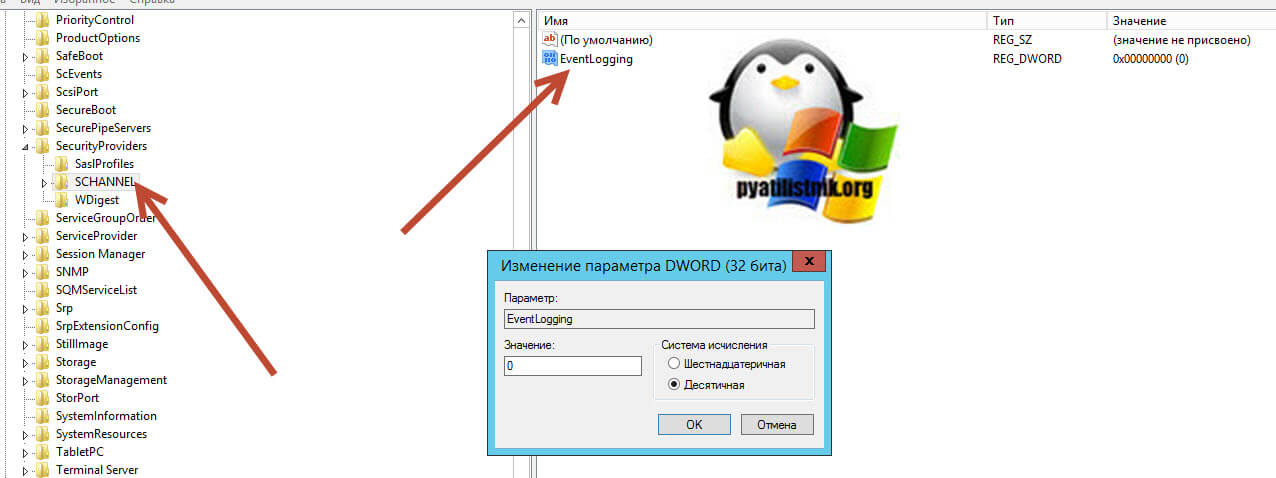
На время пока у вас идет общение с представителями клиент-банка, вы можете в реестре Windows запретить журналирование для данного события. Для этого откройте ветку:
Найдите ключ EventLogging и выставите ему значение 0.
После внесения ключа реестра, может потребоваться перезагрузка компьютера или сервера.
Более грубый метод
Чтобы отключить в системе появление событий Schannel ID 3688 вам необходимо открыть ваш браузер Internet Explorer 11 и перейти в раздел «Свойства браузера»
Далее идем на вкладку «Дополнительно», где выключаем пункт «Использовать TLS 1.2», что не совсем правильно с точки зрения безопасности. Перезапускаем браузер и пользуемся своим клиент-банком.
Источник
question
We recently moved to SCOM 2019 since then we have been receiving the below errors in the System event logs on all of the SCOM management servers.
Event ID: 36871
Event Source: Schannel
Description: A fatal error occurred while creating a TLS client credential. The internal error state is 10013.
All SCOM Management servers are running on windows server 2019.
kindly assist us on this.
3 Answers
Do you see this event in the System Log? What makes you think that it is related to SCOM? What TLS Version is currentl configured:
Can you please go over this post and see if this is also helpful:
Please check those out and I am pretty sure that those will help you.
(If the reply was helpful please don’t forget to upvote and/or accept as answer, thank you)
@kumaravelu-1265, Research and find a similar issue. in that case, these SCHANNEL 36871 events being logged are due to a configuration on the server itself.
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft.NETFramework\v4.0.30319]
«SystemDefaultTlsVersions»=dword:00000001
«SchUseStrongCrypto»=dword:00000001
Note: please do a backup before we change any registry key.
If the response is helpful, please click «Accept Answer» and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.
Источник
Как исправить ошибку SChannel 36887?
При просмотре журнала событий можно обнаружить много записей ошибки Schannel с кодом 36887. Она сопровождается сообщением, что с удаленной конечной точки получено оповещение о неустранимой ошибке 42. По сути, SChannel — это набор протоколов безопасности, который обеспечивает реализацию механизмов аутентификации и защищенной связи между вовлеченными узлами.
Причины ошибки
С ошибкой SChannel 36887 можно столкнуться по ряду причин:
Создание параметра EventLogging в системном реестре
К ошибке SChannel 36887 с кодом 42 часто приводит отсутствие раздела реестра, в котором система сможет сбрасывать подобные события. В этом случае с помощью Редактора реестра нужно создать параметр EventLogging внутри раздела SecurityProviders / Schannel. Этот способ эффективен в версиях Windows Server.
Откройте Редактор реестра командой regedit из окна Win + R. При отображении запроса от контроля учетных записей пользователей щелкните на кнопку «Да», чтобы предоставить права администратора.
В левой панели перейдите к следующей локации:
Дважды щелкните на созданном параметре и в поле Значение установите «1». Сохраните изменения на «ОК», и перезагрузите компьютер.
Теперь перейдите в журнал просмотра событий и проверьте, есть ли записи с неустранимой ошибкой SChannel 36887.
Удаление пакета KB3161606
Одной из распространенных причин, вызывающую ошибку Schannel 36887, является пакет обновления KB3161606, который отключает шифрование TLS 1.0. Этот протокол является устаревшим, но некоторые приложения все еще его используют. Чтобы обратно включить TLS 1.0, отмените обновление и заблокируйте его повторную установку.
Откройте мастера восстановления системы командой rstrui из окна Win + R.
В первом окне нажмите кнопку «Далее», затем отметьте флажком опцию показать другие точки восстановления.
Выберите снимок системы, созданный перед установкой проблемного обновления, которое привело к ошибке Schannel 36887.
В следующем окне нажмите на кнопку «Готово», чтобы запустить операцию возврата системы к предыдущему состоянию. Компьютер перезагрузится и все изменения, внесенные после создания точки восстановления, включая пакет KB3161606, будут отменены.
Если остановитесь на этом шаге Windows автоматически переустановит обновление, которое снова отключит шифрование TLS 1.0. Чтобы этого избежать, нужно скрыть это обновление.
Для этого сделайте запрос в интернете «wushowhide.diagcab», и с официального сайта Майкрософта загрузите средство для скрытия обновлений.
После двойным щелчком мыши откройте утилиту и нажмите на «Дополнительно», чтобы включить автоматическое применение исправлений.
Перейдите к следующему экрану, дождитесь завершения начального сканирования, затем щелкните на кнопку «Скрыть обновление». Установите флажок напротив обновления KB3161606 и перейдите к следующему окну. Подождите до завершения операции, затем перезапустите компьютер.
Откройте журнал просмотра событий и проверьте, есть ли новые записи с ошибкой SChannel 36887.
Удаление антивируса ESET
Как известно, антивирус ESET Antivirus Endpoint блокирует устаревший протокол шифрования TLS 1.0. Если установлены программы, которые используют старую технологию, нужно удалить ESET. Имейте в виду, что отключение в реальном времени не будет работать, поскольку блокировка применяется на уровне брандмауэра.
Если удастся исправить ошибку SChannel 36887, рассмотрите возможность установки другого антивируса или активируйте Защитника Windows.
Перейдите в раздел «Программы и компоненты» командой appwiz.cpl из окна Win + R.
Найдите в списке ESET Antivirus Endpoint, щелкните на него правой кнопкой мыши и выберите «Удалить».
После перезапустите компьютер и проверьте, решена ли проблема.
Отключение параметров использования TLS
Если обнаружили, что ошибка возникает при посещении определенных сайтов, вполне вероятно, что они не используют шифрование TLS. Чтобы это проверить, отключите опцию «Использовать TLS» в свойствах Интернета. Имейте в виду, что это решение может сделать систему уязвимой перед некоторыми угонщиками браузеров, поэтому применимо только для временного исправления.
Откройте свойства Интернета запуском команды inetcpl.cpl из диалогового окна Win +R.
На вкладке Дополнительно в разделе Безопасность снимите все флажки с опций «Использовать TLS». Примените изменения, и закройте окно.
Перезагрузите компьютер и попробуйте посетить сайты, которые вызывали неустранимую ошибку SChannel 36887 (42).
Если проблема остается, выполните проверку целостности систему командами SFC и DISM для обнаружения и восстановления поврежденных файлов Windows. Для этого откройте командную строку от имени администратора с помощью системного поиска и по очереди выполните команды:
Источник
Schannel Events
Applies To: Windows Vista, Windows Server 2008, Windows 7, Windows 8.1, Windows Server 2008 R2, Windows Server 2012, Windows 8
This topic for IT professionals lists the event details for the Secure Channel (Schannel) security support provider, and it describes the actions available to you to resolve problems.
To configure event logging for this provider, see How to enable Schannel event logging.
The Schannel Provider logs the following events to the Windows Logs\System log.
Event ID 36886: No Suitable Default Server Credential Exists on This System
How to enable Schannel event logging
You can use this registry setting to enable the logging of client certificate validation failures, which are events generated by the Schannel security support provider. Logging of client certificate validation failures is a secure channel event, and is not enabled on the server by default
The logging of rejected or discarded authentication events is enabled by default.
Registry path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
You can enable additional secure channel event logging by changing the registry key value from 1 (REG_DWORD type, data 0x00000001) to 3 (REG_DWORD type, data 0x00000003).
Event ID 36864: The Schannel Security Package has Loaded Successfully
This event is logged first whenever the Schannel.dll is successfully loaded into memory on the client computer or server. If it is unsuccessful, Event ID 36866: The Schannel Security Package Has Failed to Load will be logged.
Details
| Product | Windows operating system |
| ID | 36864 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message The Schannel security package has loaded successfully. User action No user action is required.
Event ID 36865: A Fatal Error Occurred While Opening the Subsystem Cryptographic Module
The cryptographic subsystem is composed of a software library that contains one or more independent cryptographic service providers (CSP). These providers implement cryptographic algorithms and standards. To load successfully, they must be digitally signed and the signature must be verified.
If a CSP cannot be accessed or fails to load during the authentication process, for whatever reason, the process will stop.
Details
| Product | Windows operating system |
| ID | 36865 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Error
A fatal error occurred while opening the system cryptographic subsystem cryptographic module. Operations that require the SSL or TLS cryptographic protocols will not work correctly. The error code is error code. User action
Event ID 36866: The Schannel Security Package Has Failed to Load
This event is logged when the Schannel.dll fails to load into memory on the client computer or server. If successful, Event ID 36864: The Schannel Security Package has Loaded Successfully will be logged.
Because a dependency exists between the Schannel.dll and other files, you might need to extract new copies of the following files (if other error messages indicate issues with dependent files):
Details
| Product | Windows operating system |
| ID | 36866 |
| Source | Windows operating system |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Error
Investigate whether enough memory is available to load Schannel.dll and all the dependent files.
Event ID 36867: Creating an SSL (client or server) Credential
Because authentication relies on digital certificates, certification authorities (CAs) such as Verisign or Active Directory Certificate Services are an important part of TLS/SSL. A CA is a mutually-trusted non-Microsoft company that confirms the identity of a certificate requestor (usually a user or computer), and then issues the requestor a certificate. The certificate binds the requestor’s identity to a public key, thereby creating the SSL credential for the client computer or server. This event is logged as informational only to record the progress of the TLS or SSL process.
Details
| Product | Windows operating system |
| ID | 36867 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Informational
Creating an SSL [client| server] credential. User action No user action is required.
Event ID 36868: The SSL (client or server) Credential’s Private Key Has the Following Properties
The client computer sends a client key exchange message after computing the premaster secret that uses the two random values that are generated during the client hello message and the server hello message. Before it is transmitted to the server, the premaster secret is encrypted by the public key from the server’s certificate. Both computers compute the master secret locally and derive the session key from it.
If the server can decrypt this data and complete the protocol, the client computer is assured that the server has the correct private key. This step is crucial to prove the authenticity of the server. Only the server with the private key that matches the public key in the certificate can decrypt this data and continue the protocol negotiation.
The client key exchange message includes the client computer’s protocol version and the premaster secret.
Details
| Product | Windows operating system |
| ID | 36868 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Informational
The SSL client and server credential’s private key has the following properties:
— CSP name
— CSP type
— Key name
— Key type
— Key flags
The attached data contains the certificate. User action This event is informational; no user action is required.
Event ID 36869: The SSL (client or server) Credential’s Certificate Does Not Have a Private Key Information Property Attached to it
The handshake protocols of TLS/SSL are responsible for establishing or resuming secure sessions. One of the goals of the handshake process is to authenticate the server to the client computer, and optionally, authenticate the client to the server through certificates and public or private keys.
In private (symmetric) key encryption, the same key is used to encrypt and decrypt the message. If two parties want to exchange encrypted messages securely, they must both possess a copy of the same symmetric key.
Frequently, this issue occurs when a certificate is backed up incorrectly and then later restored. This message can also indicate a certificate enrollment failure.
Details
| Product | Windows operating system |
| ID | 36869 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Error
The SSL client credential’s certificate does not have a private key information property attached to it. This most often occurs when a certificate is backed up incorrectly and then later restored. This message can also indicate a certificate enrollment failure. User action This event is informational; no user action is required.
Event ID 36870: A Fatal Error Occurred When Attempting to Access the SSL (client or server) Credential Private Key
This event can indicate that there is a problem with the server certificate on the system that is logging the event. The error is typically logged when a service (for example, LSASS on a Domain Controller) has attempted to load and verify the private and public key pair of the server certificate and that either of these operations has failed which makes the service unable to use that certificate for SSL encryption.
The handshake protocols of TLS/SSL are responsible for establishing or resuming secure sessions. One of the goals of the handshake process is to authenticate the server to the client computer, and optionally, authenticate the client to the server through certificates and public or private keys.
In private (symmetric) key encryption, the same key is used to encrypt and decrypt the message. If two parties want to exchange encrypted messages securely, they must both possess a copy of the same symmetric key.
Details
| Product | Windows operating system |
| ID | 36870 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Error
A fatal error occurred when attempting to access the SSL client credential private key. The error code returned from the cryptographic module is 0x8009030d. User action The root cause for this event can be any of the following:
Event ID 36871: A Fatal Error Occurred While Creating An SSL (client or server) Credential
This behavior is caused by the SMTP service processing an incoming EHLO command if no certificate is assigned to an SMTP site. This message is logged twice, once when the SMTP service starts, and once when the first EHLO command is received.
Simple Mail Transfer Protocol (SMTP) controls how email is transported and then delivered across the Internet to the destination server. The SMTP EHLO command enables the server to identify its support for Extended Simple Mail Transfer Protocol (ESMTP) commands.
Details
| Product | Windows operating system |
| ID | 36871 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Error
A fatal error occurred while creating an SSL server credential. User action This is an erroneous Event log entry. You can safely ignore this message. To prevent this Event log entry, you must assign a certificate to the SMTP site.
Event ID 36872: No Suitable Default Server Credential Exists on this System
This will prevent server applications that expect to make use of the system default credentials from accepting SSL connections. An example of such an application is the directory server. Applications that manage their own credentials, such as Internet Information Services (IIS), are not affected by this. This is a warning event.
This event is logged when a server application (for example, Active Directory Domain Services) attempts to perform a Secure Sockets Layer (SSL) connection, but no server certificate is found. Server certificates are either enrolled for by hand or are automatically generated by the domain’s enterprise Certification Authority (CA).
Details
| Product | Windows operating system |
| ID | 36872 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Warning
No suitable default server credential exists on this system. This will prevent server applications that expect to make use of the system default credentials from accepting SSL connections. An example of such an application is the directory server. Applications that manage their own credentials, such as Microsoft Internet Information Services (IIS), are not affected by this. User action In domains where no enterprise CA exists, this is an expected event and you can safely ignore the message.
In domains where an enterprise CA exists, you can either enroll a server certificate manually or configure the domain’s enterprise Certification Authority (CA) to automatically generate the certificate.
Event ID 36873: No Supported Cipher Suites Were Found When Initiating an SSL Connection
A cipher suite is a collection of authentication, encryption, and message authentication code (MAC) algorithms used to negotiate the security settings for a network connection using the network protocols encompassed in the Schannel security support provider.
This error message reports that the SSL connection request has failed.
The reason for this is that no supported cipher suites were found when initiating an SSL connection. This indicates a configuration problem with the client application or the installed cryptographic modules.
For information about what cipher suites are available, see Supported Cipher Suites and Protocols in the Schannel SSP.
Details
| Product | Windows operating system |
| ID | 36873 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Warning
No supported cipher suites were found when initiating an SSL connection. This indicates a configuration problem with the client application or the installed cryptographic modules. The SSL connection request has failed. User action Determine if the cipher suites supported by the server are supported by the client computer (or the application which is encountering the issue).
For more information, see How to restrict the use of certain cryptographic algorithms and protocols in Schannel.dll..
Event ID 36874: An SSL Connection Request Was Received From a Remote Client Application, But None of the Cipher Suites Supported by the Client Application Are Supported by the Server
Cypher suites are configured for the Schannel security support provider in prioritized order and certain suites are only available on specific operating system versions. For more information about this support, see Supported Cipher Suites and Protocols in the Schannel SSP.
This error message could occur when the client application, such as a web browser is using a version of the SSL protocol not supported on the server, causing the connection cannot be made.
Details
| Product | Windows operating system |
| ID | 36874 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Error
An SSL 3.0 connection request was received from a remote client application, but none of the cipher suites supported by the client application are supported by the server. The SSL connection request has failed. User action The client application is requesting an SSL connection which is not supported on the server.
Investigate the values listed under HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols.and verify that they include those versions used by the server.
Event ID 36875: The Remote Server Has Requested SSL Client Authentication, But No Suitable Client Certificate Could Be Found
In response to the client hello message, the server requested SSL client authentication. Because the client did not possess a suitable certificate, the connection process will proceed by attempting an anonymous connection. In this scenario, which has security vulnerabilities, both client and server do not get authenticated and no credentials are needed to establish an SSL connection.
The client certificate contains, among other information, what cipher suite it supports – and by extension, which protocol it supports. For more information about the use of certificates in SSL, see Schannel SSP Technical Overview.
Details
| Product | Windows operating system |
| ID | 36875 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Warning
The remote server has requested SSL client authentication, but no suitable client certificate could be found. An anonymous connection will be attempted. This SSL connection request might succeed or fail, depending on the server’s policy settings. User action This warning message requires no action.
Event ID 36876: The Certificate Received From the Remote Server Has Not Validated Correctly
Certificates are issued with a planned lifetime and explicit expiration date. A certificate may be issued for one minute, thirty years or even more. Once issued, a certificate becomes valid once its validity time has been reached, and it is considered valid until its expiration date. However, various circumstances might cause a certificate to become invalid prior to the expiration of the validity period. Such circumstances include change of name, change of association between subject and CA (for example, when an employee terminates employment with an organization), and compromise or suspected compromise of the corresponding private key.
This issue occurs because LDAP caches the certificate on the server. Although the certificate has expired and the server receives a new certificate from a CA, the server uses the cached certificate, which is expired. You must restart the server before the server uses the new certificate.
Details
| Product | Windows operating system |
| ID | 36876 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Error
The certificate received from the remote server has not validated correctly. The error code is 0Г—80090328. The SSL connection request has failed. The attached data contains the server certificate. User action You must restart the server before the server uses the new certificate.
Event ID 36877: The Certificate Received From the Remote Client Application Has Not Validated Correctly
Certificates are issued with a planned lifetime and explicit expiration date. A certificate may be issued for one minute, thirty years or even more. Once issued, a certificate becomes valid once its validity time has been reached, and it is considered valid until its expiration date. However, various circumstances might cause a certificate to become invalid prior to the expiration of the validity period. Such circumstances include change of name, change of association between subject and CA (for example, when an employee terminates employment with an organization), and compromise or suspected compromise of the corresponding private key.
Details
| Product | Windows operating system |
| ID | 36877 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Warning
The certificate received from the remote client application has not validated correctly. The error code is 0x80090325. the attached data contains the client certificate. User action The error code x80090325 indicates an untrusted certificate that was on the client.
If this was a self-signed certificate then you would need to import the certificate into the trusted root certificate store. If this certificate was issued from a Certification Authority (CA) then you will need to import the root CA certificate into the trusted root certificate store.
Event ID 36878: The Certificate Received From the Remote Client Application Is Not Suitable for Direct Mapping to a Client System Account, Possibly Because the Authority that is Issuing the Certificate Is Not Sufficiently Trusted
Because authentication relies on digital certificates, certification authorities (CAs) such as Verisign or Active Directory Certificate Services are an important part of TLS/SSL. A CA is a mutually-trusted third party that confirms the identity of a certificate requestor (usually a user or computer), and then issues the requestor a certificate. The certificate binds the requestor’s identity to a public key. CAs also renew and revoke certificates as necessary. For example, if a client is presented with a server’s certificate, the client computer might try to match the server’s CA against the client’s list of trusted CAs. If the issuing CA is trusted, the client will verify that the certificate is authentic and has not been tampered with.
When a server application requires client authentication, Schannel automatically attempts to map the certificate supplied by the client to a user account.
Details
| Product | Windows operating system |
| ID | 36878 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Warning
The certificate received from the remote client application is not suitable for direct mapping to a client system account, possibly because the authority that issuing the certificate is not sufficiently trusted. The error code is error code. The attached data contains the client certificate. User action Check to see if the CA issuing the certificate is sufficiently trusted by the client application. The data attached to the message contains the client certificate.
Event ID 36879: The Certificate Received From the Remote Client Application Was Not Successfully Mapped to a Client System Account
Because authentication relies on digital certificates, certification authorities (CAs) such as Verisign or Active Directory Certificate Services are an important part of TLS/SSL. A CA is a mutually-trusted third party that confirms the identity of a certificate requestor (usually a user or computer), and then issues the requestor a certificate. The certificate binds the requestor’s identity to a public key. CAs also renew and revoke certificates as necessary. For example, if a client is presented with a server’s certificate, the client computer might try to match the server’s CA against the client’s list of trusted CAs. If the issuing CA is trusted, the client will verify that the certificate is authentic and has not been tampered with.
When a server application requires client authentication, Schannel automatically attempts to map the certificate supplied by the client to a user account.
Details
| Product | Windows operating system |
| ID | 36879 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Warning
The certificate received from the remote client application was not successfully mapped to a client system account. The error code is error code. User action This warning message is not necessarily a fatal error, as the server application might still find the certificate acceptable.
Event ID 36880: An SSL (client or server) Handshake Completed Successfully
An SSL session always begins with an exchange of messages called the SSL handshake. The handshake allows the server to authenticate itself to the client by using public-key techniques, and then allows the client and the server to cooperate in the creation of symmetric keys used for rapid encryption, decryption, and tamper detection during the session that follows. Optionally, the handshake also allows the client to authenticate itself to the server.
Details
| Product | Windows operating system |
| ID | 36880 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Informational
An SSL [client| server] handshake completed successfully. User action No action required for this informational message.
The negotiated cryptographic parameters are protocol, cipher, cipher strength, MAC, exchange, and exchange strength.
Event ID 36881: The Certificate Received From the Remote Server Has Expired
Because authentication relies on digital certificates, certification authorities (CAs) such as Verisign or Active Directory Certificate Services are an important part of TLS/SSL. A CA is a mutually-trusted third party that confirms the identity of a certificate requestor (usually a user or computer), and then issues the requestor a certificate. The certificate binds the requestor’s identity to a public key. CAs also renew and revoke certificates as necessary. For example, if a client is presented with a server’s certificate, the client computer might try to match the server’s CA against the client’s list of trusted CAs. If the issuing CA is trusted, the client will verify that the certificate is authentic and has not been tampered with.
Details
| Product | Windows operating system |
| ID | 36881 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Error
The certificate received from the remote server has expired. The SSL connection request has failed. The attached data contains the server certificate. User action
Event ID 36882: The Certificate Received From the Remote Server Was Issued By an Untrusted Certificate Authority
Because authentication relies on digital certificates, certification authorities (CAs) such as Verisign or Active Directory Certificate Services are an important part of TLS/SSL. A CA is a mutually-trusted third party that confirms the identity of a certificate requestor (usually a user or computer), and then issues the requestor a certificate. The certificate binds the requestor’s identity to a public key. CAs also renew and revoke certificates as necessary. For example, if a client is presented with a server’s certificate, the client computer might try to match the server’s CA against the client’s list of trusted CAs. If the issuing CA is trusted, the client will verify that the certificate is authentic and has not been tampered with.
The Schannel provider creates the list of trusted certification authorities by searching the Trusted Root Certification Authorities store on the local computer. When Schannel detects a certificate that was issued by an untrusted certification authority, this error is logged.
Details
| Product | Windows operating system |
| ID | 36882 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Error
The certificate received from the remote server was issued by an untrusted certification authority. Because of this, none of the data contained in the certificate can be validated. The SSL connection request has failed. The attached data contains the server certificate. User action Remove the untrusted certificates from the Trusted Root Certification Authorities store on the local computer.
Event ID 36883: The Certificate Received From the Remote Server Has Been Revoked
Because authentication relies on digital certificates, certification authorities (CAs) such as Verisign or Active Directory Certificate Services are an important part of TLS/SSL. A CA is a mutually-trusted third party that confirms the identity of a certificate requestor (usually a user or computer), and then issues the requestor a certificate. The certificate binds the requestor’s identity to a public key. CAs also renew and revoke certificates as necessary.
All certificates in a certificate chain may be processed to verify that none of the certificates is revoked. Certificate chain validation is of course optional from an application standpoint and may not be enforced by CryptoAPI. The Windows operating system by default checks certificate revocation status via certificate revocation lists, as the CRL processing engine is the native revocation provider included with CryptoAPI. When this functionality has been invoked each certificate in the certificate chain is checked against the compared specified in the CRL published in the CRL Distribution Point (CDP) extension in the certificate. If the certificate is found to be included in the CRL, the certificate is then considered revoked.
Details
| Product | Windows operating system |
| ID | 36883 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Error
The certificate received from the remote server has been revoked. This means that the certification authority that issued the certificate has invalidated it. The SSL connection request has failed. The attached data contains the server certificate. User action
Event ID 36884: The Certificate Received From the Remote Server Does Not Contain the Expected Name
The server certificate contains the name of the server, which must match that which is contained in one of the certificates on the client computer. If the certificate name differs between the fully qualified domain name (FQDN) and the local server name, the connection will fail.
Details
| Product | Windows operating system |
| ID | 36884 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Error
The certificate received from the remote server does not contain the expected name. It is therefore not possible to determine whether we are connecting to the correct server. The server name we were expecting is servername. The SSL connection request has failed. The attached data contains the server certificate. User action
Event ID 36885: When Asking for Client Authentication, This Server Sends a List of Trusted Certificate Authorities to the Client.
The server sends a list of trusted certification authorities to the client if the following conditions are true:
The server uses the Transport Layer Security (TLS)/SSL protocol to encrypt network traffic.
Client certificates are required for authentication during the authentication handshake process.
This list of trusted certification authorities represents the authorities from which the server can accept a client certificate. To be authenticated by the server, the client must have a certificate that is present in the chain of certificates to a root certificate from the server’s list.
The Schannel provider creates the list of trusted certification authorities by searching the Trusted Root Certification Authorities store on the local computer. Every certificate that is trusted for client authentication purposes is added to the list, which is restricted by size limits. If the size of this list exceeds the maximum in bytes, the Schannel logs Warning event ID 36855. Then, Schannel truncates the list of trusted root certificates and sends this truncated list to the client computer. When the client computer receives the truncated list of trusted root certificates, the client computer might not have a certificate that exists in the chain of a trusted certificate issuer.
Details
| Product | Windows operating system |
| ID | 36885 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Warning
When asking for client authentication, this server sends a list of trusted certification authorities to the client. The client uses this list to choose a client certificate that is trusted by the server. Currently, this server trusts so many certification authorities that the list has grown too long. This list has thus been truncated. The administrator of this machine should review the certification authorities trusted for client authentication and remove those that do not really need to be trusted. User action Review the certification authorities trusted for client authentication and remove those that do not really need to be trusted.
Event ID 36886: No Suitable Default Server Credential Exists on This System
Because authentication relies on digital certificates, certification authorities (CAs) such as Verisign or Active Directory Certificate Services are an important part of TLS/SSL. A CA is a mutually-trusted third party that confirms the identity of a certificate requestor (usually a user or computer), and then issues the requestor a certificate. The certificate binds the requestor’s identity to a public key. CAs also renew and revoke certificates as necessary.
If the server’s certificate wasn not generated by a CA, one must be individually generated or installed on the server in order for the client computer to connect successfully.
Details
| Product | Windows operating system |
| ID | 36886 |
| Source | Schannel |
| Version | 6.0 |
6.2 Symbolic Name Message Type: Error
No suitable default server credential exists on this system. This will prevent server applications that expect to make use of the system default credentials from accepting SSL connections. An example of such an application is the directory server. Applications that manage their own credentials, such as Internet Information Services (IIS), are not affected by this. User action This event occurs when a server attempt to make an SSL connection but no server certificate is found. In a domain where no enterprise CA exists, this event is normal and can be safely ignored.or you can install a CA in the domain.
Event ID 36887: A Fatal Alert Was Received
The TLS alert sub-protocol uses messages to indicate a change in status or an error condition to the peer. There are a wide variety of alerts to notify the peer of both normal and error conditions. Alerts are commonly sent when the connection is closed, a message which is not valid is received, a message cannot be decrypted, or the user cancels the operation. The IETF specification, RFC 4346, contains descriptions of the closure alerts and error alerts.
This alert message indicates this computer received a TLS or SSL fatal alert message from the server it was communicating or negotiating with. The error indicates a state in the communication process, not necessarily a problem with the application. However, the cause could be how the application, such as a web browser, handled the communication.
The desktop app, using SCHANNEL_ALERT_TOKEN, generates a SSL or TLS alert to be sent to the target of a call to either the InitializeSecurityContext (Schannel) function or the AcceptSecurityContext (Schannel) function. The two alert types are warning and fatal. With a fatal error, the connection is closed immediately.
Event Details
| Product | Windows Operating |
| ID | 36887 |
| Source | Schannel |
| Version | 6.1 |
6.2 Symbolic Name SSLEVENT_RECEIVE_FATAL_ALERT
Event ID 36888: A Fatal Alert Was Generated
This event indicates that this computer (the computer that logs this event) has detected an error condition and generated a fatal alert to notify the other party about it.
The desktop app, using SCHANNEL_ALERT_TOKEN, generates a SSL or TLS alert to be sent to the target of a call to either the InitializeSecurityContext (Schannel) function or the AcceptSecurityContext (Schannel) function. The two alert types are warning and fatal. With a fatal error, the connection is closed immediately.
The TLS alert sub-protocol uses messages to indicate a change in status or an error condition to the peer. There are a wide variety of alerts to notify the peer of both normal and error conditions. Alerts are commonly sent when the connection is closed, an invalid message is received, a message cannot be decrypted, or the user cancels the operation. The IETF specification, RFC 4346, contains descriptions of the closure alerts and error alerts.
For more information about how Schannel works, see Schannel SSP Technical Overview.
Источник